Buffer overflows, Trojan horses, and backdoor attacks are all attacks at the application layer.
The network-based intrusion detection system is mainly used to monitor the information of the critical path of the network in real time, listen to all packets on the network, collect data, and divide
Analyze the suspicious object, which of the following options are its main features? (multiple choices)
Which of the following options is not a special message attack?
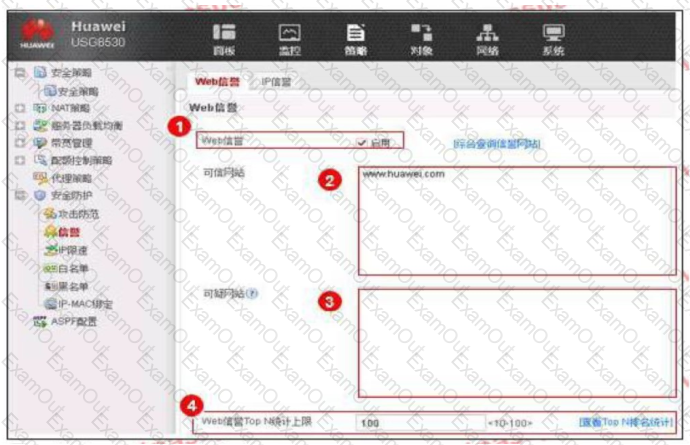
An enterprise administrator configures the Web reputation system as shown in the figure. Regarding the configuration, which of the following statements is correct?
In the Huawei USG6000 product, after creating or modifying the security configuration file, the configuration content will not take effect immediately: you need to click the "Prompt" in the upper right corner of the interface.
"Hand in" to activate.
Regarding intrusion prevention, which of the following option descriptions is wrong
For the description of the principles of HTTP Flood and HTTPS Flood blow defense, which of the following options are correct? (multiple choice)
Regarding scanning and snooping attacks, which of the following descriptions is wrong?
What content can be filtered by the content filtering technology of Huawei USG6000 products? (multiple choice)
Regarding the mail content filtering configuration of Huawei USG6000 products, which of the following statements is wrong?.

