After completing an annual external penetration test, a company receives the following guidance:
Decommission two unused web servers currently exposed to the internet.
Close 18 open and unused ports found on their existing production web servers.
Remove company email addresses and contact info from public domain registration records.
Which of the following does this represent?
A security analyst finds a rogue device during a monthly audit of current endpoint assets that are connected to the network. The corporate network utilizes 002.1X for access control. To be allowed on the network, a device must have a Known hardware address, and a valid user name and password must be entered in a captive portal. The following is the audit report:
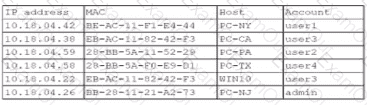
Which of the following is the most likely way a rogue device was allowed to connect?
A security manager is implementing MFA and patch management. Which of the following would best describe the control type and category? (Select two).
A newly appointed board member with cybersecurity knowledge wants the board of directors to receive a quarterly report detailing the number of incidents that impacted the organization. The systems administrator is creating a way to present the data to the board of directors. Which of the following should the systems administrator use?
Which of the following is an example of a data protection strategy that uses tokenization?
Which of the following best explains a concern with OS-based vulnerabilities?
Which of the following activities should a systems administrator perform to quarantine a potentially infected system?
Which of the following technologies must be used in an organization that intends to automate infrastructure deployment?
Which of the following must be considered when designing a high-availability network? (Choose two).
An administrator discovers a cross-site scripting vulnerability on a company website. Which of the following will most likely remediate the issue?
Various company stakeholders meet to discuss roles and responsibilities in the event of a security breach that would affect offshore offices. Which of the following is this an example of?
Which of the following will harden access to a new database system? (Select two)
During the onboarding process, an employee needs to create a password for an intranet account. The password must include ten characters, numbers, and letters, and two special characters. Oncethe password is created, the company will grant the employee access to other company-owned websites based on the intranet profile. Which of the following access management concepts is the company most likely using to safeguard intranet accounts and grant access to multiple sites based on a user's intranet account? (Select two).
A company wants to track modifications to the code used to build new virtual servers. Which of the following will the company most likely deploy?
A government worker secretly copies classified files that contain defense tactics information to an external drive. The government worker then gives the external drive to a corrupt organization. Which of the following best describes the motivation of the worker?

