(Refer to the exhibit.
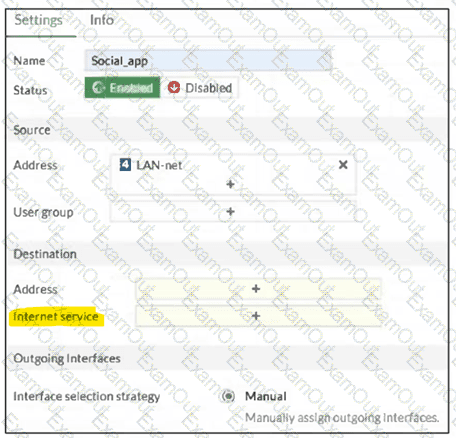
You configure SD-WAN on a standalone FortiGate device.
You want to create an SD-WAN rule that steers traffic related to Facebook and LinkedIn through the less costly internet link.
What must you do to set Facebook and LinkedIn applications as destinations from the GUI? Choose one answer.)
Refer to the exhibits.
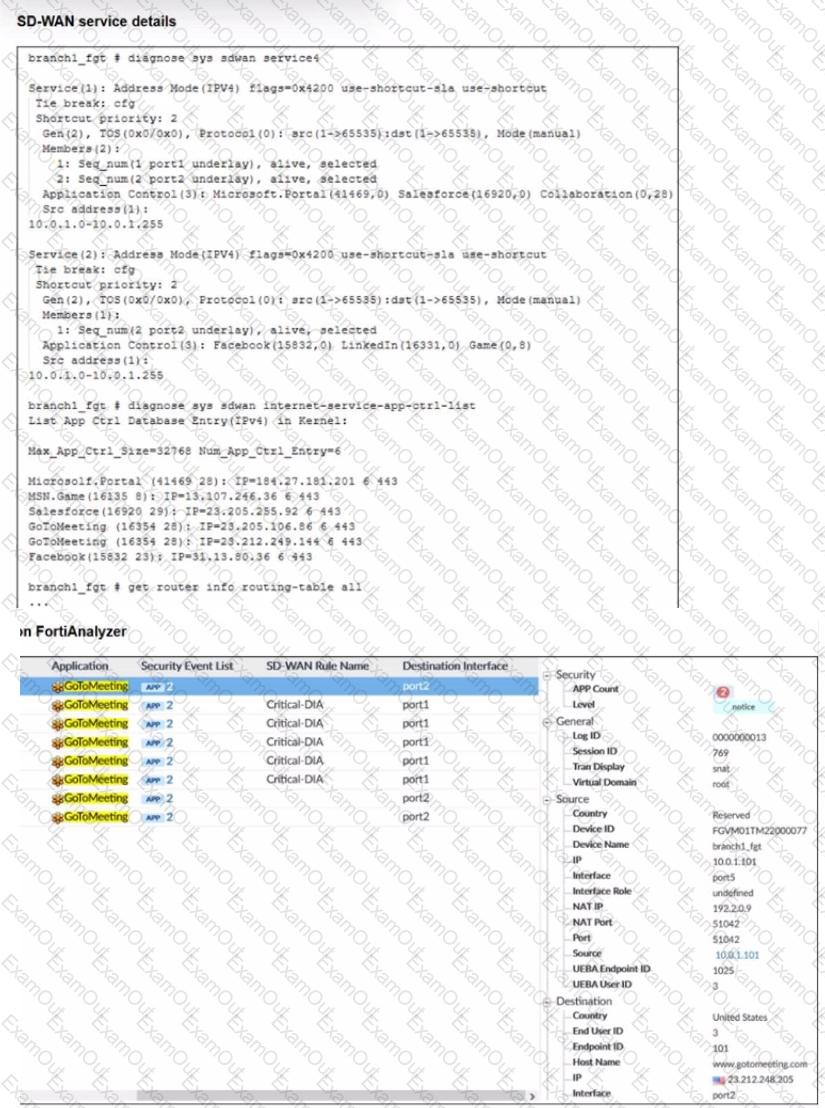
An administrator is testing application steering in SD-WAN. Before generating test traffic, the administrator collected the information shown in the first exhibit. After generating GoToMeeting test traffic, the administrator examined the corresponding traffic log on FortiAnalyzer, which is shown in the second exhibit.
The administrator noticed that the traffic matched the implicit SD-WAN rule, but they expected the traffic to match rule ID 1.
Which two reasons explain why some log messages show that the traffic matched the implicit SD-WAN rule? (Choose two.)
Within the context of SD-WAN, what does SIA correspond to?
Refer to the exhibit.
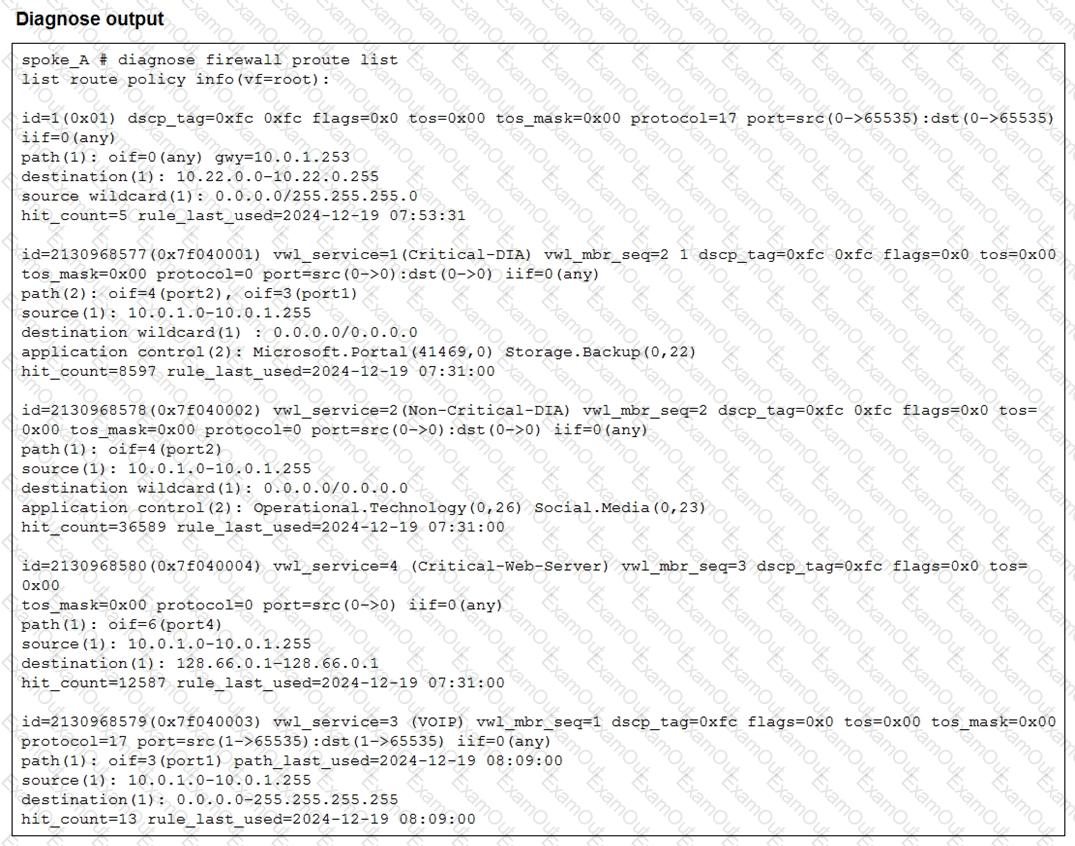
Which two conclusions can you draw from the output shown? (Choose two.)
(Refer to the exhibit.
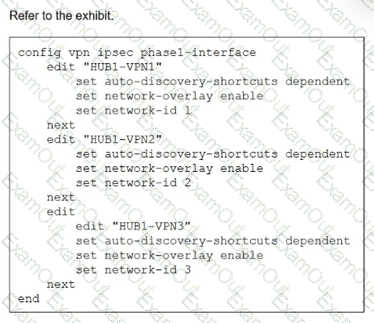
You update the spokes configuration of an existing auto-discovery VPN (ADVPN) topology by adding the parameters shown in the exhibit.
Which is a valid objective of those settings? Choose one answer.)
Refer to the exhibit that shows an SD-WAN zone configuration on the FortiManager GUI.
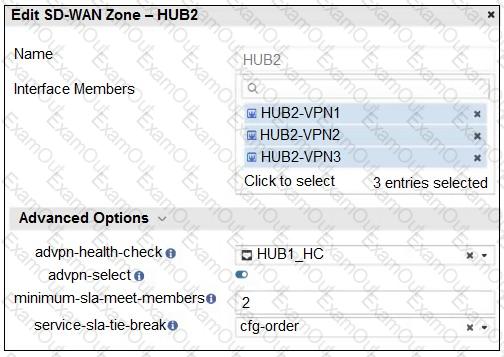
Based on the exhibit, how will the FortiGate device behave after it receives this configuration?
Which statement describes FortiGate behavior when you reference a zone in a static route?
When a customer delegate the installation and management of its SD-WAN infrastructure to an MSSP, the MSSP usually keeps the hub within its infrastructure for ease of management and to share costly resources.
In which two situations will the MSSP install the hub in customer premises? (Choose two.)

