Which secure internet access (SIA) use case minimizes individual endpoint configuration?
Which two purposes is the dedicated IP address used for in a FortiSASE deployment? (Choose two.)
For monitoring potentially unwanted applications on endpoints, which information is available on the FortiSASE software installations page?
Refer to the exhibits.
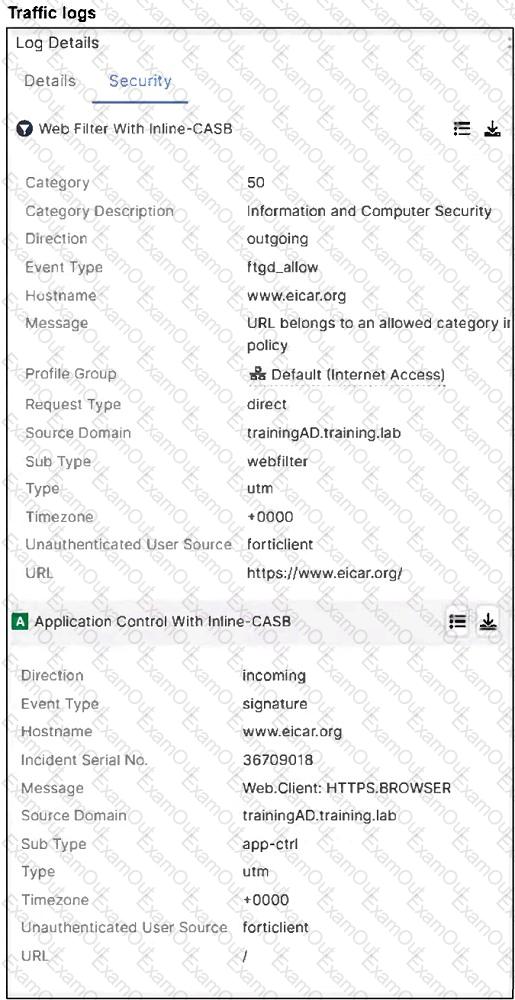
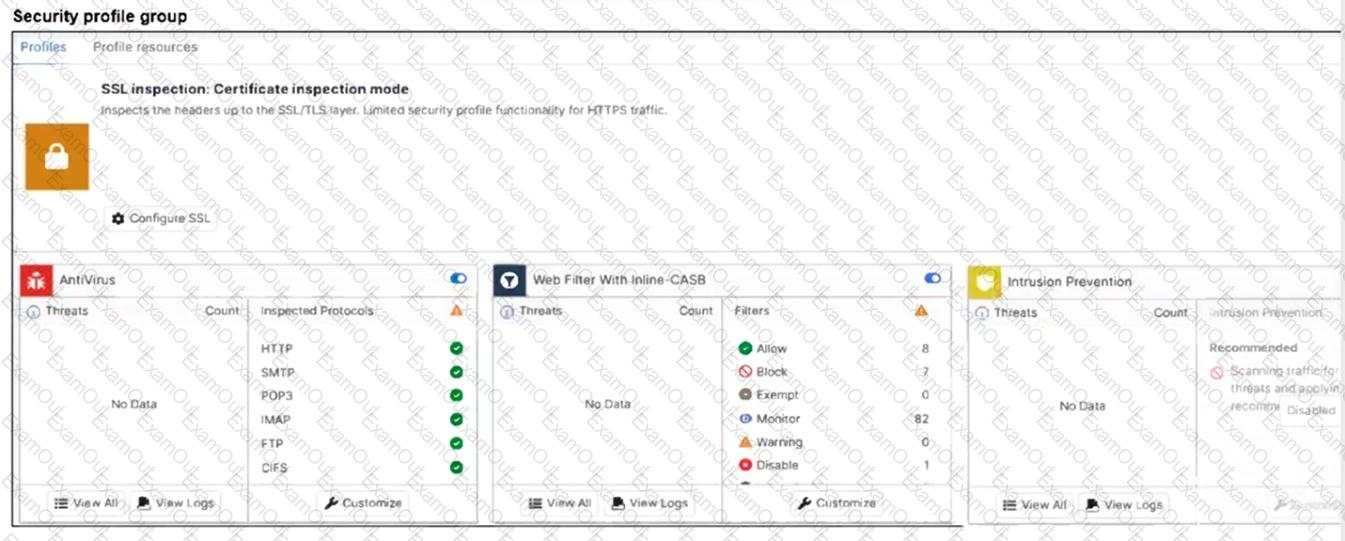
A FortiSASE administrator has configured an antivirus profile in the security profile group and applied it to the internet access policy. Remote users are still able to download the eicar.com-zip file from https://eicar.org.
Which configuration on FortiSASE is allowing users to perform the download?
Refer to the exhibit.
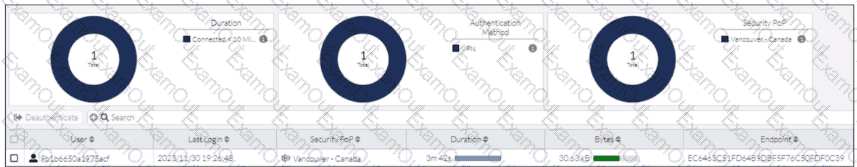
While reviewing the traffic logs, the FortiSASE administrator notices that the usernames are showing random characters.
Why are the usernames showing random characters?
How does FortiSASE hide user information when viewing and analyzing logs?
Which two settings are automatically pushed from FortiSASE to FortiClient in a new FortiSASE deployment with default settings? (Choose two.)
Which two of the following can release the network lockdown on the endpoint applied by FortiSASE? (Choose two.)\
What are two benefits of deploying FortiSASE with FortiGate ZTNA access proxy? (Choose two.)
Refer to the exhibit.
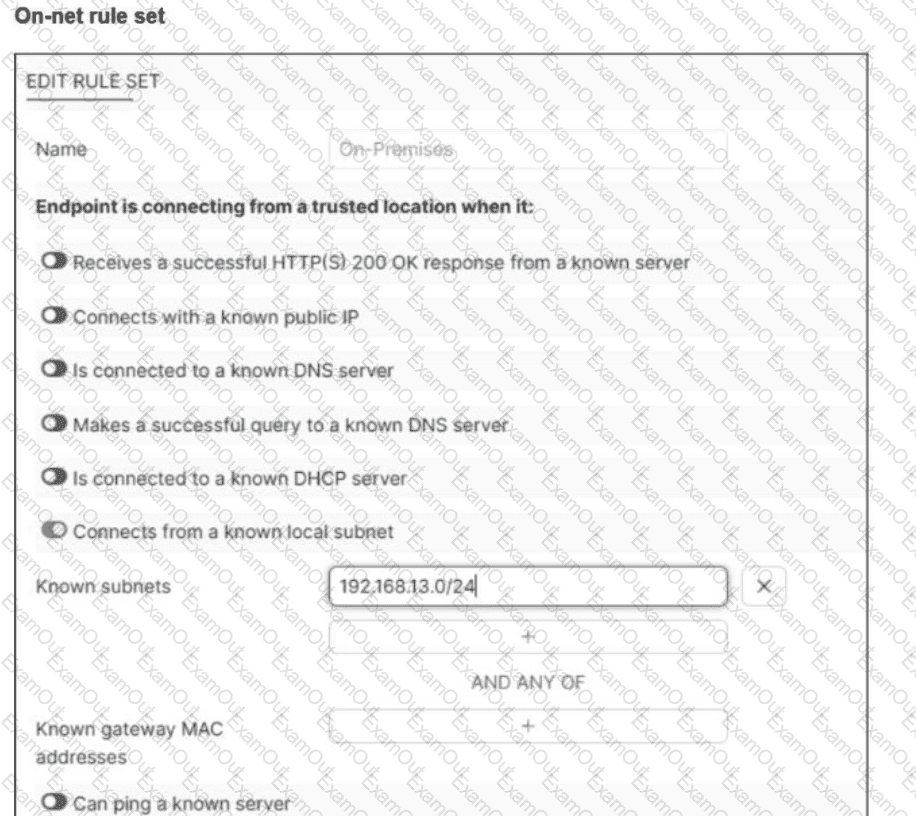
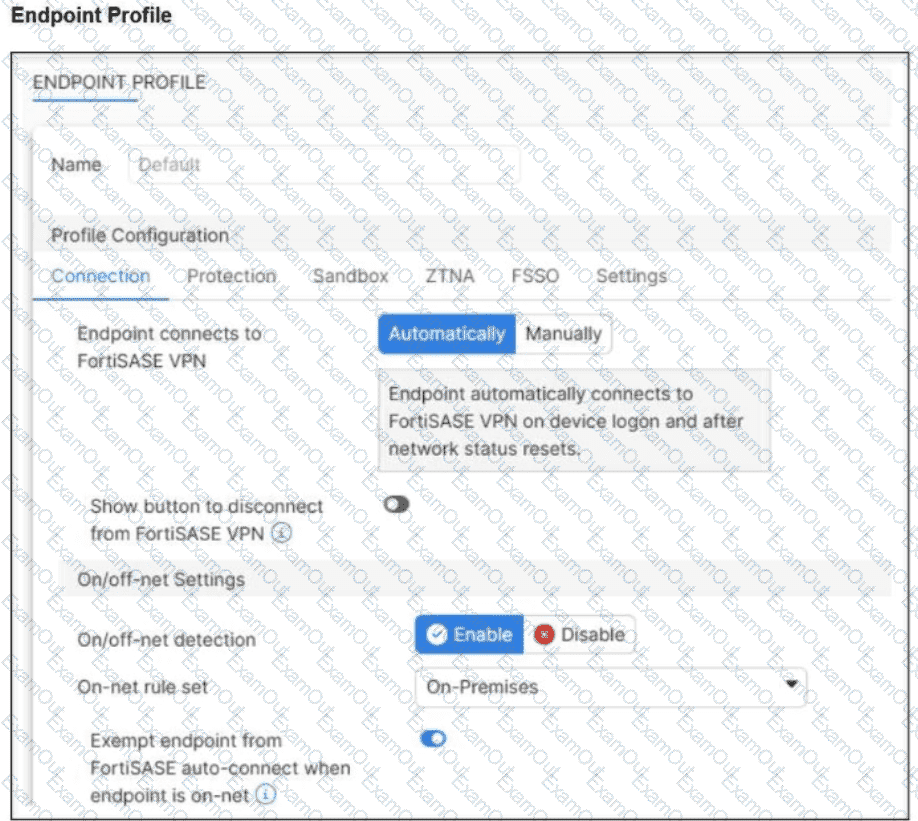
An endpoint is assigned an IP address of 192.168.13.101/24.
Which action will be run on the endpoint?

