Refer to the exhibits.
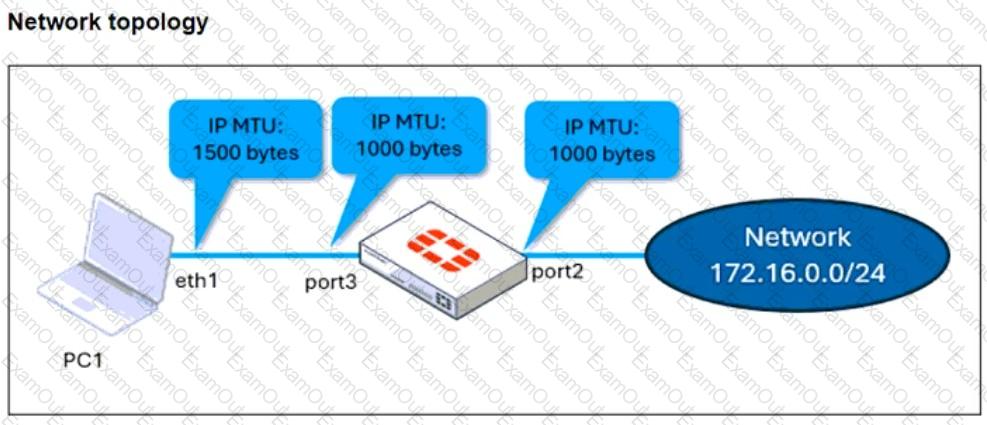
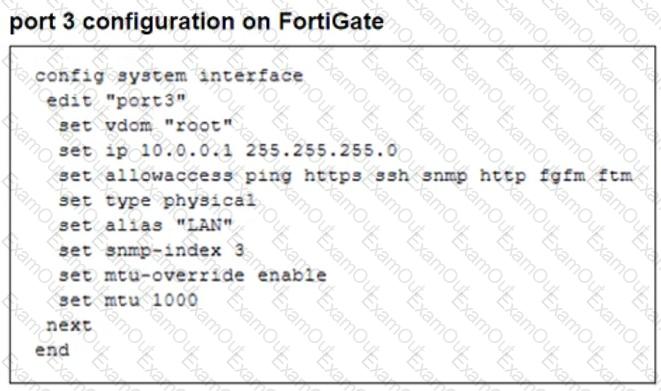
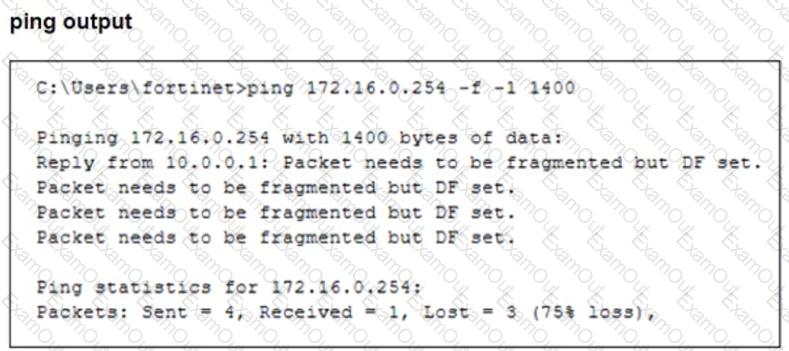
The configuration of a user's Windows PC, which has a default MTU of 1500 bytes, along with FortiGate interfaces set to an MTU of 1000 bytes, and the results of PC1 pinging server 172.16.0.254 are shown.
Why is the user in Windows PC1 unable to ping server 172.16.0.254 and is seeing the message: Packet needs to be fragmented but DF set?
Refer to the exhibit, which shows a command output.

FortiGate_A and FortiGate_B are members of an FGSP cluster in an enterprise network.
While testing the cluster using the ping command, the administrator monitors packet loss and found that the session output on FortiGate_B is as shown in the exhibit.
What could be the cause of this output on FortiGate_B?
Refer to the exhibit, which shows the ADVPN network topology and partial BGP configuration.
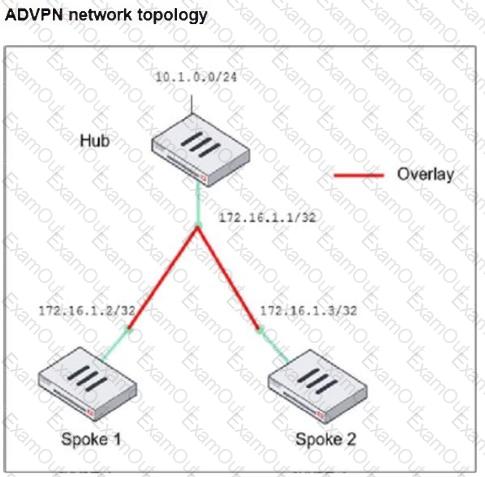

Which two parameters must an administrator configure in the config neighbor range for spokes shown in the exhibit? (Choose two.)
To secure your enterprise network traffic, which step does FortiGate perform first, when handling the first packets of a session? (Choose one answer)
A company's users on an IPsec VPN between FortiGate A and B have experienced intermittent issues since implementing VXLAN. The administrator suspects that packets exceeding the 1500-byte default MTU are causing the problems.
In which situation would adjusting the interface’s maximum MTU value help resolve issues caused by protocols that add extra headers to IP packets?
A FortiGate device with UTM profiles is reaching the resource limits, and the administrator expects the traffic in the enterprise network to increase.
The administrator has received an additional FortiGate of the same model.
Which two protocols should the administrator use to integrate the additional FortiGate device into this enterprise network? (Choose two.)
Which two statements about IKEv2 are true if an administrator decides to implement IKEv2 in the VPN topology? (Choose two.)
During the maintenance window, an administrator must sniff all the traffic going through a specific firewall policy, which is handled by NP6 interfaces. The output of the sniffer trace provides just a few packets.
Why is the output of sniffer trace limited?
Refer to the exhibits. The exhibits show a network topology, a firewall policy, and an SSL/SSH inspection profile configuration.
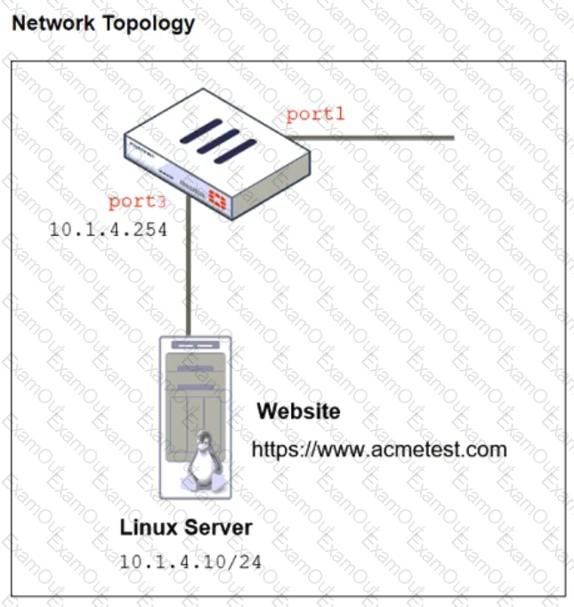
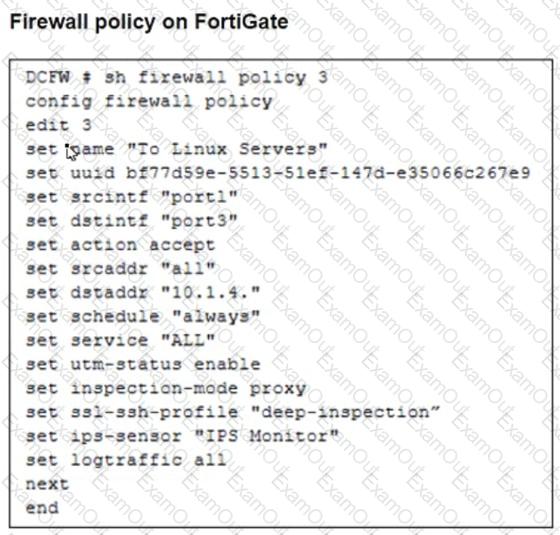

Why is FortiGate unable to detect HTTPS attacks on firewall policy ID 3 targeting the Linux server?

 FGSP allows session-aware load balancing between multiple FortiGate units without requiring them to be in an HA (High Availability) cluster.
FGSP allows session-aware load balancing between multiple FortiGate units without requiring them to be in an HA (High Availability) cluster. With external load balancers, incoming traffic is evenly distributed across multiple FortiGate devices.
With external load balancers, incoming traffic is evenly distributed across multiple FortiGate devices. This approach is useful for scaling out traffic handling capacity while ensuring that sessions remain synchronized between firewalls.
This approach is useful for scaling out traffic handling capacity while ensuring that sessions remain synchronized between firewalls. FGSP is effective when stateful failover is required but without the constraints of traditional HA.
FGSP is effective when stateful failover is required but without the constraints of traditional HA. FGCP active-active mode enables multiple FortiGate devices to share traffic loads, increasing throughput and efficiency.
FGCP active-active mode enables multiple FortiGate devices to share traffic loads, increasing throughput and efficiency. Active-active mode is suitable for balancing UTM processing across multiple FortiGates, making it ideal when resource limits are a concern.
Active-active mode is suitable for balancing UTM processing across multiple FortiGates, making it ideal when resource limits are a concern. Using switches ensures redundancy and avoids single points of failure in the network.
Using switches ensures redundancy and avoids single points of failure in the network. This mode is commonly used in enterprise networks where both scalability and redundancy are required.
This mode is commonly used in enterprise networks where both scalability and redundancy are required.