Refer to the exhibit to view the firewall policy.
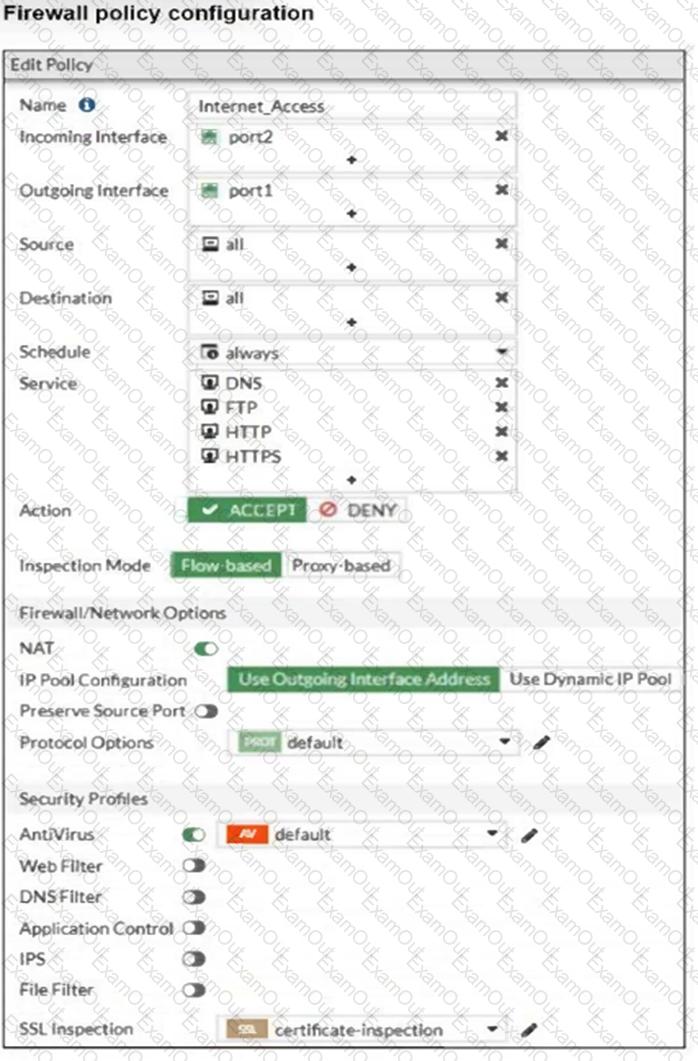
Why would the firewall policy not block a well-known virus, for example eicar?
Which two features of IPsec IKEv1 authentication are supported by FortiGate? (Choose two.)
An administrator has configured a strict RPF check on FortiGate.
How does strict RPF check work?
Refer to the exhibit showing a FortiGuard connection debug output.
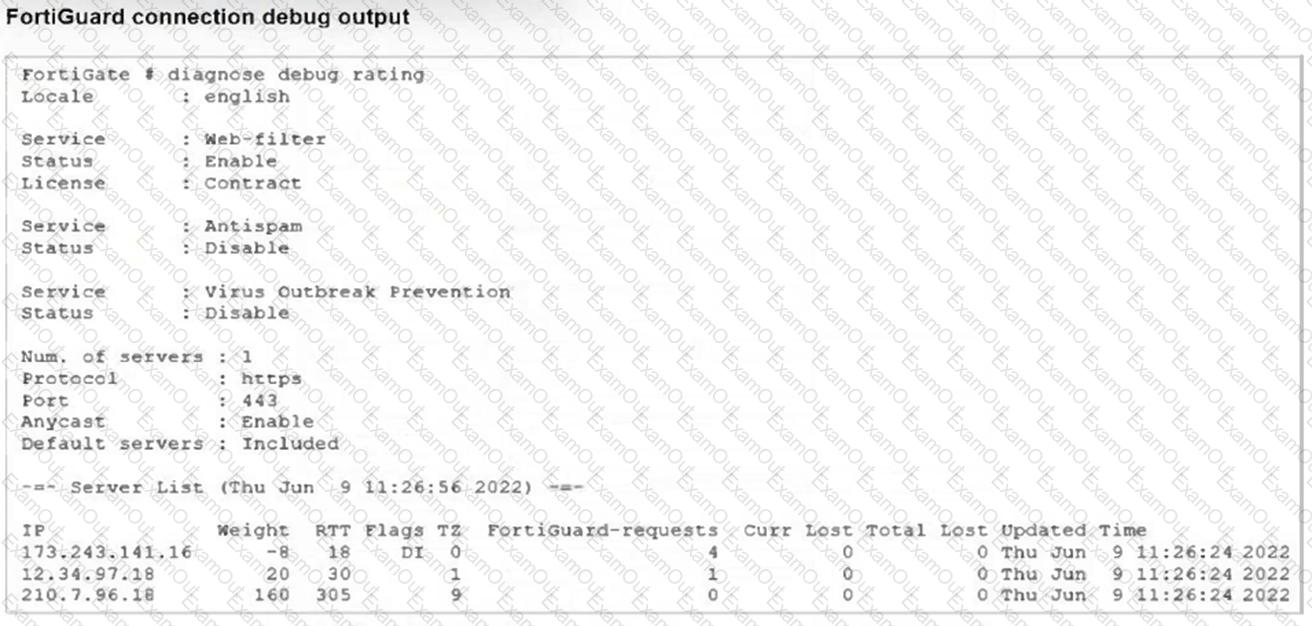
Based on the output, which two facts does the administrator know about the FortiGuard connection? (Choose two.)
Which three strategies are valid SD-WAN rule strategies for member selection? (Choose three.)
Refer to the exhibits.
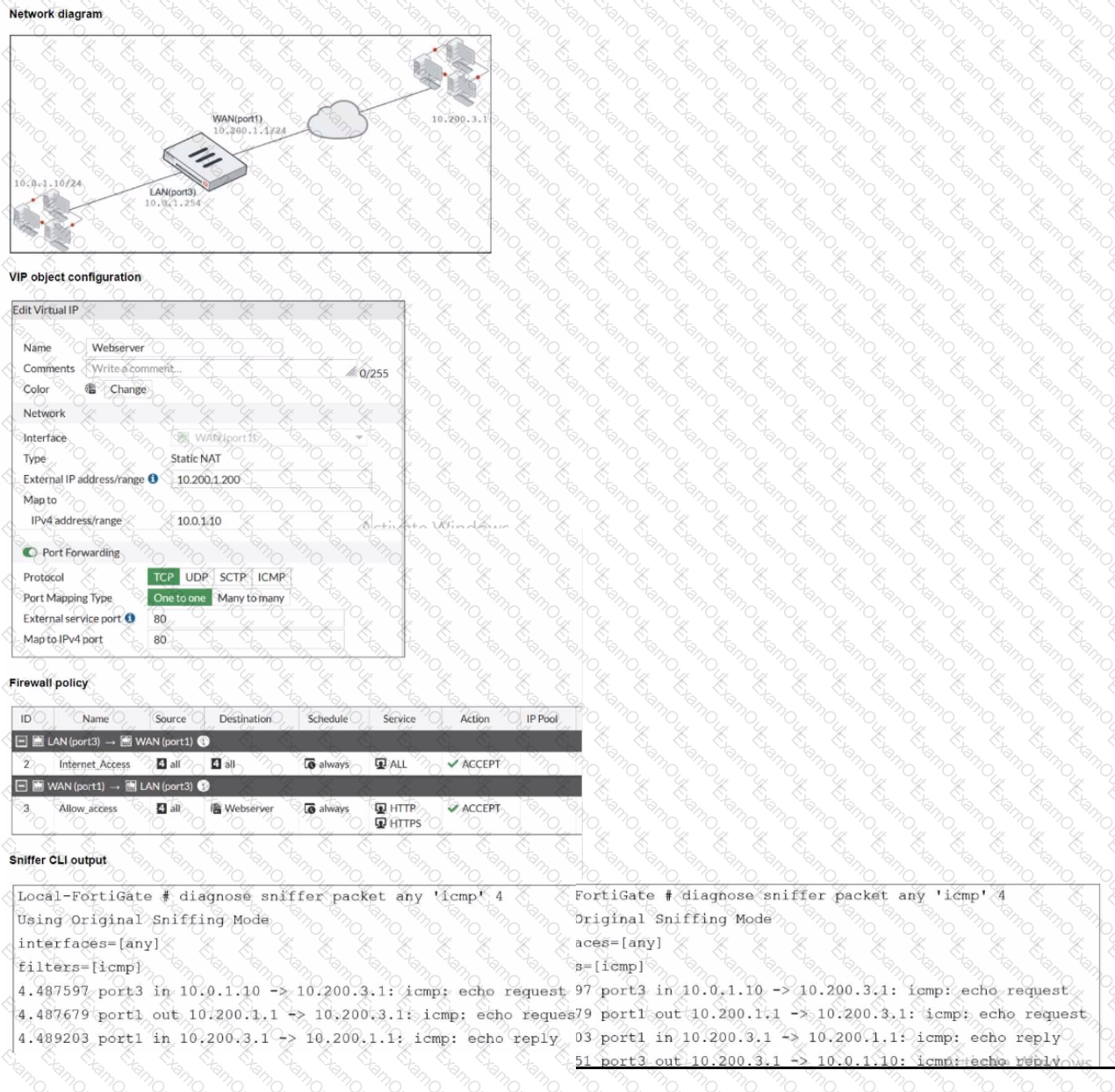
The exhibits show a diagram of a FortiGate device connected to the network, VIP configuration, firewall policy. and the sniffer CLI output on the FortiGate device.
The WAN (port1) interface has the IP address 10.200.1.1 /24.
The LAN (port3) interface has the IP address 10.0.1.254/24.
The webserver host (10. 0.1. 10) must use its VIP external IP address as the source NAT (SNAT) when It pings remote server (10.200.3.1).
Which two statements are valid to achieve this goal? (Choose two.)
FortiGuard categories can be overridden and defined in different categories. To create a web rating override for the example.com home page the override must be configured using a specific syntax.
Which two syntaxes are correct to configure a web rating override for the home page? (Choose two.)
Which two statements are true regarding FortiGate HA configuration synchronization? (Choose two.)
Refer to the exhibit.
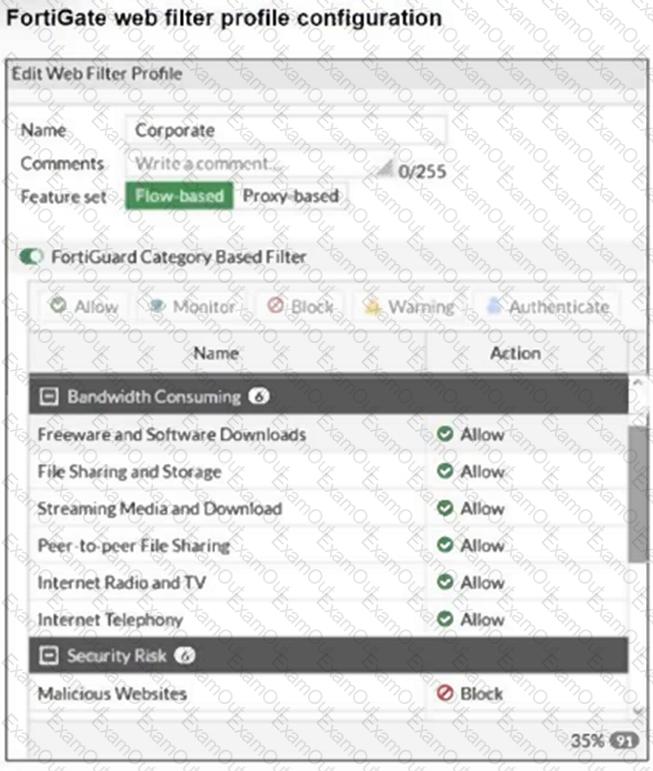
The exhibit shows theFortiGuard Category Based Filtersection of a corporate web filter profile.
An administrator must block access todownload.com, which belongs to theFreeware and Software Downloadscategory. The administrator must also allow other websites in the same category.
What are two solutions for satisfying the requirement? (Choose two.)
Refer to the exhibit.
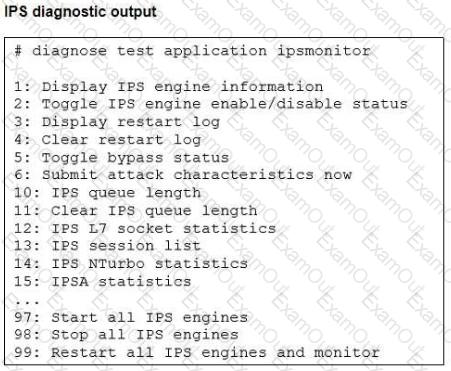
Examine the intrusion prevention system (IPS) diagnostic command shown in the exhibit.
If option 5 is used with the IPS diagnostic command and the outcome is a decrease in the CPU usage, what is the correct conclusion?

