You must add an Amazon Web Services (AWS) network access list (NACL) rule to allow SSH traffic to a subnet for temporary testing purposes. When you review the current inbound and outbound NACL rules, you notice that the rules with number 5 deny SSH and telnet traffic to the subnet.
What can you do to allow SSH traffic?
An administrator implements FortiWeb ingress controller to protect containerized web applications in an AWS Elastic Kubernetes Service (EKS) cluster.
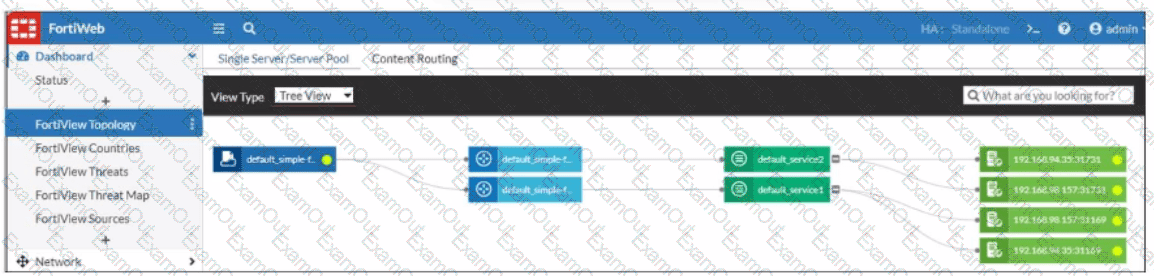
What can you conclude about the topology shown in FortiView?
Refer to the exhibit.
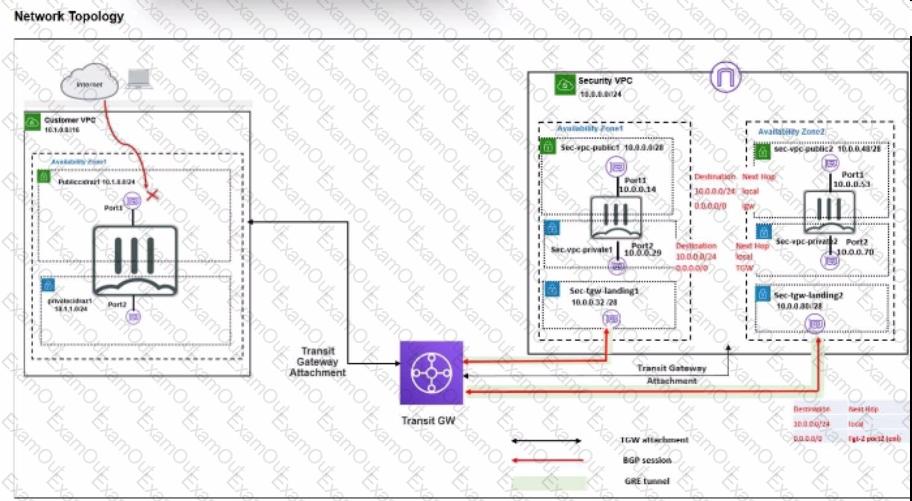
In your Amazon Web Services (AWS), you must allow inbound HTTPS access to the Customer VPC FortiGate VM from the internet. However, your HTTPS connection to the FortiGate VM in the Customer VPC is not successful.
Also, you must ensure that the Customer VPC FortiGate VM sends all the outbound Internet traffic through the Security VPC.
How do you correct this issue with minimal configuration changes? (Choose three.)
Refer to the exhibit.
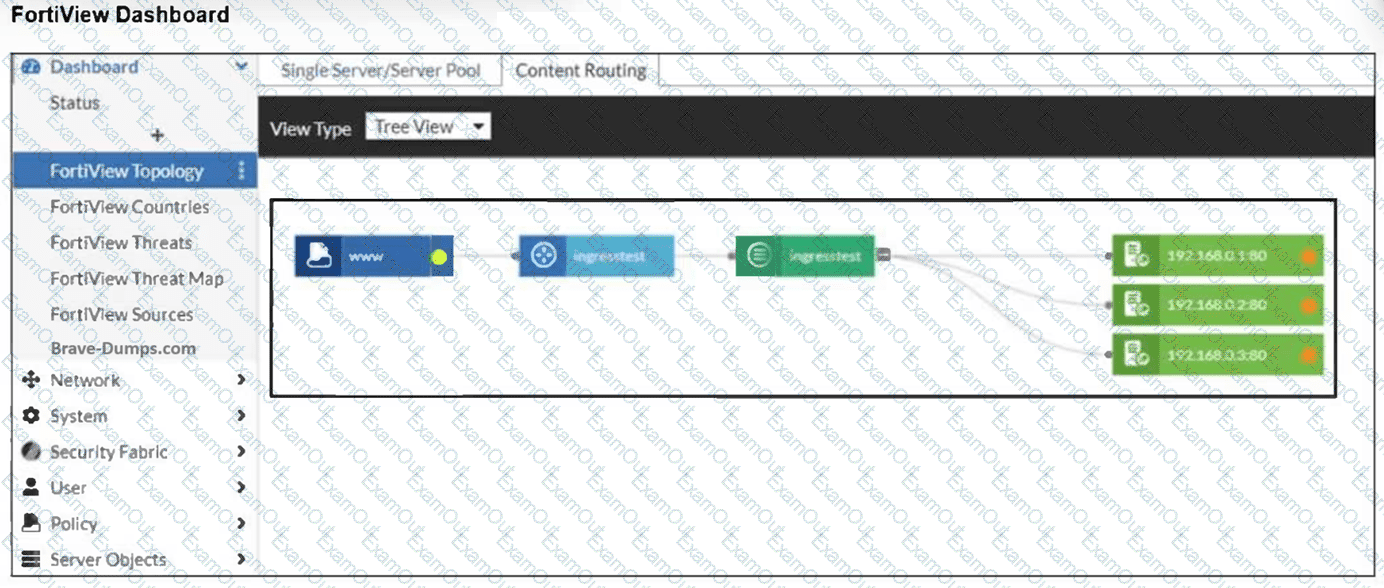
An administrator installed a FortiWeb ingress controller to protect a containerized web application. What is the reason for the status shown in FortiView? (Choose one answer)
Refer to the exhibit.
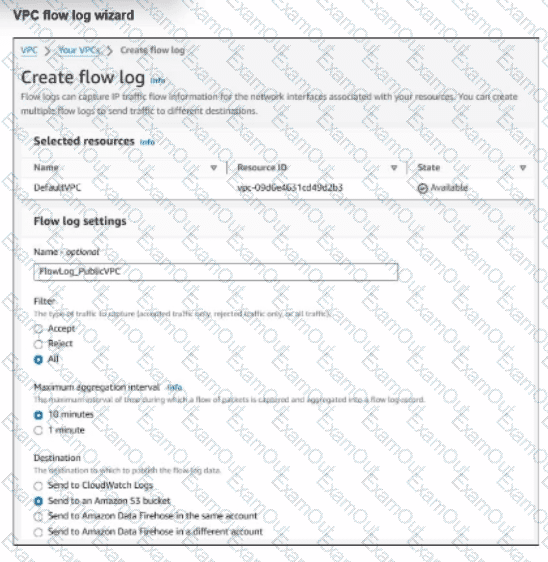
An experienced AWS administrator is creating a new virtual public cloud (VPC) flow log with the settings shown in the exhibit.
What is the purpose of this configuration?
An administrator would like to use FortiCNP to keep track of sensitive data files located in the Amazon Web Services (AWS) S3 bucket and protect it from malware. Which FortiCNP feature should the administrator use?
The cloud administration team is reviewing an AWS deployment that was done using CloudFormation.
The deployment includes six FortiGate instances that required custom configuration changes after being deployed. The team notices that unwanted traffic is reaching some of the FortiGate instances because the template is missing a security group.
To resolve this issue, the team decides to update the JSON template with the missing security group and then apply the updated template directly, without using a change set.
What is the result of following this approach?
An administrator is relying on an Azure Bicep linter to find possible issues in Bicep files.
Which problem can the administrator expect to find?
Your monitoring team reports performance issues with a web application hosted in Azure. You suspect that the bottleneck might be due to unexpected inbound traffic spikes.
Which method should you use to identify and analyze the traffic pattern?
How does an administrator secure container environments in Amazon AWS from newly emerged security threats? (Choose one answer)

