Which is incorrect about the IKE DPD statement?
71. Which option is incorrect about the HTTP Flood defense principle?
The following scan snoop attacks are:
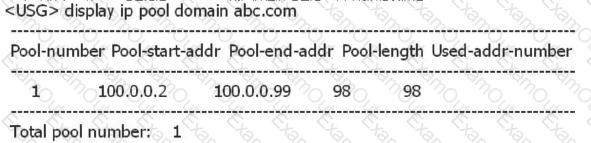
As shown below, the domain abc address pool is the address pool where the L2TP VPN user is located. What is wrong with the following statement?
With regard to the Radius agreement, what are the following statements correct?
The following figure shows the L2TP over IPSec application scenario. The client uses the pre-shared-key command to perform IPSec authentication. How should the IPSec security policy be configured on the LNS?
The hot standby and IPSec functions are combined. Which of the following statements is correct?
Which is the correct packet encapsulation order for L2TP over IPSec?
The default interval for sending VGMP hello packets is 1 second. That is, when the hello packet sent by the peer is not received within the range of three hello packets, the peer is considered to be faulty. Master status.
Which of the following statements is true for virtual service technology?

