A security analyst is investigating a reported phishing attempt that was received by many users throughout the company The text of one of the emails is shown below:
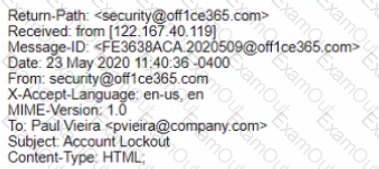
Office 365 User.
It looks like you account has been locked out Please click this link and follow the pfompts to restore access
Regards.
Security Team
Due to the size of the company and the high storage requirements, the company does not log DNS requests or perform packet captures of network traffic, but rt does log network flow data Which of the following commands will the analyst most likely execute NEXT?
An organization is adopting loT devices at an increasing rate and will need to account for firmware updates in its vulnerability management programs. Despite the number of devices being deployed, the organization has only focused on software patches so far. leaving hardware-related weaknesses open to compromise. Which of the following best practices will help the organization to track and deploy trusted firmware updates as part of its vulnerability management programs?
An analyst is reviewing registry keys for signs of possible compromise. The analyst observes the following entries:
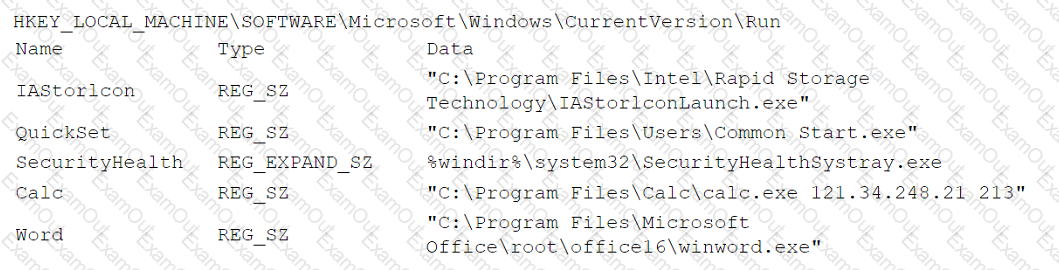
Which of the following entries should the analyst investigate first?
A security analyst discovers suspicious activity going to a high-value corporate asset. After reviewing the traffic, the security analyst identifies that
malware was successfully installed on a machine. Which of the following should be completed first?
An application developer needs help establishing a digital certificate for a new application. Which of the following illustrates a certificate management best practice?
An organization has a policy that requires dedicated user accounts to run programs that need elevated privileges. Users must be part of a group that allows elevated permissions. While reviewing security logs, an analyst sees the following:
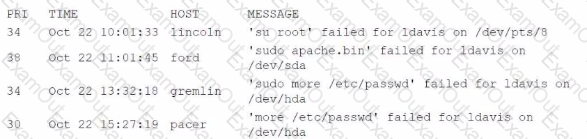
Which of the following hosts violates the organizational policies?
A security analyst is investigating an active threat of the system memory. While narrowing down the source of the threat, the analyst is inspecting all processes to isolate suspicious activity Which of the following techniques is the analyst using?
Which of the following BEST explains the function of trusted firmware updates as they relate to hardware assurance?
Which of the following solutions is the BEST method to prevent unauthorized use of an API?
A security analyst is reviewing the following log entries to identify anomalous activity:
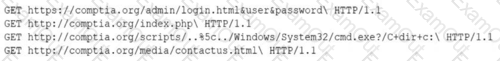
Which of the following attack types is occurring?

