Drag the phases of the cybersecurity emergency response on the left into the box on the right, and arrange them from top to bottom in the order of execution.[fill in the blank]*

The following description of the AH protocol in IPSec VPN, which one is wrong?
The RADIUS protocol specifies how to pass user information, billing information, authentication and billing results between the NAS and the RADIUS server, and the RADIUS server is responsible for receiving the user's connection request, completing the authentication, and returning the result to the NAS.
Which of the following descriptions of single sign-on is correct?
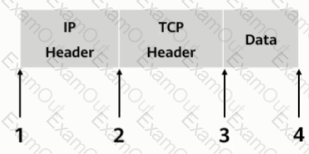
As shown, in transmission mode, which of the following locations should the AH header be inserted in?
The following description of the construction of a digital certificate, which item is wrong
Which of the following is not a type of Windows log event?

