Review the incident report:
Packet captures show a host maintaining periodic TLS sessions that imitate normal HTTPS traffic but run on TCP 8443 to a single external host. An analyst flags the traffic as potential command-and-control. During the same period, the host issues frequent DNS queries with oversized TXT payloads to an attacker-controlled domain, transferring staged files.
Which two MITRE ATT&CK techniques best describe this activity? (Choose two answers)
Based on the Pyramid of Pain model, which two statements accurately describe the value of an indicator and how difficult it is for an adversary to change? (Choose two answers)
Refer to the exhibit.
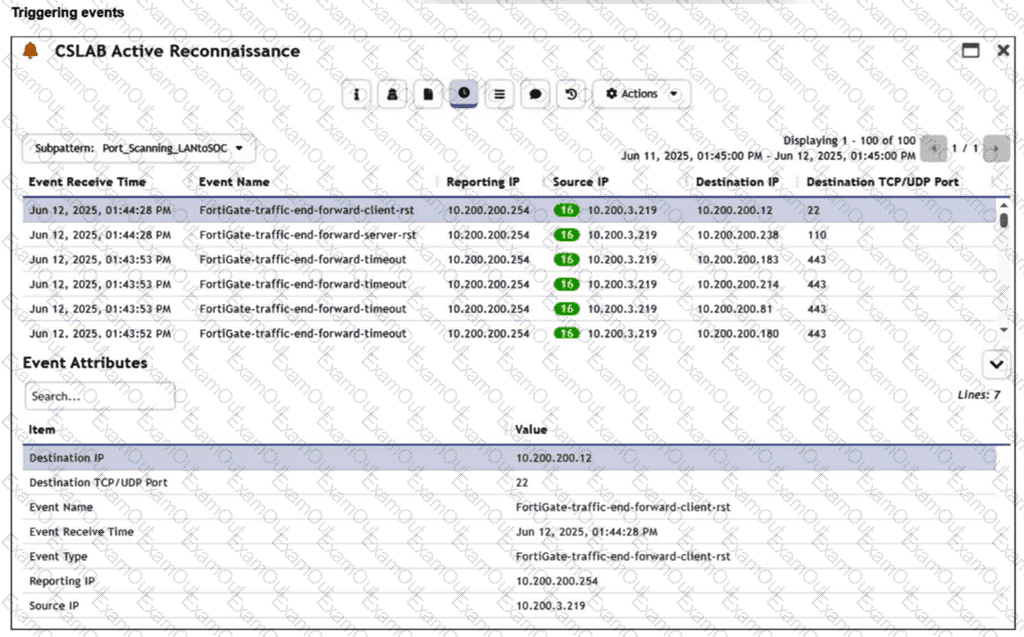
You are reviewing the Triggering Events page for a FortiSIEM incident. You want to remove the Reporting IP column because you have only one firewall in the topology. How do you accomplish this? (Choose one answer)
Refer to the exhibits.
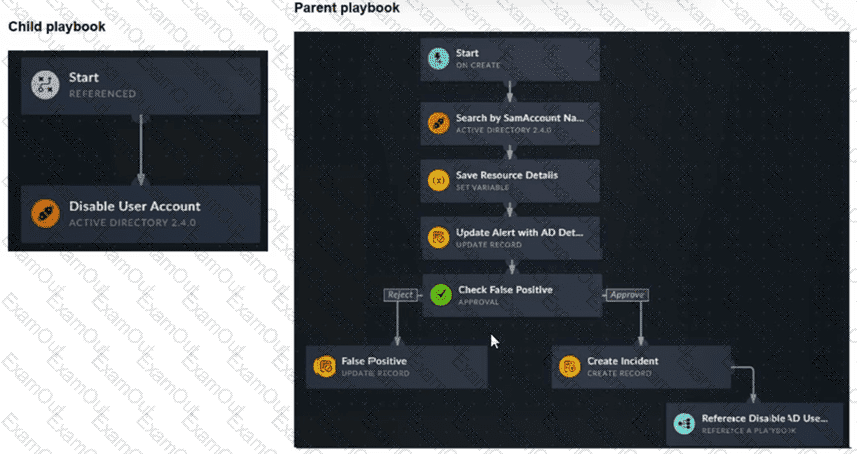
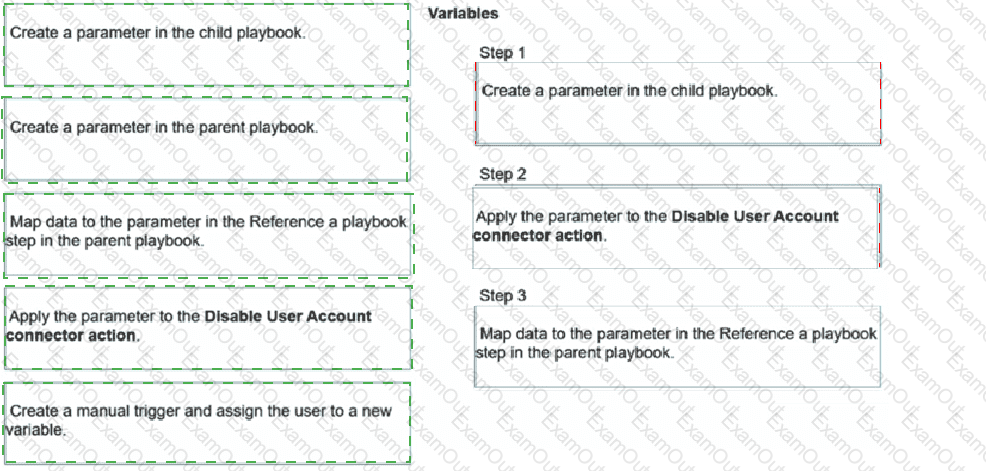
You have a playbook that, depending on whether an analyst deems the alert to be a true positive, could reference a child playbook. You need to pass variables from the parent playbook to the child playbook.
Place the steps needed to accomplish this in the correct order.
Refer to the exhibit.
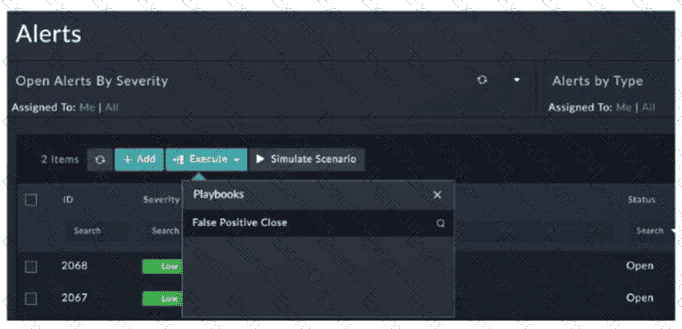
You configured a playbook namedFalse Positive Close, and want to run it to verify if it works. However, when you clickExecuteand search for the playbook, you do not see it listed. Which two reasons could be the cause of the problem? (Choose two answers)
Which three factors does the FortiSIEM rules engine use to determine the count when it evaluates the aggregate condition COUNT (Matched Events) on a specific subpattern? (Choose three answers)
Which two playbook triggers enable the use of trigger events in later tasks as trigger variables? (Choose two.)
Refer to the exhibit.
Assume that all devices in the FortiAnalyzer Fabric are shown in the image.
Which two statements about the FortiAnalyzer Fabric deployment are true? (Choose two.)
When you use a manual trigger to save user input as a variable, what is the correct Jinja expression to reference the variable? (Choose one answer)
Review the following incident report:
Attackers leveraged a phishing email campaign targeting your employees.
The email likely impersonated a trusted source, such as the IT department, and requested login credentials.
An unsuspecting employee clicked a malicious link in the email, leading to the download and execution of a Remote Access Trojan (RAT).
The RAT provided the attackers with remote access and a foothold in the compromised system.
Which two MITRE ATT&CK tactics does this incident report capture? (Choose two.)