Refer to the exhibits, which show the system performance output and the default configuration of high memory usage thresholds in a FortiGate.
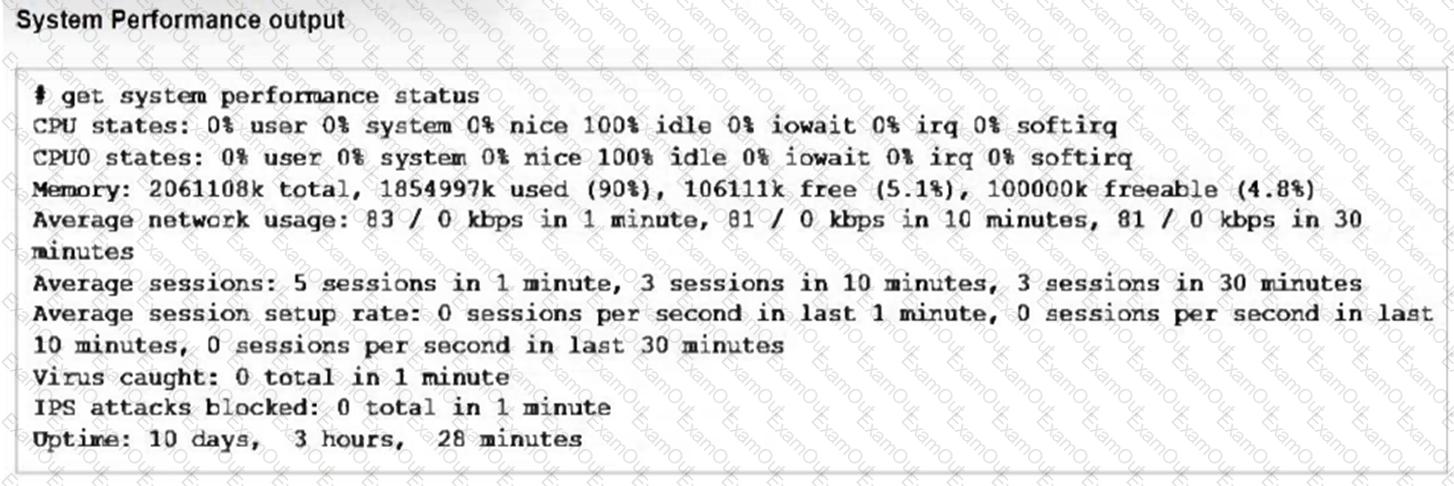
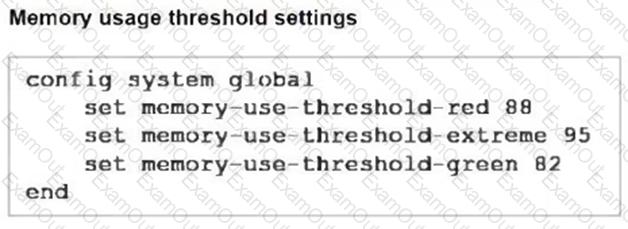
Based on the system performance output, what can be the two possible outcomes? (Choose two.)
How can you disable RPF checking?
Refer to the exhibits.
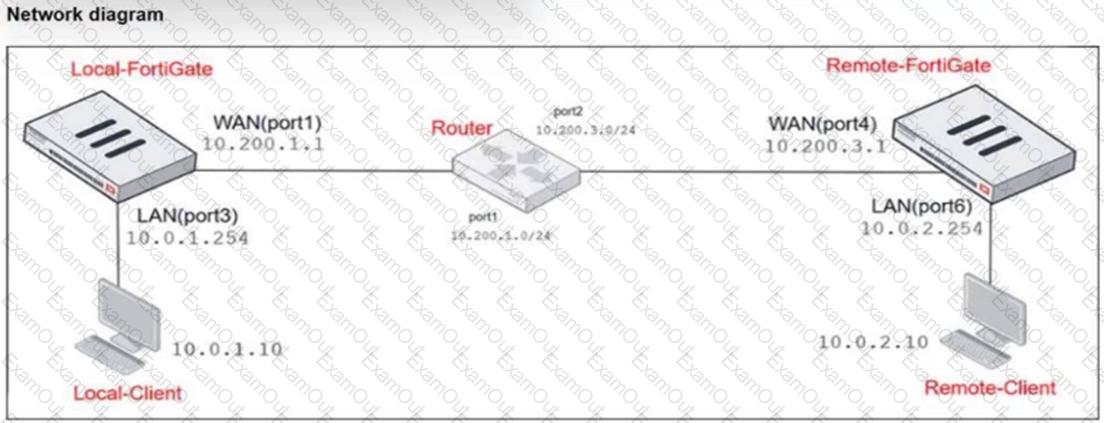
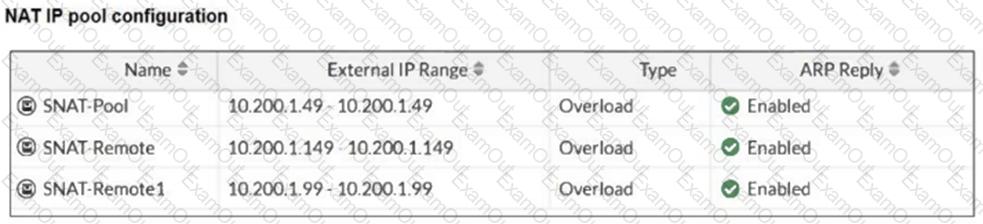

The exhibits show a diagram of a FortiGate device connected to the network, as well as the IP pool configuration and firewall policy objects.
The WAN (port1) interface has the IP address10.200.1.1/24. The LAN (port3) interface has the IPaddress10.0.1.254/24.
Which IP address will be used to source NAT (SNAT) the traffic, if the user on Local-Client (10.0.1.10) pings the IP address of Remote-FortiGate (10.200.3.1)?
Which statement about the deployment of the Security Fabric in a multi-VDOM environment is true?
An organization requires remote users to send external application data running on their PCs and access FTP resources through an SSUTLS connection.
Which FortiGate configuration can achieve this goal?
Refer to the exhibit.
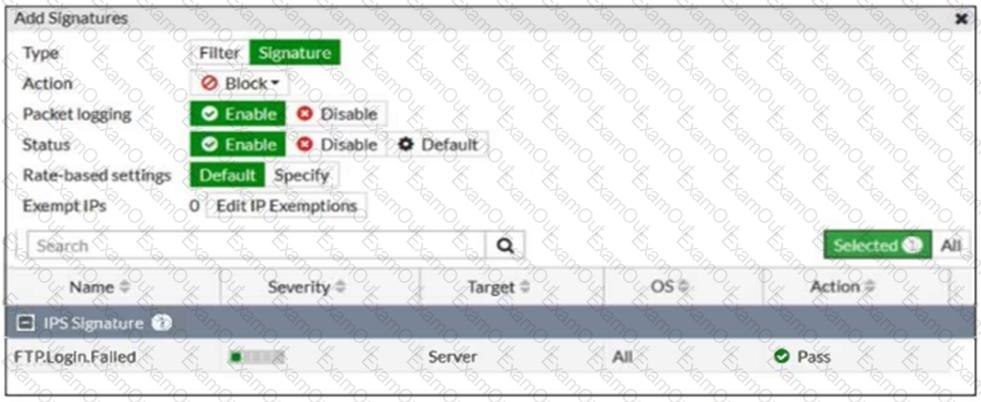
Review the intrusion prevention system (IPS) profile signature settings shown in the exhibit.
What do you conclude when adding theFTP.Login.Failedsignature to the IPS sensor profile?

