A customer wants to minimize the Kubernetes application code developers must change to adopt Conjur for secrets access.
Which solutions can meet this requirement? (Choose two.)
Refer to the exhibit.
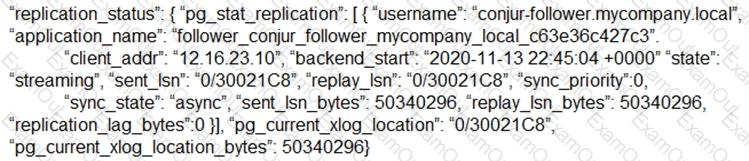
How can you confirm that the Follower has a current copy of the database?
What is a possible Conjur node role change?
You are setting up the Secrets Provider for Kubernetes to support rotation with Push-to-File mode.
Which deployment option should be used?
An application owner reports that their application is suddenly receiving an incorrect password. CPM logs show the password was recently changed, but the value currently being retrieved by the application is a different value. The Vault Conjur Synchronizer service is running.
What is the most likely cause of this issue?
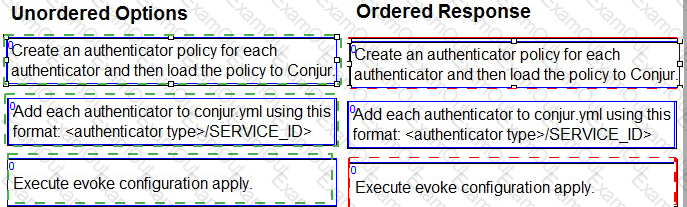
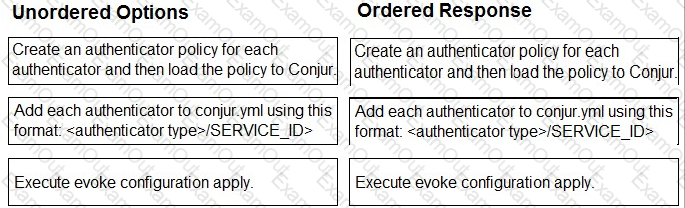
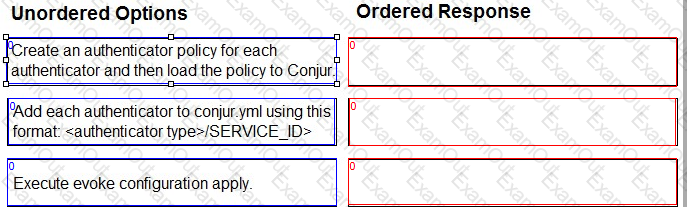
Arrange the steps to configure authenticators in the correct the sequence.
When working with Summon, what is the purpose of the secrets.yml file?
When working with Credential Providers in a Privileged Cloud setting, what is a special consideration?