Refer to the exhibit.
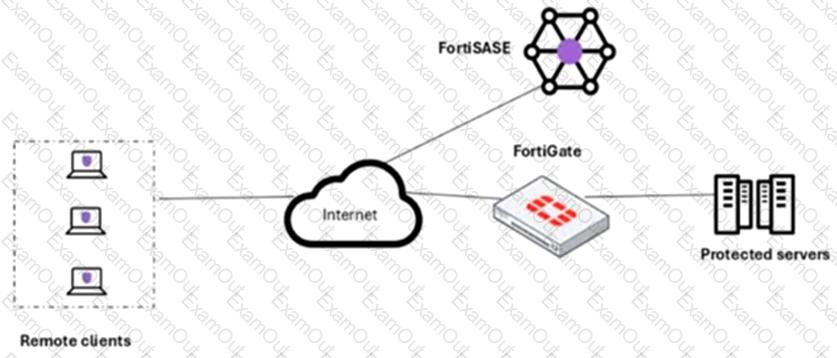
A customer needs to implement device posture checks for their remote endpoints while accessing the protected server. They also want the TCP traffic between the remote endpoints and the protected servers to be processed by FortiGate.
In this scenario, which two setups will achieve these requirements? (Choose two.)
Refer to the exhibit.
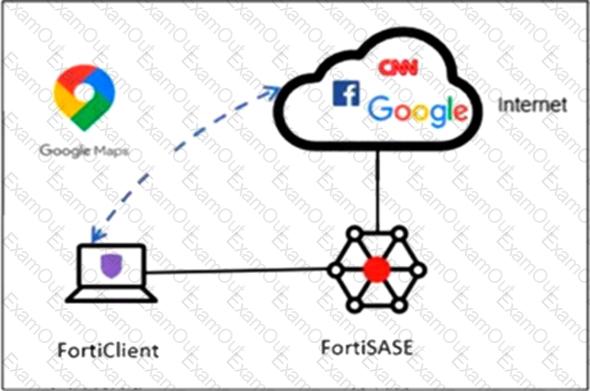
An organization must inspect all the endpoint internet traffic on FortiSASE, and exclude Google Maps traffic from the FortiSASE VPN tunnel and redirect it to the endpoint physical interface.
Which configuration must you apply to achieve this requirement?
A customer wants to ensure secure access for private applications for their users by replacing their VPN.
Which two SASE technologies can you use to accomplish this task? (Choose two.)
Which FortiSASE component protects users from online threats by hosting their browsing sessions on a remote container within a secure environment?
Which two advantages does FortiSASE bring to businesses with microbranch offices that have FortiAP deployed for unmanaged devices? (Choose two.)

