Which statement about how impersonation analysis identifies spoofed email addresses is correct?
What are Two reasons for having reliable DNS servers configured on FortiMail? (Choose two.)
Exhibit.
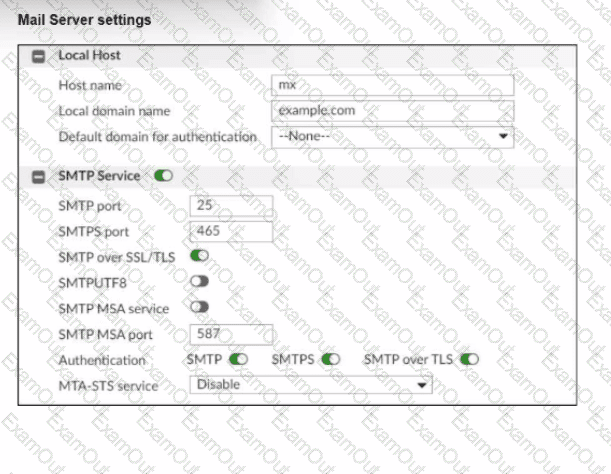
Refer to the exhibit, which shows the mail server settings of a FortiMail device. What are two ways this FortiMail device will handle connections? (Choose two.)
Refer to the exhibit, which shows a few lines of FortiMail logs.
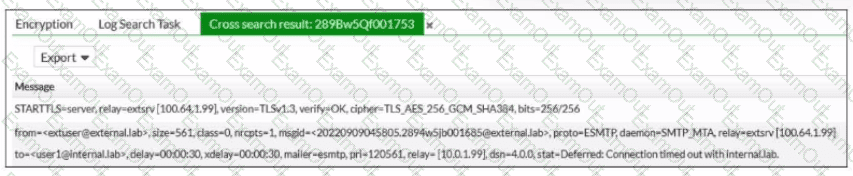
Based on these log entries, which two statements describe the operational status of this FortiMail device? (Choose two.)
A FortiMail administrator is concerned about cyber criminals attempting to get sensitive information from employees using whaling phishing attacks. What option can the administrator configure to prevent these types of attacks?
In which two ways does a transparent mode FortiMail use the build-it MTA to process email? (Choose two.)
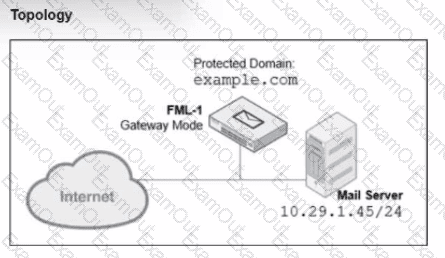

Refer to the exhibits, which show a topology diagram (Topology) and a configuration element (IP Policy).
An administrator has enabled the sender reputation feature in the Example_Session profile on FML-1. After a few hours, the deferred queue on the mail server starts filling up with undeliverable email.
Which two changes must theadministrator make to fix this issue? (Choose two.)
Refer to the exhibit, which shows an inbound recipient policy.
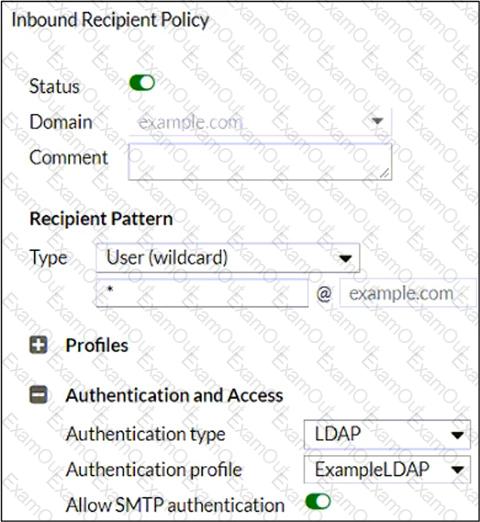
After creating the policy shown in the exhibit, an administrator discovers that clients can send unauthenticated emails using SMTP.
What must the administrator do to enforce authentication?
Refer to the exhibit, which shows the Authentication Reputation list on a FortiMail device running in gateway mode.
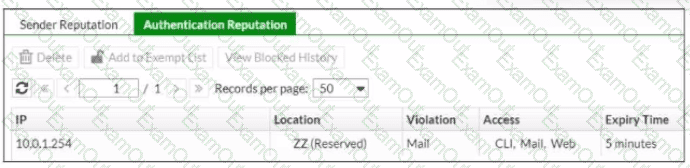
Why was the IP address blocked?
Which SMTP command lists (he supported SMTP service extensions of the recipient MTA?

