You work for a small supermarket chain which has successfully operated a product inventory application for several years. It has recently purchased a data warehousing solution which provides tailorable profiling of product purchases with the aim of improving its marketing strategy. The decision has been made to host the data warehousing software and database on the same server used by the product inventory application. Based on this decision, two product risks have been cataloged:
The co-existence of both applications on the same server may introduce resource conflicts, resulting in an unacceptable impact on the functionality of the product inventory application
In the event of loss or corruption of product inventory data during transfer to the warehouse, it may not be possible to restore from back-up in the timeframe required, resulting in lost business.
Which TWO non-functional test types should be included in the test plan to mitigate both product risks?
Which of the following statements is true regarding fault seeding and fault injection tools?
The following user story has been written:
As a paying hotel guest
I want to see the charges that have been added to my bill
So that I can monitor my expenditure and know In advance how much I will have to pay when I check out
The notes that have been added to It mention that It must be possible for the guest to get a printout of the bill, see It In a variety of currencies and set a flag in the hotel's billing system against any Item that they wish to challenge.
The following acceptance criteria have been defined:
1.The user shall be able to choose from the most commonly-used currencies.
2.The application must be accessible on most mobile platforms as well as on the hotel room's smart TV.
3.The hotel manager must be notified whenever a bill item is flagged by a hotel guest.
4.End-to-end response time for any individual request submitted by a user must not exceed 7 seconds.
Applying the INVEST technique to this user story, including its acceptance criteria, which of the following statements is correct?
SELECT ONE OPTION
Within an embedded software project, the maintainability of the software is considered to be critical. It has been decided to use static analysis on each delivered software component.
Which of the following metrics is NOT a maintainability metric typically used with static analysis?
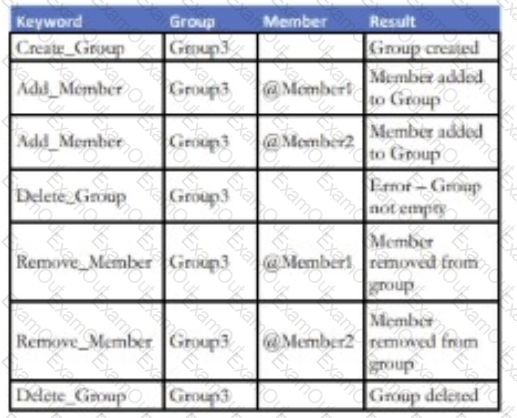
An enhancement to a Social Media application allows for the creation of new Groups. Any number of existing application members can be added to a
Group. An attempt to add a non-existing member of the application to a Group will result in an error. Members can also be removed from an existing Group.
Existing Groups can also be deleted but only if there are no current members attached to it.
Which keyword-driven input table provides an adequate test of this enhancement?
Subject to testing is a software system (COTS) for Project Administration and Control (PACS). PACS is a multi-project system for controlling the project time, e.g., in terms of scheduling and tracking, and managing the productivity of projects, e.g., in terms of effort and deliverables.
During various interviews with stakeholders the following information was gathered:
• Using PACS is not business critical. There is no impact such as high financial losses or problems to the operational continuity of an organization. Its application is not critical since the software package does not support directly the operational, or the primary, business processes of an organization. It supports (project) management in the project planning and tracking process. Of course, it will be highly annoying for users if the system “goes down” from time to time. Although this does not have a high impact for the business process as a whole, the Mean Time Between Failures (MTBF) still needs to be at a good level to be successful in the market.
• Users of PACS typically have an academic educational level, but have no prior experience with this particular type of project management software. The system will be used by a large number of users within an organization.
• The system will be used on a regular basis, e.g., several times per day by project managers and several times per week by project employees. This means that the system will not be used very intensively, often only for some data input or an information request. Its usage is not considered to be very time-critical.
• The data is recorded on-line and real-time. The system is expected to run in multiple hardware environments in various network environments. It is also expected that changes in the operational environments will happen in the upcoming period that also need to be supported.
Based on the information provided by the stakeholder, which combination of non-functional quality characteristics should you propose to test as part of your test approach?
Assume you are involved in testing a Health Insurance Calculation system.
At the main screen one can enter information for a new client. The information to be provided consists of last name, first name and date of birth. After confirmation of the information, the system checks the age of the potential new client and calculates a proposed premium.
The system also has the option to request information for an existing client, using the client’s ID number.
A keyword-driven automation approach is being used to automate most of the regression testing.
Based on the information provided, which TWO of the options provided would be the MOST LIKELY keywords for this application? (Choose two.)
A project to develop a new system has performance efficiency listed as a critical requirement. Which of the following describes how and when the Technical Test Analyst should FIRST be involved in performance test activities for the new system?
Consider the following fault attack:
• Force all possible incoming errors from the software/operating system interfaces to the application.
Which of the following is the kind of failure you are looking for when using this attack?
The following characteristics were identified during an early product risk-assessment for a software system:
• the software system needs to manage synchronization between various processes
• microcontrollers will be used that will limit product performance
• the hardware that will be used will make use of timeslots
• the number of tasks supported in parallel by the software system is large and are often highly complex.
Based on the information provided, which of the following non-functional test types is MOST appropriate to be performed?

 A group of people in a group
Description automatically generated
A group of people in a group
Description automatically generated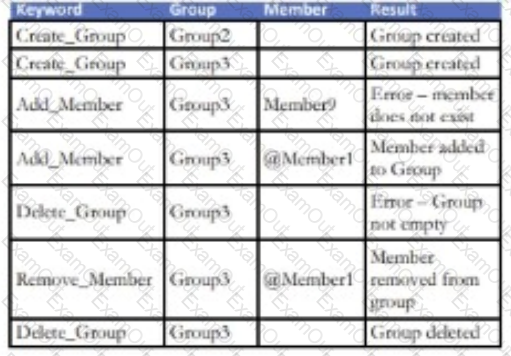 A group of people in a table
Description automatically generated
A group of people in a table
Description automatically generated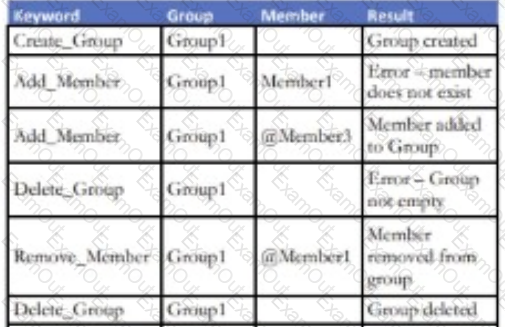 A group of people in a group
Description automatically generated
A group of people in a group
Description automatically generated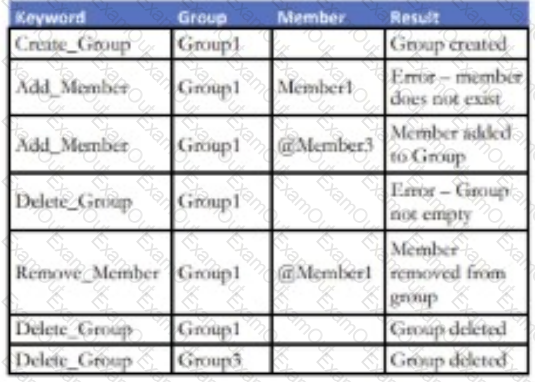 A group of people in a group
Description automatically generated
A group of people in a group
Description automatically generated