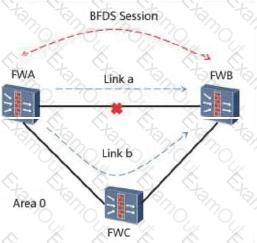
As shown in the following figure, the BFD for OSPF network is as follows: 1. OSPF is running between the three devices: FW_A, FW_B, and FW_C. The neighbors are in the FULL state. The association between BFD and OSPF is complete. BFD is complete. To establish a BFD session, the following instructions are correct?
Site to Site IPSec VPN negotiation failed. Which of the following should be checked? 1. Network connectivity issues; 2. View the establishment of IKE phase 1 security associations and related configurations; 3. View the establishment of IKE phase 2 security associations and related configurations; 4. See if the security ACLs at both ends mirror each other.
In the dual-system hot backup, when the slave does not receive the hello packet of the HRP sent in the HRP hello packet period, the slave device is considered to be faulty.
If the IPSec policy is configured in the policy template and sub-policy mode, the firewall applies the policy template first and then applies the sub-policy.
What are the correct descriptions of IPSec and IKE below?
Two USG firewalls failed to establish an IPSec VPN tunnel through the NAT traversal mode. Run the display ike sa command to view the session without any UDP 500 session. What are the possible reasons?
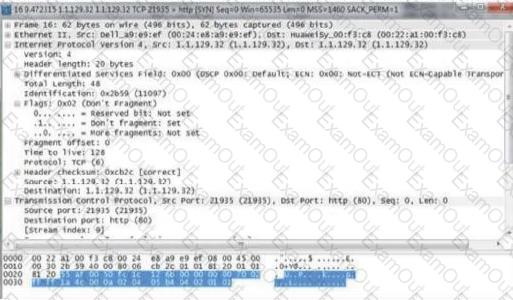
When an attack occurs, many packets are found on the attacked host (1.1.129.32) as shown in the figure. According to the analysis of the attack, what kind of attack is this attack?
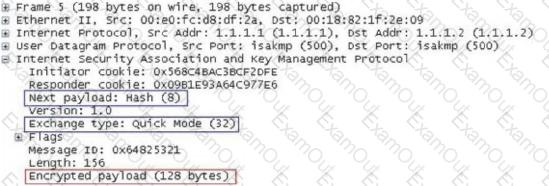
In the IKE V1 pre-shared key mode, what is the main role of the data captured in the following figure?
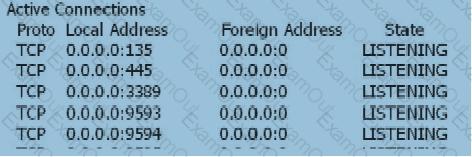
When the user's SSL VPN has been successfully authenticated, the user cannot access the Web-link resource. On the Web server, view the information as follows: netstat -anp tcp With the following information, which of the following statements is correct?
The dual-system hot backup load balancing service interface works at Layer 3, and the upstream and downstream routers are connected to each other. The two USG devices are active and standby. Therefore, both the hrp track master and the hrp track slave must be configured on the morning service interface.

