Which API endpoint can be used to discover secrets inside of Conjur?
After manually failing over to your disaster recovery site (Site B) for testing purposes, you need to failback to your primary site (Site A).
Which step is required?
When attempting to retrieve a credential, you receive an error 401 – Malformed Authorization Token.
What is the cause of the issue?
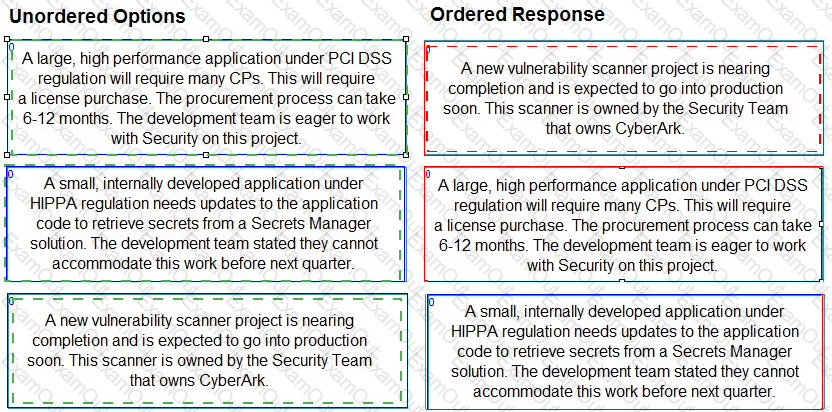
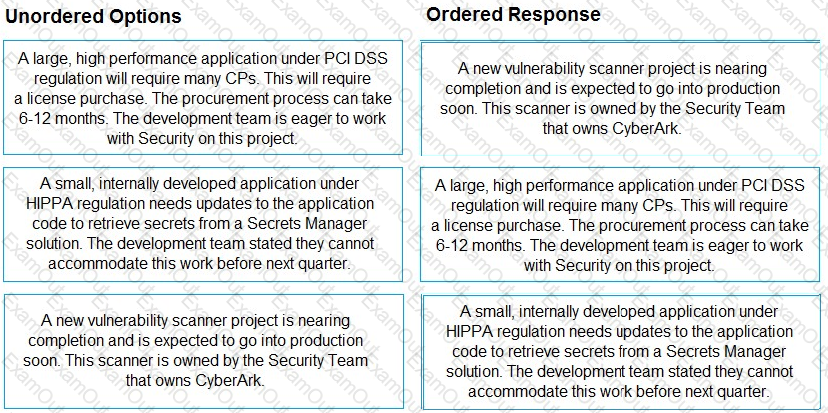
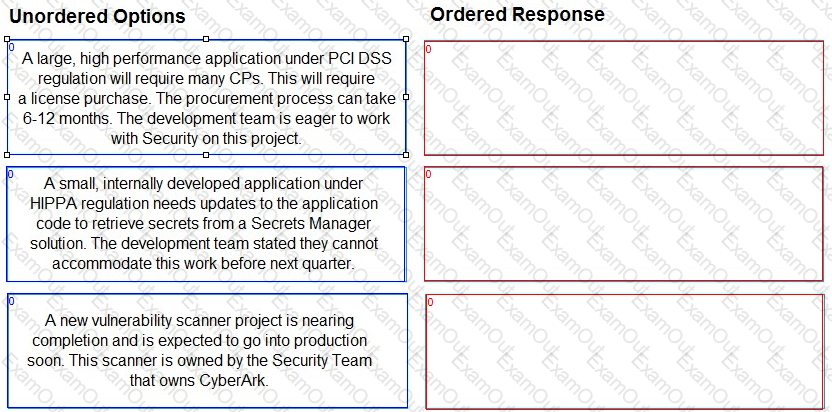
Findings were obtained after cataloging pending Secrets Manager use cases.
Arrange the findings in the correct order for prioritization.
While installing the first CP in an environment, errors that occurred when the environment was created are displayed; however, the installation procedure continued and finished successfully.
What should you do?
When installing the CCP and configuring it for use behind a load balancer, which authentication methods may be affected? (Choose two.)
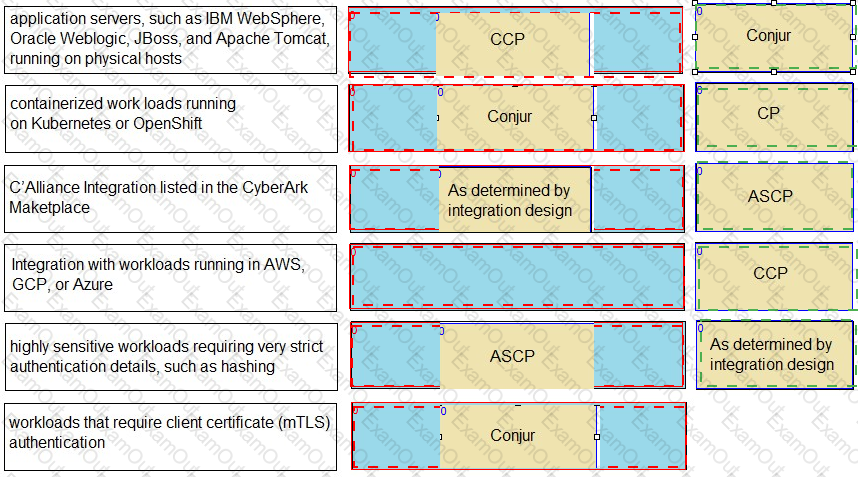
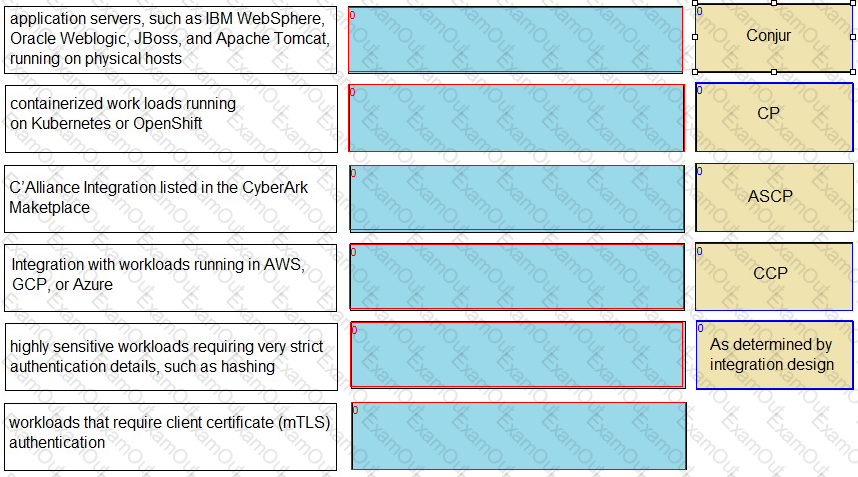
Match each use case to the appropriate Secrets Manager Solution.
Which statement is true for the Conjur Command Line Interface (CLI)?
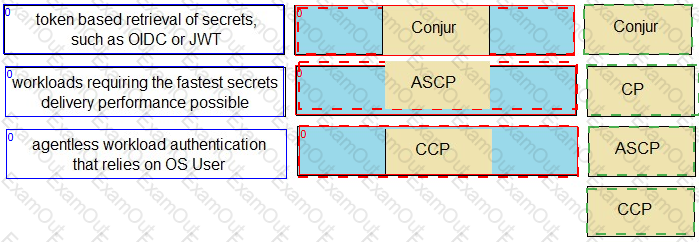
Match each scenario to the appropriate Secrets Manager solution.

What is the correct command to import the root CA certificate into Conjur?