DDoS is an abnormal packet that an attacker sends a small amount of non-traffic traffic to the attack target (usually a server, such as DNS or WEB) through the network, so that the attacked server resolves the packet when the system crashes or the system is busy.
On the web configuration page, choose System --> High Reliability --> Hot Standby and click Check for HRP Configuration Consistency. Button. The following window pops up. Which of the following configurations can solve the problem (assuming the heartbeat is added to the DMZ area)?

A user dials to the LNS of the company through L2TP over IPSec using the VPN client, and the final dialup fails. However, the debug ike all and debug l2tp all did not see any information on the LNS. The two stages of establishing ike failed. What are the reasons for the failure?
In the firewall DDoS attack defense technology, the Anti-DDoS device adopts seven layers of defense technology, and the description based on session defense is correct?
In the USG firewall, which two commands can be used to view the running status and memory/CPU usage of the device components (main control board, board, fan, power supply, etc.)?
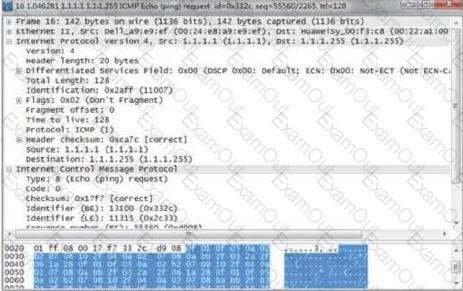
When an attack occurs, the result of packet capture on the attacked host (1.1.1.1) is as shown in the figure. What kind of attack is this attack?
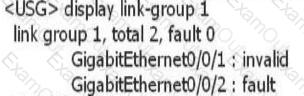
After the link-group is configured on the device, use the display link-group 1 command to obtain the following information. What information can I get?
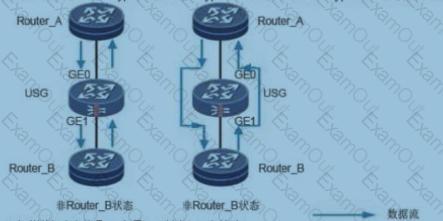
The figure shows the data flow direction of the Bypass interface in the Bypass working mode and the non-Bypass working mode. What are the following statements about the working flow of the electrical Bypass interface?
On an Eth-Trunk interface, traffic load balancing can be implemented by configuring different weights on member links.
Which of the following is incorrect about IKE V1 and IKE V2?

