Within IPsec tunnel templates available on FortiManager. which template will you use to configure static tunnels for a hub and spoke topology?
Refer to the exhibits.
Exhibit A
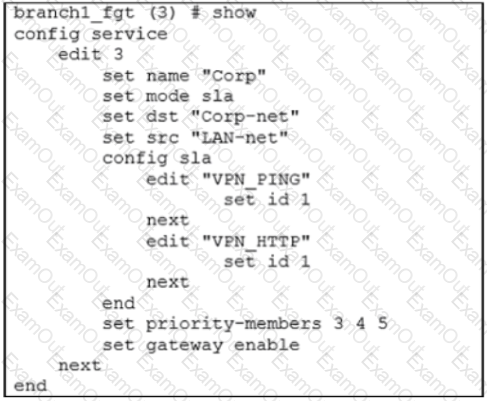
Exhibit B -
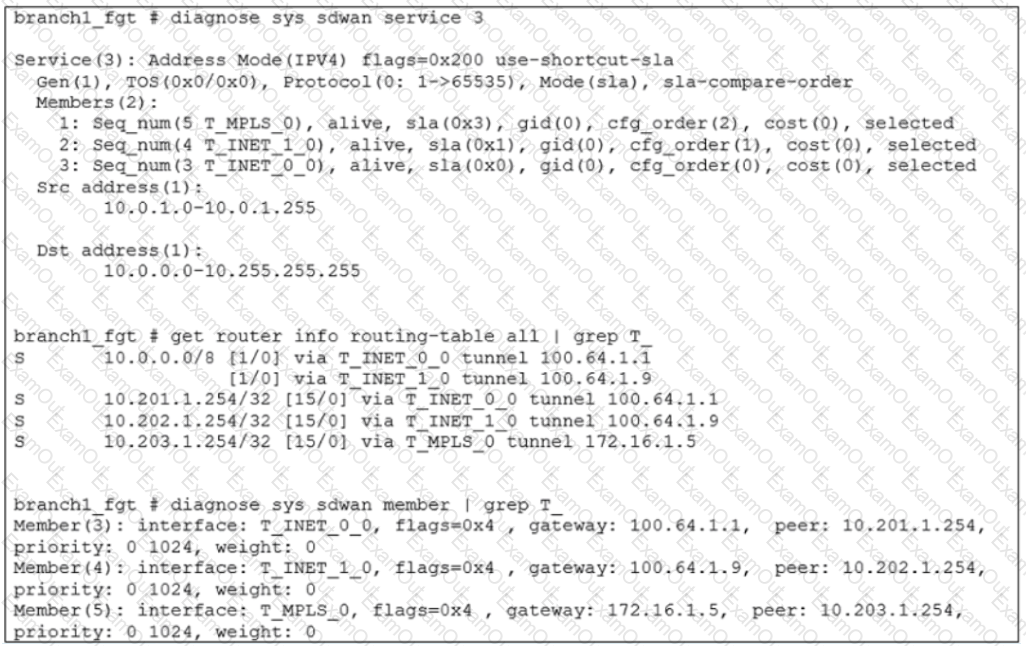
Exhibit A shows the configuration for an SD-WAN rule and exhibit B shows the respective rule status, the routing table, and the member status.
The administrator wants to understand the expected behavior for traffic matching the SD-WAN rule.
Based on the exhibits, what can the administrator expect for traffic matching the SD-WAN rule?
Refer to the exhibit.
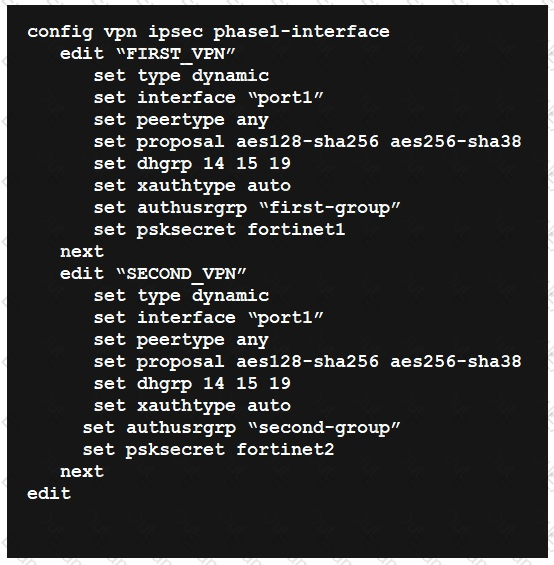
FortiGate has multiple dial-up VPN interfaces incoming on port1 that match only FIRST_VPN.
Which two configuration changes must be made to both IPsec VPN interfaces to allow incoming connections to match all possible IPsec dial-up interfaces? (Choose two.)
Which three matching traffic criteria are available in SD-WAN rules? (Choose three.)
Which diagnostic command can you use to show the member utilization statistics measured by performance SLAs for the last 10 minutes?
Refer to the exhibit.
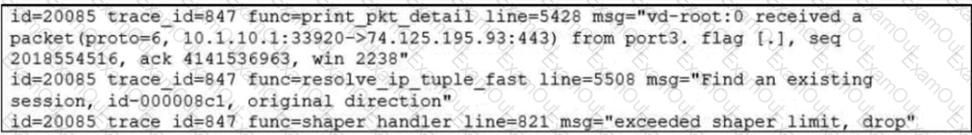
Which conclusion about the packet debug flow output is correct?
Which two statements are correct when traffic matches the implicit SD-WAN rule? (Choose two.)
Refer to the exhibit.
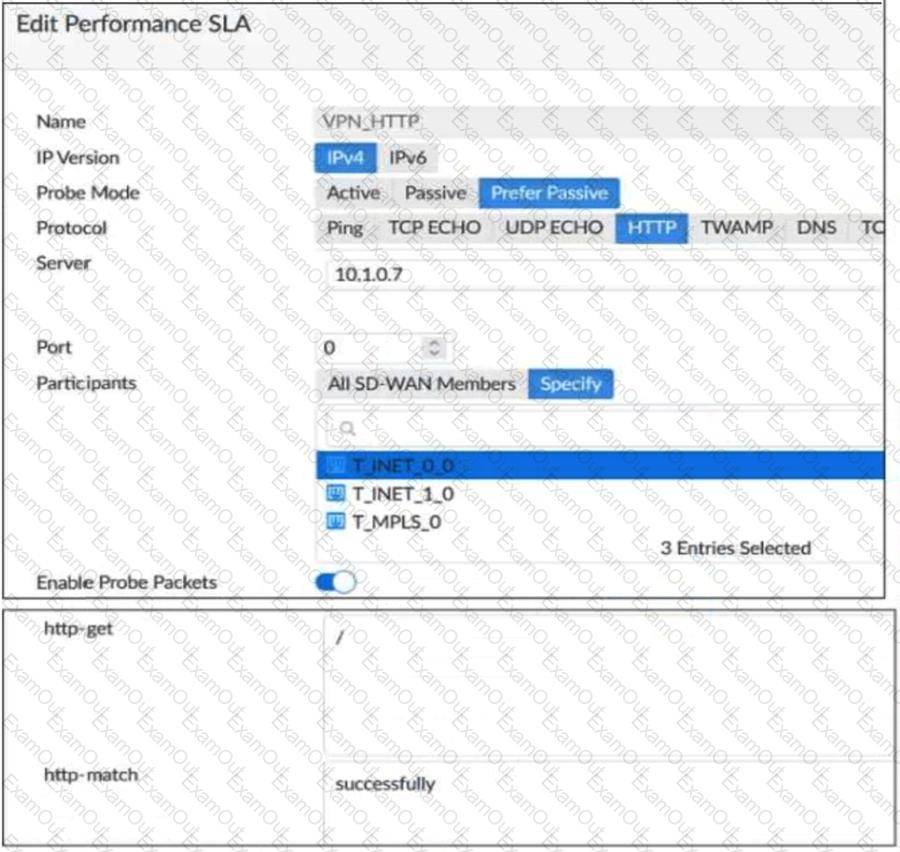
Based on the exhibit, which two statements are correct about the health of the selected members? (Choose two.)
Refer to the exhibit.
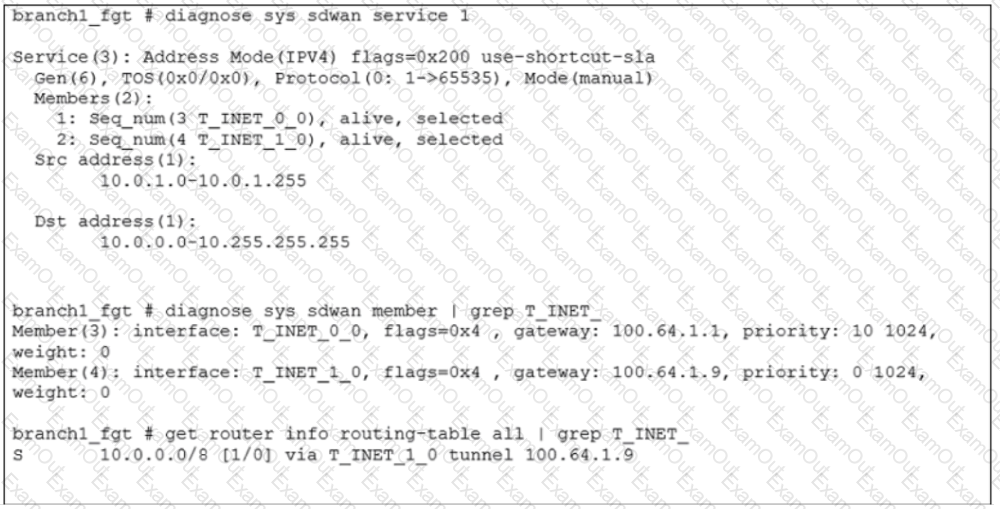
An administrator is troubleshooting SD-WAN on FortiGate. A device behind branch1_fgt generates traffic to the 10.0.0.0/8 network. The administrator expects the traffic to match SD-WAN rule ID 1 and be routed over T_INET_0_0. However, the traffic is routed over T_INET_1_0.
Based on the output shown in the exhibit, which two reasons can cause the observed behavior? (Choose two.)
Which two statements describe how IPsec phase 1 main mode is different from aggressive mode when performing IKE negotiation? (Choose two )

