A network technician is troubleshooting network latency and has determined the issue to be occuring two network switches( Switch10 and Switch11). Symptoms reported included poor video performance and slow file copying. Given the following informtion:
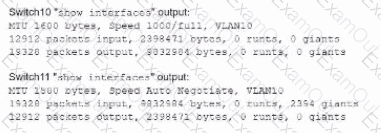
Which of the following should the technician most likely do to resolve the issue?
Which of the following routing protocols uses an autonomous system number?
A junior network technician at a large company needs to create networks from a Class C address with 14 hosts per subnet. Which of the following numbers of host bits is required?
A customer calls the help desk to report issues connection to the internet. The customer can reach a local database server. A technician goes to the site and examines the configuration:
Which of the following is causing the user ' s issue?
Which of the following kinds of targeted attacks uses multiple computers or bots to request the same resource repeatedly?
Which of the following allows a network administrator to analyze attacks coming from the internet without affecting latency?
Which of the following concepts describes the idea of housing different customers in the same public cloud data center?
A network administrator is connecting two Layer 2 switches in a network. These switches must transfer data in multiple networks. Which of the following would fulfill this requirement?
Which of the following OSI model layers manages the exchange of HTTP information?
Which of the following best describes a characteristic of a DNS poisoning attack?

