Which two components are part of onboarding a secure web gateway (SWG) endpoint? (Choose two)
Refer to the exhibits.
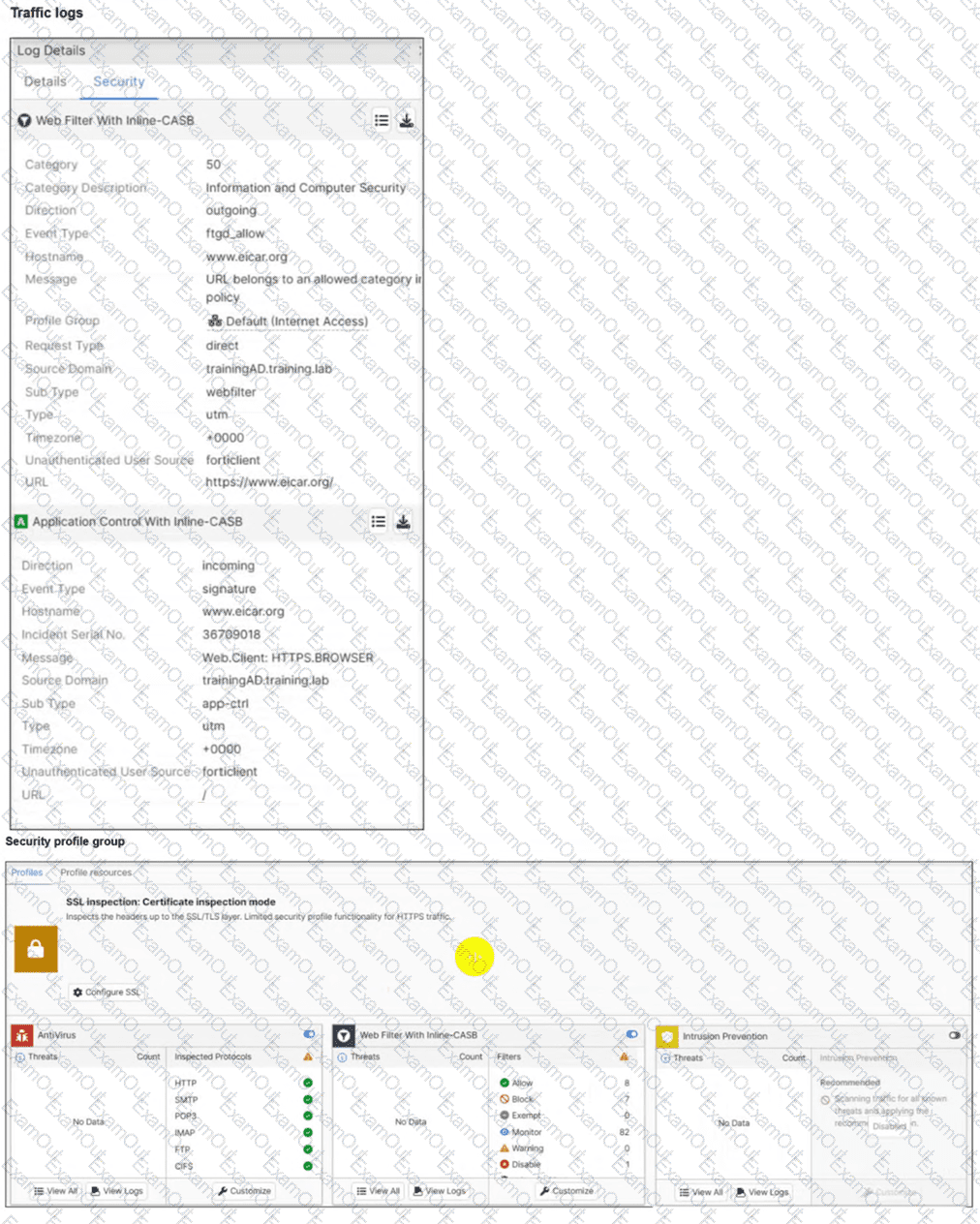
A FortiSASE administrator has configured an antivirus profile in the security profile group and applied it to the internet access policy. Remote users are still able to download the eicar.com-zip file from https://eicar.org.
Which configuration on FortiSASE is allowing users to perform the download? (Choose one answer)
Refer to the exhibits.
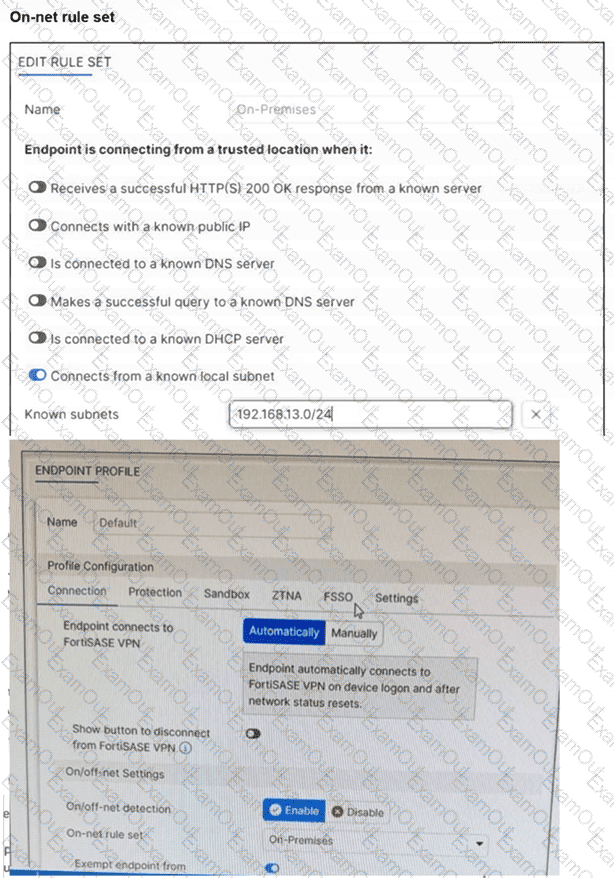
An endpoint is assigned an IP address of 192.168.13.101/24. Which action will be run on the endpoint? (Choose one answer)
When viewing the daily summary report generated by FortiSASE. the administrator notices that the report contains very little data. What is a possible explanation for this almost empty report?
A customer needs to implement device posture checks for their remote endpoints while accessing the protected server. They also want the TCP traffic between the remote endpoints and the protected servers to be processed by FortiGate.
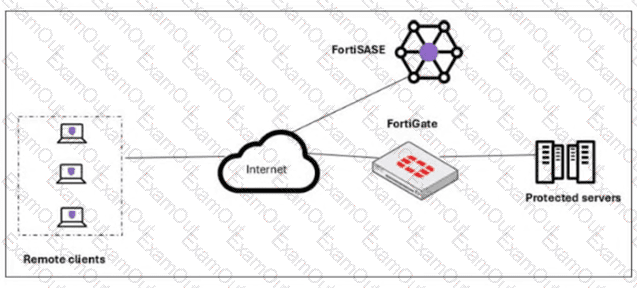
In this scenario, which two setups will achieve these requirements? (Choose two answers)
An organization wants to block all video and audio application traffic but grant access to videos from CNN Which application override action must you configure in the Application Control with Inline-CASB?
What is the maximum number of Secure Private Access (SPA) service connections (SPA hubs) supported in the SPA use case? (Choose one answer)
Refer to the exhibit.
In the user connection monitor, the FortiSASE administrator notices the user name is showing random characters. Which configuration change must the administrator make to get proper user information?
Which three traffic flows are supported by FortiSASE Secure Private Access (SPA)? (Choose three answers)
Which two benefits come from integrating SoCaaS with FortiSASE? (Choose two answers)

