A security technician configured a NIDS to monitor network traffic. Which of the following is a condition in which harmless traffic is classified as a potential network attack?
A security analyst identified one server that was compromised and used as a data making machine, and a few of the hard drive that was created. Which of the following will MOST likely provide information about when and how the machine was compromised and where the malware is located?
A software developer is correcting the error-handling capabilities of an application following the initial coding of the fix. Which of the following would the software developer MOST likely performed to validate the code poor to pushing it to production?
Which of the following control types is an organization using when restoring a backup?
A threat feed disclosed a list of files to be used as an loC for a zero-day vulnerability. A cybersecurity analyst decided to include a custom lookup for these files on the endpoint's log-in script as a mechanism to:
White reviewing incident reports from the previous night, a security analyst notices the corporate websites were defaced with po mcai propaganda. Which of the following BEST Describes this type of actor?
A company is building a new internal network. Instead of creating new credentials, the company wants to streamline each employee's authentication. Which of the following technologies would best fulfill this requirement?
Which of me following are reasons why consumer IoT devices should be avoided in an enterprise environment? (Select TWO)
According to a static analysis report for a web application, a dynamic code evaluation script injection vulnerability was found. Which of the following actions is the BEST option to fix the vulnerability in the source code?
During the onboarding process for a new vendor, a security analyst obtains a copy of the vendor's latest penetration test summary:
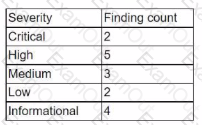
Performed by: Vendor Red Team Last performed: 14 days ago
Which of the following recommendations should the analyst make first?

