Refer to the exhibits, which show a diagram of a FortiGate device connected to the network. VIP object configuration, and the firewall policy configuration.
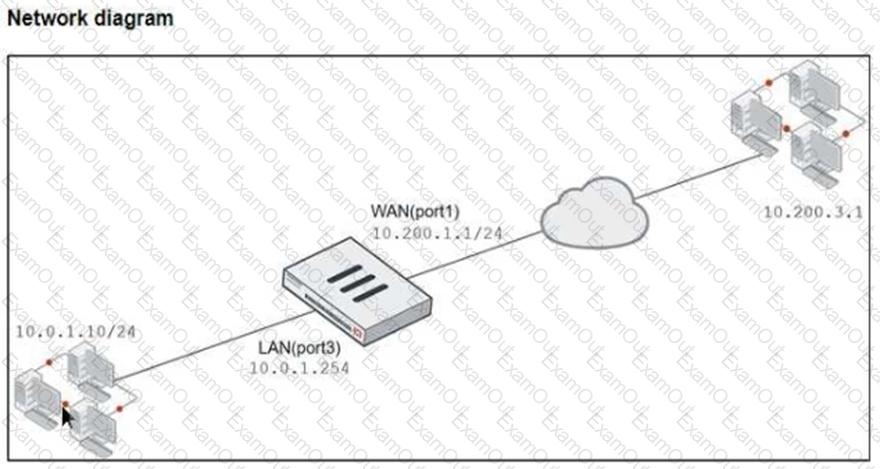


TheWAN (port1)interface has the IP address10.200.1.1/24. TheLAN (port3)interface has the IP address10.0.1.254/24.
If the host10.200.3.1sends a TCP SYN packet on port 8080 to10.200.1.10, what will the source address, destination address, and destination port of the packet be at the time FortiGate forwards the packet to the destination?
Which two settings are required for SSL VPN to function between two FortiGate devices? (Choose two.)
There are multiple dial-up IPsec VPNs configured in aggressive mode on the HQ FortiGate. The requirement is to connect dial-up users to their respective department VPN tunnels.
Which phase 1 setting you can configure to match the user to the tunnel?
Which three CLI commands, can you use to troubleshoot Layer 3 issues if the issue is in neither the physical layer nor the link layer? (Choose three.)
Refer to the exhibits.
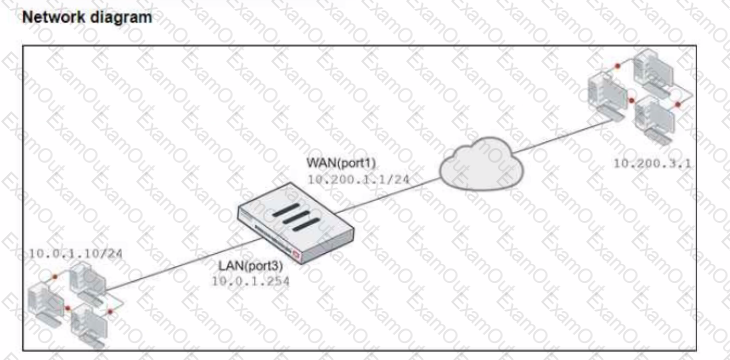
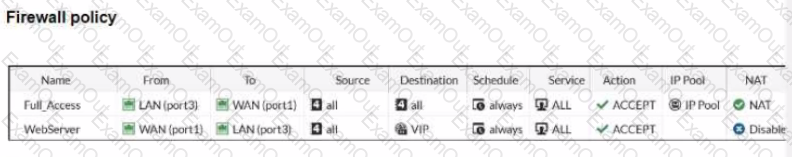
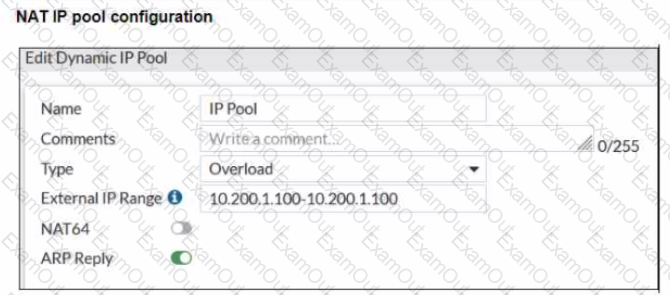
The exhibits show a diagram of a FortiGate device connected to the network, and the firewall policies configuration VIP configuration and IP pool configuration on the FortiGate device
The WAN (port1) interface has the IP address 10.200. l. 1/24 The LAN (port3) interface has the IP address 10.0.1.254/24
The first firewall policy has NAT enabled using the IP pool The second firewall policy is configured with a VIP as the destination address.
Which IP address will be used to source NAT (SNAT) the internet traffic coming from a workstation with the IP address 10.0.1.10?
A network administrator enabled antivirus and selected an SSL inspection profile on a firewall policy.
When downloading an EICAR test file through HTTP, FortiGate detects the virus and blocks the file. When downloading the same file through HTTPS, FortiGate does not detect the
and does not block the file allowing it to be downloaded.
The administrator confirms that the traffic matches the configured firewall policy.
What are two reasons for the failed virus detection by FortiGate? (Choose two.)
Which statement is correct regarding the use of application control for inspecting web applications?
A network administrator has configured an SSL/SSH inspection profile defined for full SSL inspection and set with a private CA certificate. The firewall policy that allows the traffic uses this profile for SSL inspection and performs web filtering. When visiting any HTTPS websites, the browser reports certificate warning errors.
What is the reason for the certificate warning errors?
An administrator configured a FortiGate to act as a collector for agentless polling mode.
What must the administrator add to the FortiGate device to retrieve AD user group information?
Refer to the exhibit.
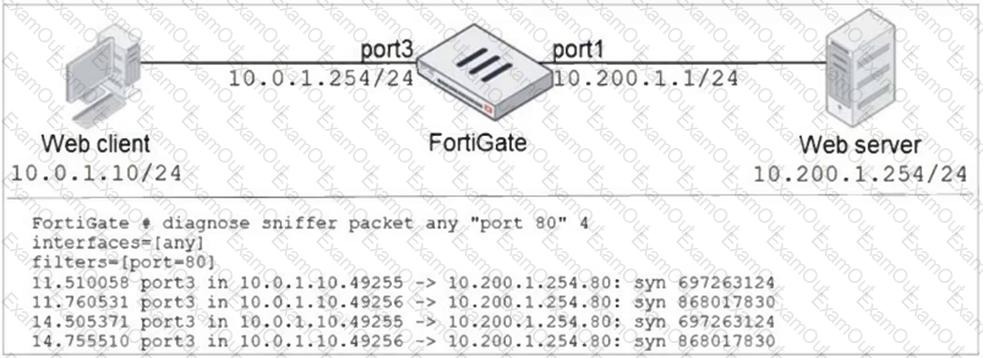
In the network shown in the exhibit, the web client cannot connect to the HTTP web server. The administrator runs the FortiGate built-in sniffer and gets the output shown in the exhibit.
What should the administrator do next, to troubleshoot the problem?

