The following figure is a schematic diagram of the detection file of the firewall and the sandbox system linkage.
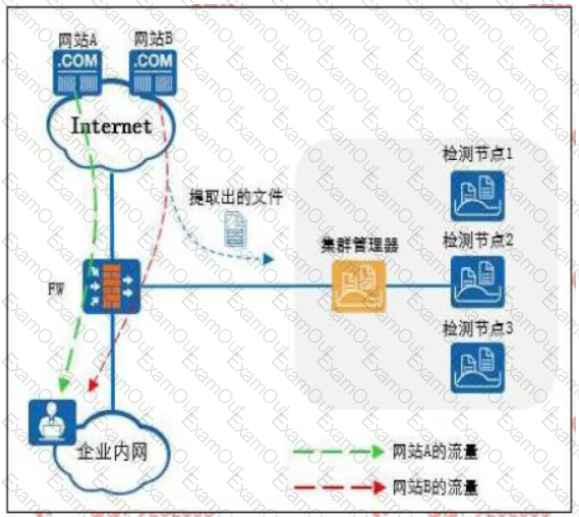
The Web reputation function is enabled on the firewall, and website A is set as a trusted website and website B is set as a suspicious website.
Which of the following statements is correct
Based on the anti-virus gateway of streaming scan, which of the following descriptions is wrong?
The whitelist rule of the firewall anti-virus module is configured as ("*example*, which of the following matching methods is used in this configuration?
URL filtering technology can perform URL access control on users according to different time objects and address objects to achieve precise management of users.
The purpose of the Internet behavior.
Which of the following options is correct for the description of the Anti DDoS system configuration?
Which of the following descriptions are correct for proxy-based anti-virus gateways? (multiple choice)
Regarding the mail content filtering configuration of Huawei USG6000 products, which of the following statements is wrong?.
Viruses can damage computer systems. v Change and damage business data: spyware collects, uses, and disperses sensitive information of corporate employees.
These malicious pastoral software seriously disturb the normal business of the enterprise. Desktop anti-disease software can solve the problem of central virus and indirect software from the overall situation.
Regarding computer viruses, which of the following options is correct?
The network-based intrusion detection system is mainly used to monitor the information of the critical path of the network in real time, listen to all packets on the network, collect data, and divide
Analyze the suspicious object, which of the following options are its main features? (multiple choices)

