An administrator must minimize CPU and RAM use on a FortiGate firewall while also enabling essential security features, such as web filtering and application control for HTTPS traffic.
Which SSL inspection setting helps reduce system load while also enabling security features, such as web filtering and application control for encrypted HTTPS traffic?
Refer to the exhibit.
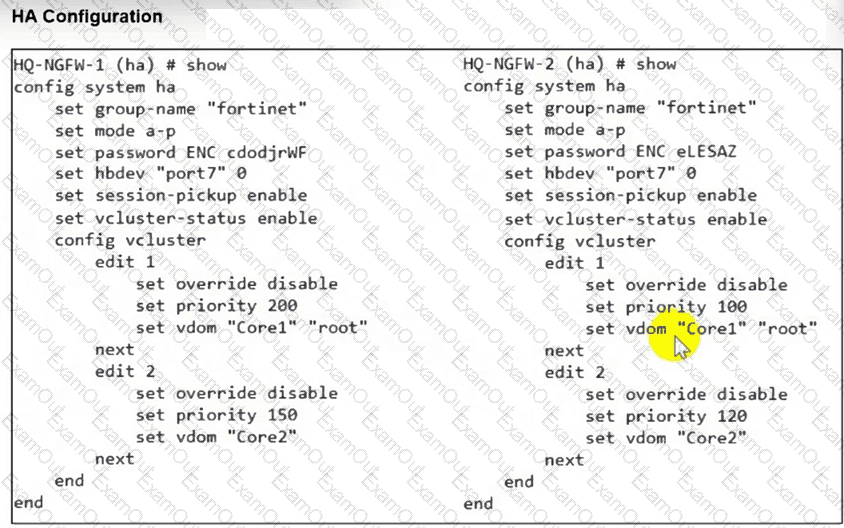
An HA configuration of an active-active (A-A) cluster with the same HA uptime is shown. You want HQ-NGFW-2 to handle the Core2 VDOM traffic. Which modification must you make to achieve this outcome? (Choose one answer)
Refer to the exhibit, which shows a partial enterprise network.
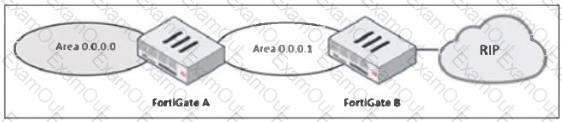
An administrator would like the area 0.0.0.0 to detect the external network.
What must the administrator configure?
Refer to the exhibit, which contains a partial VPN configuration.
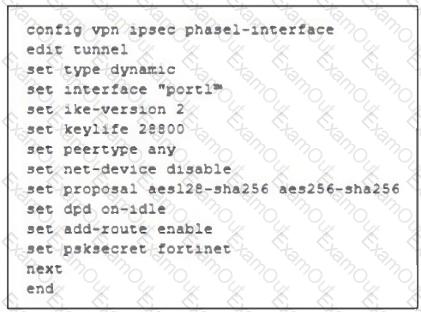
What can you conclude from this VPN IPsec phase 1 configuration?
Refer to the exhibit, which shows a hub and spokes deployment.
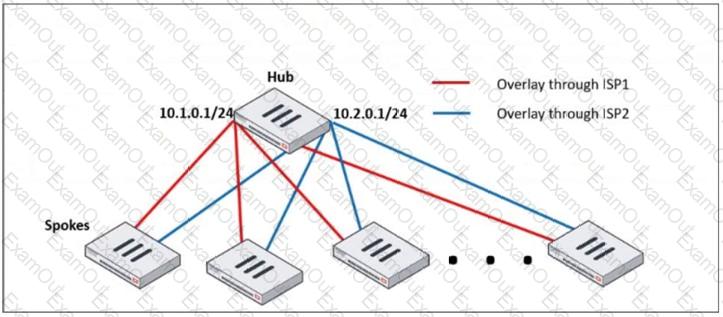
An administrator is deploying several spokes, including the BGP configuration for the spokes to connect to the hub.
Which two commands allow the administrator to minimize the configuration? (Choose two.)
Refer to the exhibit, which contains a partial command output.

The administrator has configured BGP on FortiGate. The status of this new BGP configuration is shown in the exhibit.
What configuration must the administrator consider next?
What is the initial step performed by FortiGate when handling the first packets of a session?
Refer to the exhibit.
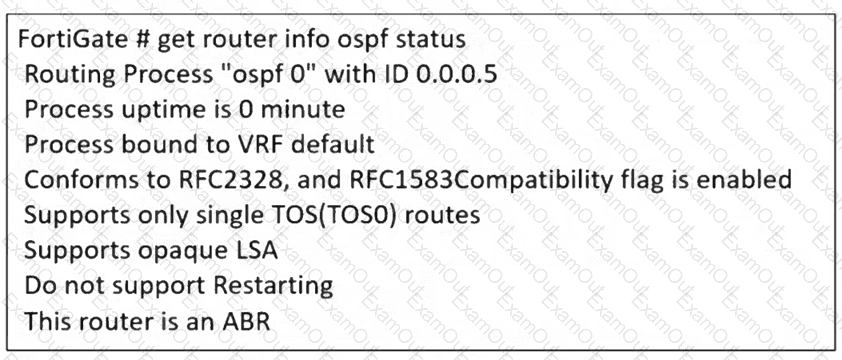
The partial output of an OSPF command is shown. While checking the OSPF status of FortiGate, you receive the output shown in the exhibit. Based on the output, which two statements about FortiGate are correct? (Choose two answers)
Refer to the exhibit, which shows an enterprise network connected to an internet service provider.
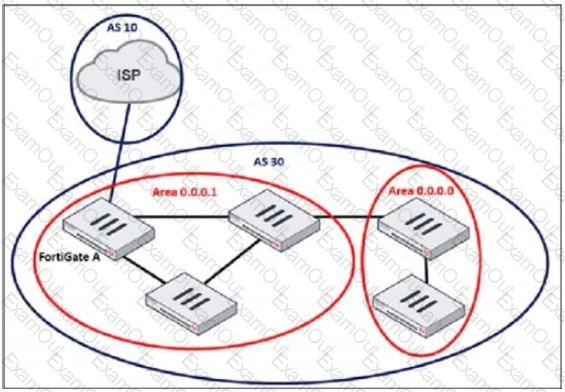
The administrator must configure the BGP section of FortiGate A to give internet access to the enterprise network.
Which command must the administrator use to establish a connection with the internet service provider?
Why does the ISDB block layers 3 and 4 of the OSI model when applying content filtering? (Choose two.)

