Which of the following states indicates that a BFD session has been successfully established?
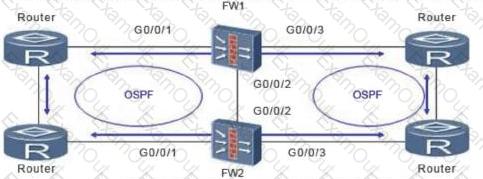
As shown in the figure, the firewall is dual-system hot standby. In this networking environment, all service interfaces of the firewall work in routing mode, and OSPF is configured on the upper and lower routers. Assume that the convergence time of OSPF is 30s after the fault is rectified. What is the best configuration for HRP preemption management?
The firewall device defends against the SYN Flood attack by using the technology of source legality verification. The device receives the SYN packet and sends the SYN-ACK probe packet to the source IP address host in the SYN packet. If the host exists, it will Which message is sent?
What is the correct statement about the binding of local users to VPN instances?
According to the capture of the victim host, what kind of attack is this attack?
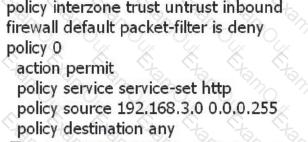
The PC A in the Trust zone is 192.168.3.1. You cannot access the Internet server in the Untrust zone. The configuration between the Trust zone and the Untrust zone is as follows. What are the most likely causes of the following faults?
L2TP is a tunneling protocol set up for transparent transmission of PPP packets between users and enterprise servers. Which of the following features are included?
The following are traffic-type attacks.
The ip-link sends a probe packet to the specified IP address. By default, after 3 probe failures, the link to this IP address is considered faulty.
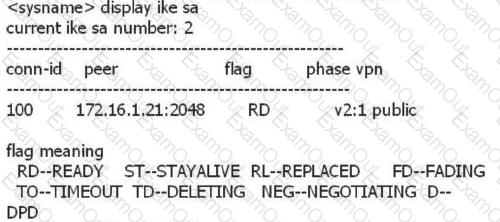
Run the display ike sa command to check the IKE SA information. The following statement is correct?