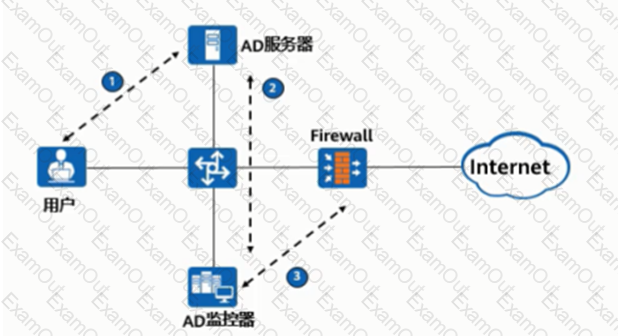
As shown in the figure, the process of AD single sign-on (querying the security log mode of AD server), please match the corresponding operation process.
Please order the following steps in the PKI life cycle correctly, 1. Issued, 2. storage, 3. Update, 4. verify[fill in the blank]*
The network environment is becoming more and more complex, and network security incidents occur frequently. While accelerating the construction of informatization, enterprises must not only resist external attacks, but also prevent internal management personnel from being involved in data leakage and operation and maintenance accidents due to operational errors and other issues. Which of the following options might reduce operational risk?
Which of the following is not an advantage of symmetric encryption algorithms?
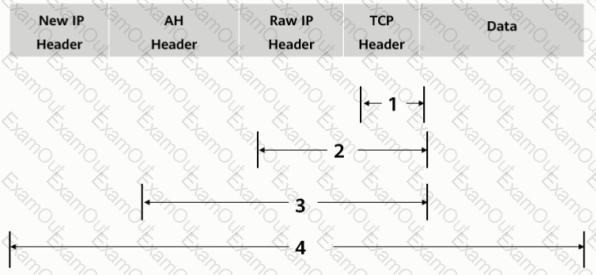
As shown in the figure, what is the authentication range of the AH protocol in tunnel mode?
Which of the following descriptions about the main implementation of single sign-on is wrong? ( )[Multiple choice]*
Which of the following attack methods is to construct special SQL statements and submit sensitive information to exploit program vulnerabilities
The trigger modes of the built-in Portal authentication in the firewall include pre-authentication and ____ authentication[fill in the blank]*
What is correct about the following description of device management in the operating system?
What is the security level of the Untrust zone in Huawei firewalls?