Refer to the exhibits.
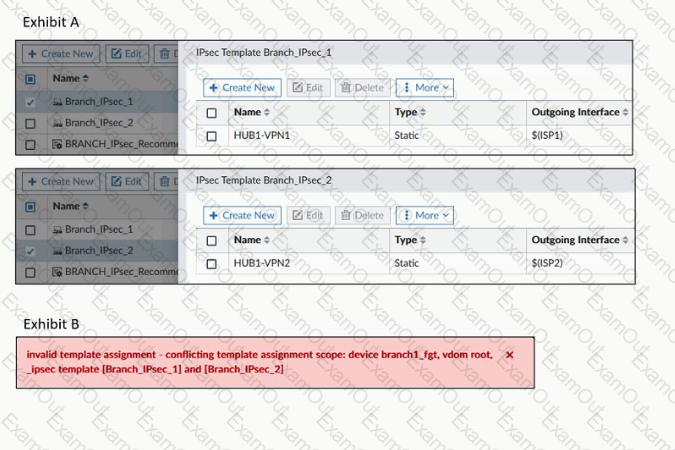
Exhibit A shows two IPsec templates to define Branch_IPsec_1 and Branch_IPsec_2. Each template defines a VPN tunnel.
Exhibit B shows the error message that FortiManager displayed when the administrator tried to assign the second template to the FortiGate device.
Which statement best explain the cause for this issue?
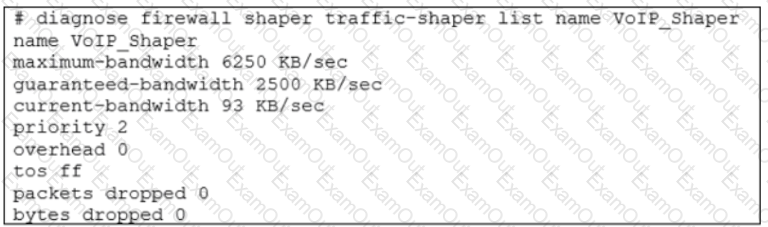
Which two conclusions for traffic that matches the traffic shaper are true? (Choose two.)
Which two statements about SD-WAN central management are true? (Choose two.)
What are two benefits of using forward error correction (FEC) in IPsec VPNs? (Choose two.)
Which diagnostic command can you use to show the SD-WAN rules, interface information, and state?
diagnose sys sdwan service
diagnose sys sdwan route-tag-list
diagnose sys sdwan member
Refer to the exhibit, which shows an SD-WAN zone configuration on the FortiGate GUI.
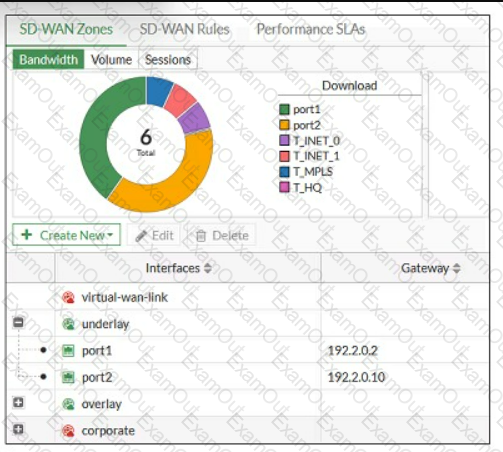
Based on the exhibit, which statement is true?
Refer to the exhibit.
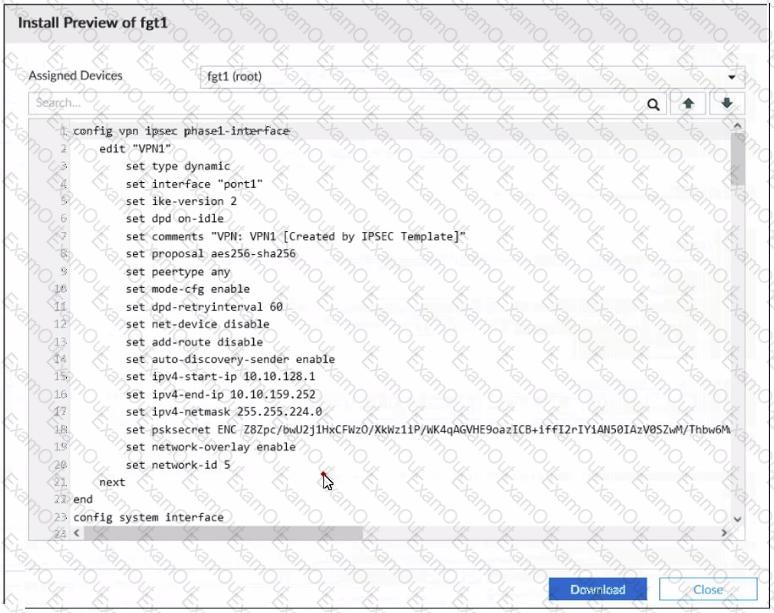
An administrator used the SD-WAN overlay template to prepare an IPsec configuration for a hub-and-spoke SD-WAN topology. The exhibit shows the installation preview for one FortiGate device. In the exhibit, which statement best describes the configuration applied to the FortiGate device?
Which two protocols in the IPsec suite are most used for authentication and encryption? (Choose two.)
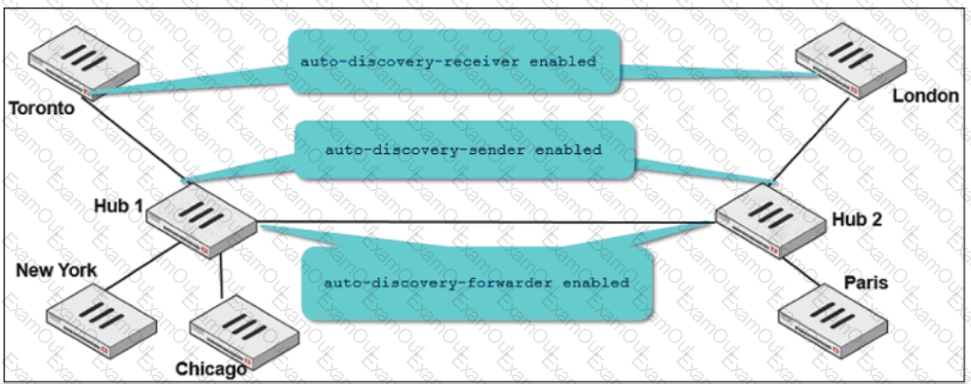
Two hub-and-spoke groups are connected through a site-to-site IPsec VPN between Hub 1 and Hub 2. The administrator configured ADVPN on both hub-and-spoke groups.
Which two outcomes are expected if a user in Toronto sends traffic to London? (Choose two.)

