Regarding the Anti-DDoS cloud cleaning solution; which of the following statements is wrong?
An enterprise administrator configures a Web reputation website in the form of a domain name, and configures the domain name as www. abc; example. com. .
Which of the following is the entry that the firewall will match when looking up the website URL?
Which aspects of information security will be caused by unauthorized access? (multiple choice)
The security management system is only optional, and anti-virus software or anti-hacking technology can be a good defense against network threats.
What equipment do Policy Center supported servers include? (Choose 3 answers)
When a data file hits the whitelist of the firewall's anti-virus module, the firewall will no longer perform virus detection on the file.
In the following options, which of the two attacks use similar attack methods, they will generate a large number of useless response packets, occupying network bandwidth,
Consume equipment resources?
Which of the following types of attacks are DDoS attacks? 2I
The administrator has configured file filtering to prohibit internal employees from uploading development files, but internal employees can still upload development files. Which of the following is not allowed Can the reason?
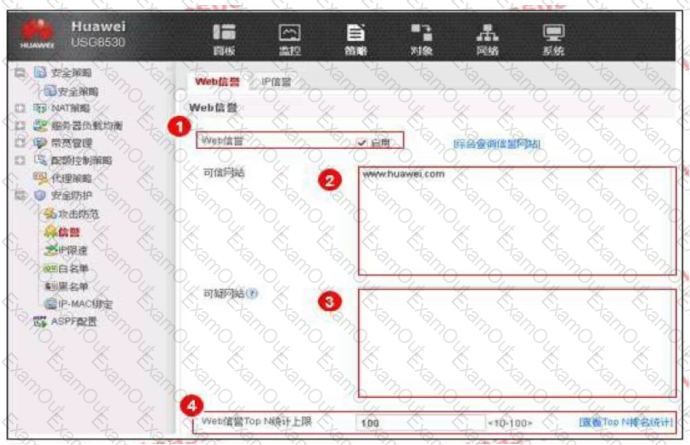
An enterprise administrator configures the Web reputation system as shown in the figure. Regarding the configuration, which of the following statements is correct?