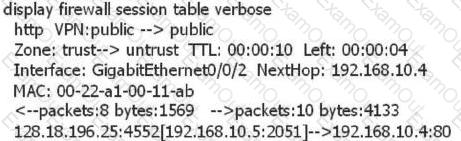
Based on the following information analysis on the firewall, which of the following options are correct?
The attacker sends a large number of invite messages to the SIP server, causing the SIP server to refuse service. Which layer of the OSI model is this attack based on?
The ACK flood attack uses a botnet to send a large number of ACK packets, which impacts the network bandwidth and causes network link congestion. If the number of attack packets is large, the server processing performance is exhausted, thus rejecting normal services. Under the Huawei Anti-DDoS device to prevent this attack, compare the two processing methods - strict mode and basic mode, what is correct?
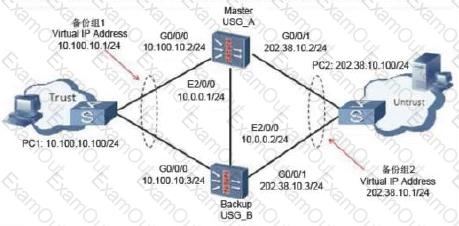
The enterprise network is as shown in the figure. On the USG_A and USG_B, hot standby is configured, and USG_A is the master device. The administrator wants to configure SSL VPN on the firewall so that branch employees can access the headquarters through SSL VPN. Which virtual gateway address should the SSL VPN be?
Which of the following security services can a secure multi-instance provide for a virtual firewall?
The topology diagram of the BFD-bound static route is as follows: The administrator has configured the following on firewall A: [USG9000_A] bfd [USG9000_A-bfd] quit [USG9000_A] bfd aa bind peer-ip 1.1.1.2 [USG9000_A- Bfd session-aa] discriminator local 10 [USG9000_A-bfd session-aa] discriminator remote 20 [USG9000_A-bfd session-aa] commit [USG9000_A-bfd session-aa] quit What are the correct statements about this segment?
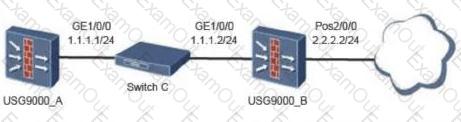
The branch firewall of an enterprise is configured with NAT. As shown in the figure, USG_B is the NAT gateway. The USG_B is used to establish an IPSec VPN with the headquarters. Which parts of the USG_B need to be configured?
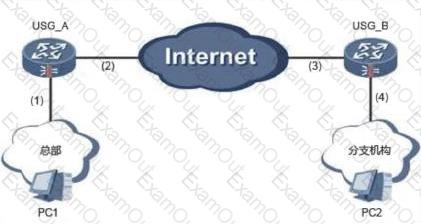
What are the three elements of an abnormal flow cleaning solution?
According to the dual-system hot backup network diagram, what are the correct descriptions in the following dual-system hot backup preemption function?
When using the SSL VPN client to start the network extension, the prompt "Connection gateway failed", what are the possible reasons for the failure?

