A computer hardware manufacturer developing a new SoC that will be used by mobile devices. The SoC should not allow users or the process to downgrade from a newer firmware to an older one. Which of the following can the hardware manufacturer implement to prevent firmware downgrades?
An analyst is reviewing the following output as part of an incident:
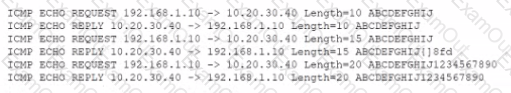
Which of the Wowing is MOST likely happening?
A company wants to ensure a third party does not take intellectual property and build a competing product. Which of the following is a non-technical data and privacy control that would best protect the company?
A company's security team recently discovered a number of workstations that are at the end of life. The workstation vendor informs the team that the product is no longer supported and patches are no longer available The company is not prepared to cease its use of these workstations Which of the following would be the BEST method to protect these workstations from threats?
A security analyst is reviewing a firewall usage report that contains traffic generated over the last 30 minutes in order to locate unusual traffic patterns:
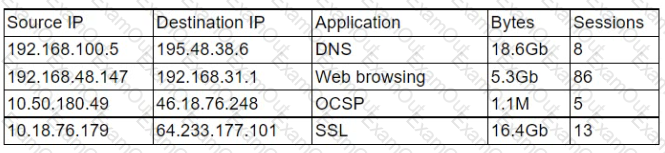
Which of the following source IP addresses does the analyst need to investigate further?
A security analyst found an old version of OpenSSH running on a DMZ server and determined the following piece of code could have led to a command execution through an integer overflow;
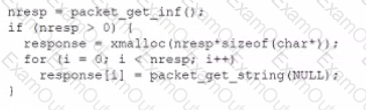
Which of the following controls must be in place to prevent this vulnerability?
A cybersecurity analyst is supporting an Incident response effort via threat Intelligence Which of the following is the analyst most likely executing?
An application must pass a vulnerability assessment to move to the next gate. Consequently, any security issues that are found must be remediated prior to the next gate. Which of the following best describes the method for end-to-end vulnerability assessment?
An analyst is reviewing email headers to determine if an email has been sent from a legitimate sender. The organization uses SPF to validate email origination. Which of the following most likely indicates an invalid originator?
Which of the following should a database administrator for an analytics firm implement to best protect PII from an insider threat?

