Where are logical network values defined?
Which two things must be done to allow FortiNAC to process incoming syslog messages from an unknown vendor? (Choose two.)
Which three circumstances trigger Layer 2 polling of infrastructure devices? (Choose three.)
Where do you look to determine which network access policy, if any is being applied to a particular host?
Which devices would be evaluated by device profiling rules?
An administrator wants the Host At Risk event to generate an alarm. What is used to achieve this result?
Refer to the exhibit.
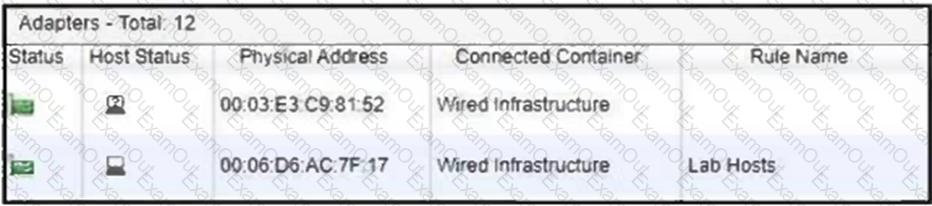
Considering the host status of the two hosts connected to the same wired port, what will happen if the port is a member of the Forced Registration port group?
While troubleshooting a network connectivity issue, an administrator determines that a device was being automatically provisioned to an incorrect VLAN.
Where would the administrator look to determine when and why FortiNAC made the network access change?
Which two methods can be used to gather a list of installed applications and application details from a host? (Choose two.)
Which agent can receive and display messages from FortiNAC to the end user?

