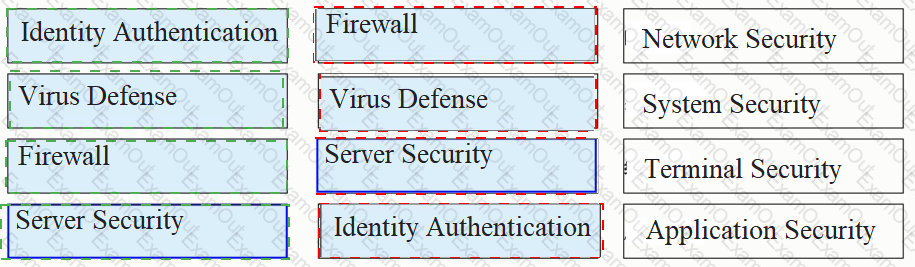
Please classify the following security defenses into the correct classification.
When using passive mode to establish an FTP connection, the control channel uses port 20 and the data channel uses port 21. ( )[Multiple choice]*
Which of the following are the backup items that HRP can provide?
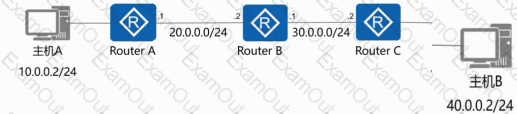
As shown in the figure, the administrator needs to test the network quality of the 20.0.0/24 CIDR block to the 40.0.0/24 CIDR block on Device B, and the device needs to send large packets for a long time to test the network connectivity and stability.
DES is a stream encryption algorithm, because the cipher capacity is only 56 bits, so it is not enough to deal with the weakness of insufficient security, and later 3DES was proposed.
Please match the following information security risks to information security incidents one by one.[fill in the blank]*
physical security riskEnterprise server permissions are loosely set
Information Security Management RiskInfected Panda Burning Incense
Information Access RiskFire destroyed equipment in computer room
application riskTalk to people about leaking company secrets
Which of the following is the numbering range of Layer 2 ACLs?
Which of the following operating modes does NTP support?
In the Linux system, which of the following is the command to query the P address information? ( )[Multiple choice]*
In cases where some configurations alter existing session table entries and want them to take effect immediately, you can regenerate the session table by clearing the session table information. All session table information can be cleared by executing the _____firewall session table command.