Exhibit:
Which observation about this FortiAnalyzer Fabric deployment architecture is true?
Refer to the exhibit.
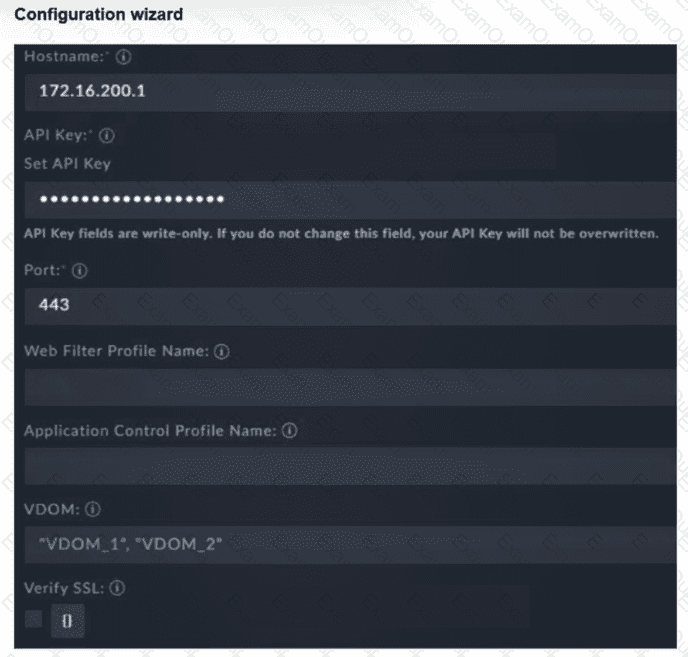
You must configure the FortiGate connector to allow FortiSOAR to perform actions on a firewall. However, the connection fails. Which two configurations are required? (Choose two answers)
Refer to the exhibits.
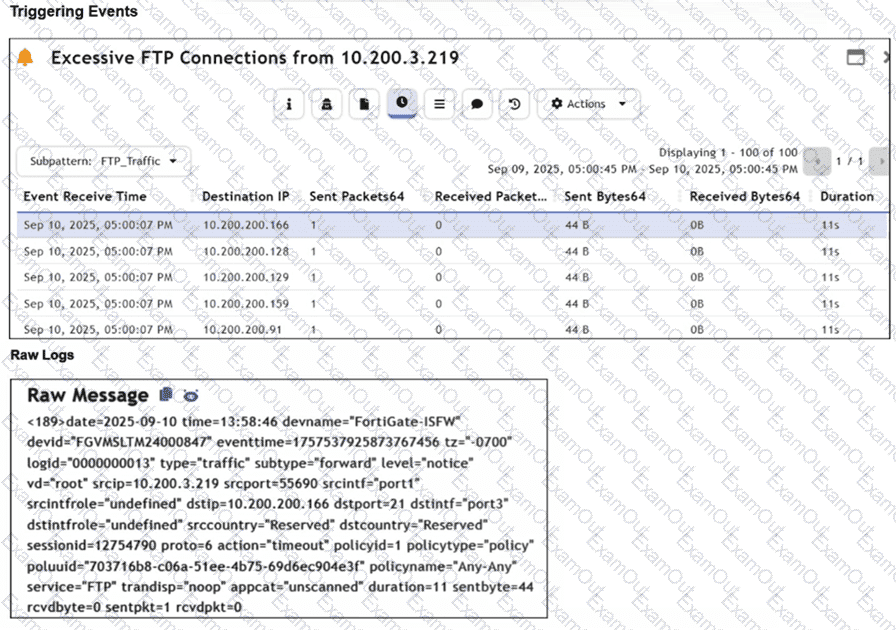
Assume that the traffic flows are identical, except for the destination IP address. There is only one FortiGate in network address translation (NAT) mode in this environment.
Based on the exhibits, which two conclusions can you make about this FortiSIEM incident? (Choose two answers)
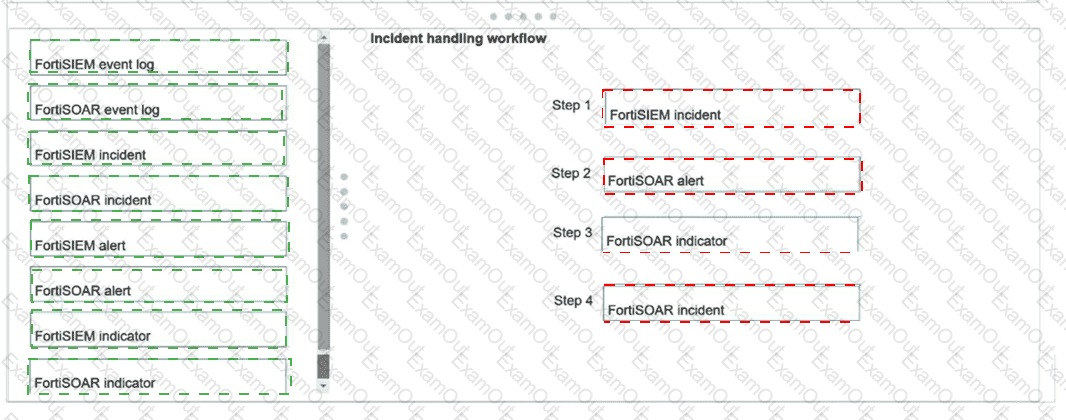
Using the default data ingestion wizard in FortiSOAR, place the incident handling workflow from FortiSIEM to FortiSOAR in the correct sequence. Select each workflow component in the left column, hold and drag it to a blank position in the column on the right. Place the four correct workflow components in order, placing the first step in the first position at the top of the column.
Refer to the exhibits.
The DOS attack playbook is configured to create an incident when an event handler generates a denial-of-ser/ice (DoS) attack event.
Why did the DOS attack playbook fail to execute?
Refer to the exhibit.
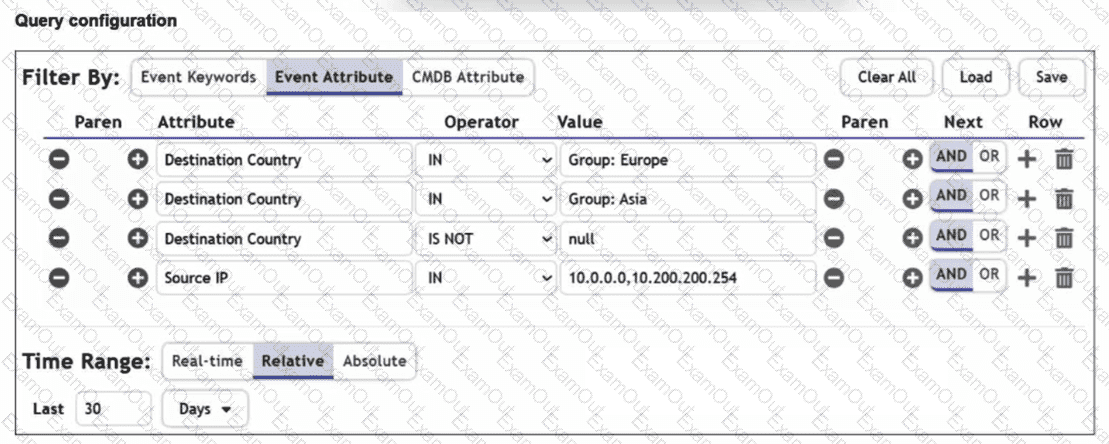
You are trying to find traffic flows to destinations that are in Europe or Asia, for hosts in the local LAN segment. However, the query returns no results. Assume these logs exist on FortiSIEM.
Which three mistakes can you see in the query shown in the exhibit? (Choose three answers)
Refer to the exhibits.
You configured a spearphishing event handler and the associated rule. However. FortiAnalyzer did not generate an event.
When you check the FortiAnalyzer log viewer, you confirm that FortiSandbox forwarded the appropriate logs, as shown in the raw log exhibit.
What configuration must you change on FortiAnalyzer in order for FortiAnalyzer to generate an event?