When can 2FA/MFA be prompted? (Choose two.)
Which CyberArk Identity supported web standard is commonly used for enterprise Single Sign-On and issues XML tokens for authentication?
Cindy just joined a company's IT Audit Department and needs CyberArk Identity access to perform her daily job activities.
Which administrative right(s) should she be assigned to match her job requirement?
When configuring an application to use the App Gateway, you do not have to change any configurations in the application directly. You enable the application for App Gateway access in the Admin Portal and input the existing URL that users enter to open the application. You can either use an external URL that CyberArk Identity automatically generates, or you can continue using an existing internal URL.
What is a disadvantage of using an existing internal URL for App Gateway connections?
Refer to the exhibit.
Which statements are correct regarding this Authentication Policy? (Choose two.)

Which CyberArk Identity service do you use to find a list of pre-built app connectors?
Within a Web App connector, which feature does an admin use to grant users access?
The Security Operation Team requested a report to show users who have logged in the last seven days.
Which report in the Builtin Reports Library should you use?
The Security Operation Team requested a report to show users who have logged in the last seven days.
Which report in the Builtin Reports Library should you use?
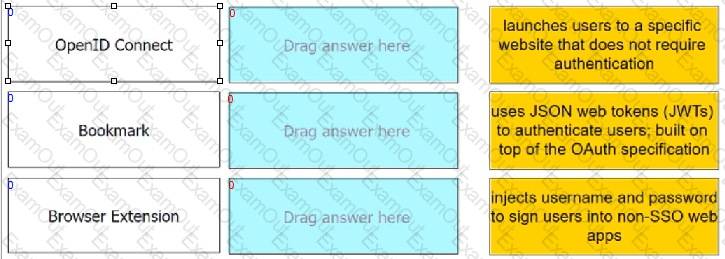
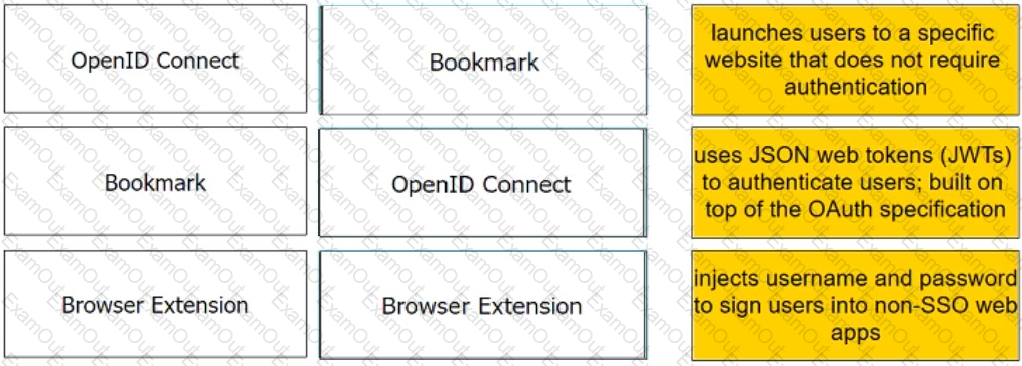
Match each Web App Connector to the phrase that best describes its service offering.