Refer to the exhibit.
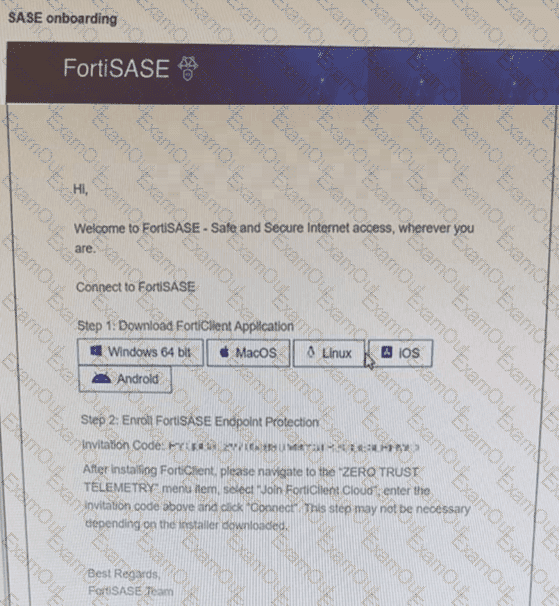
Which two statements about the onboarding process shown in the exhibit are true? (Choose two answers)
Which two statements about FortiSASE Geofencing with regional compliance are true? (Choose two answers)
Refer to the exhibits.
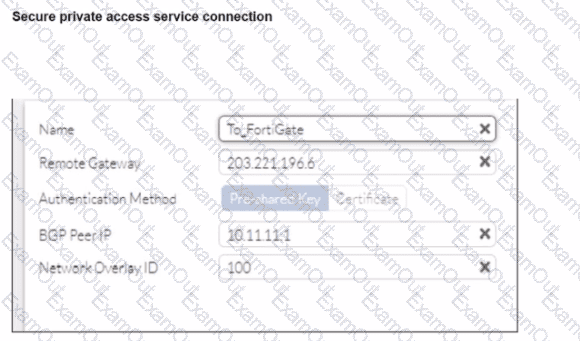
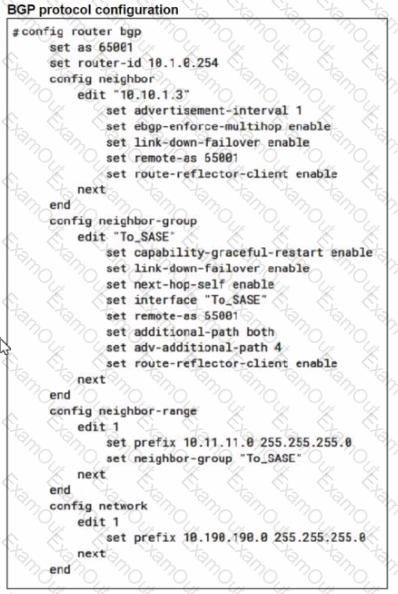
A FortiSASE administrator is trying to configure FortiSASE as a spoke to a FortiGate hub. The VPN tunnel does not establish
Based on the provided configuration, what configuration needs to be modified to bring the tunnel up?
What are two benefits of deploying secure private access (SPA) with SD-WAN? (Choose two answers)
Refer to the exhibits.
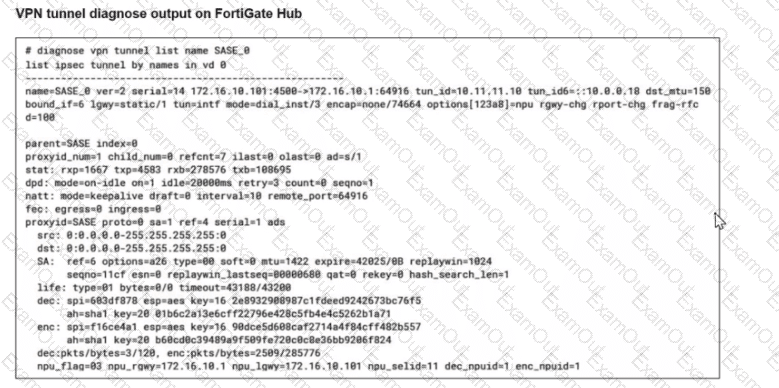
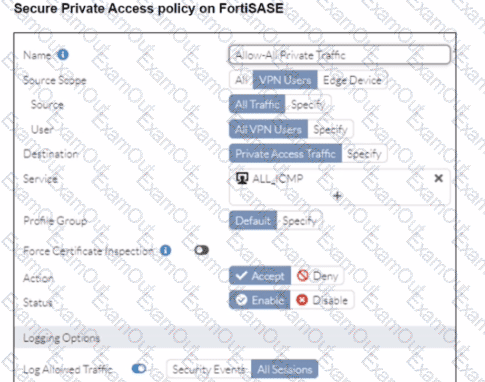
A FortiSASE administrator is trying to configure FortiSASE as a spoke to a FortiGate hub. The tunnel is up to the FortiGale hub. However, the administrator is not able to ping the webserver hosted behind the FortiGate hub.
Based on the output, what is the reason for the ping failures?
During FortiSASE provisioning, how many security points of presence (POPs) need to be configured by the FortiSASE administrator?
When configuring the DLP rule in FortiSASE using Regex format, what would be the correct order for the configuration steps? (Place the four correct steps in order)

When you configure FortiSASE Secure Private Access (SPA) with SD-WAN integration, you must establish a routing adjacency between FortiSASE and the FortiGate SD-WAN hub. Which routing protocol must you use?
You are designing a new network, and the cybersecurity policy mandates that all remote users working from home must always be connected and protected. Which FortiSASE component facilitates this always-on security measure? (Choose one answer)
You are configuring FortiSASE SSL deep inspection. What is required for FortiSASE to inspect encrypted traffic? (Choose one answer)


