What should you do if you forget your CyberArk Authenticator PIN?
You want to find all events related to the user with the login ID of "ivan.helen@acme".
Which filter do you enter into the UBA portal data explorer?
Your organization wants to implement passwordless authentication for business critical web applications. CyberArk Identity manages access to these applications.
What can you do to facilitate the enforcement of this passwordless authentication initiative? (Choose two.)
What does enabling "Workflow" allow within an app connector?
Which risk factors contribute to the user behavior risk score? (Choose two.)
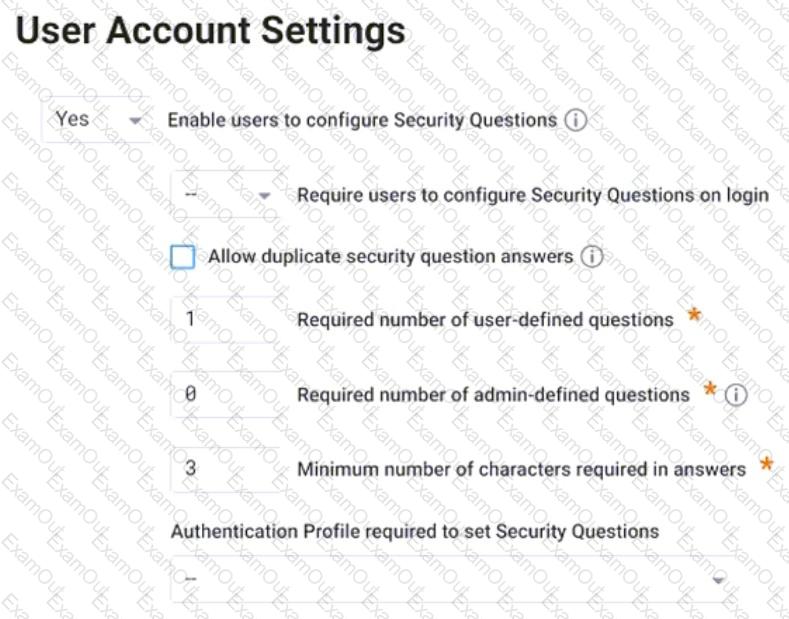
Refer to the exhibit.
Which statement is correct about this configuration shown?
A customer's IT admin asks you to disable CyberArk Identity Connector auto-update software options.
Which statement is correct?
Which administrative right is required to manually start a provisioning synchronization job?
Which settings can help minimize the number of 2FA / MFA prompts? (Choose two.)
Which options are available with Self-Service Password Reset? (Choose three.)

