A security analyst discovered requests associated with IP addresses known for born legitimate 3nd bot-related traffic. Which ofthe following should the analyst use to determine whether the requests are malicious?
A security analyst is reviewing the following authentication logs:
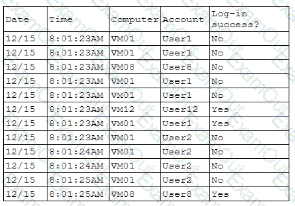
Which of the following should the analyst do first?
A company wants to implement hardware security key authentication for accessing sensitive information systems The goal is to prevent unauthorized users from gaining access with a stolen password Which of the following models should the company implement to b«st solve this issue?
An organization found a significant vulnerability associated with a commonly used package in a variety of operating systems. The organization develops a registry of software dependencies to facilitate incident response activities. As part of the registry, the organization creates hashes of packages that have been formally vetted. Which of the following attack vectors does this registry address?
A systems administrator wants to introduce a newly released feature for an internal application. The administrate docs not want to test the feature in the production environment. Which of the following locations is the best place to test the new feature?
A security operations analyst is reviewing network traffic baselines for nightly database backups. Given the following information:
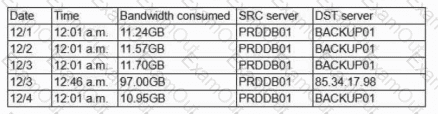
Which of the following should the security analyst do next?
Audit findings indicate several user endpoints are not utilizing full disk encryption During me remediation process, a compliance analyst reviews the testing details for the endpoints and notes the endpoint device configuration does not support full disk encryption Which of the following is the most likely reason me device must be replaced'
During a recentsecurity event, access from thenon-production environment to the production environmentenabledunauthorized usersto:
Installunapproved software
Makeunplanned configuration changes
During theinvestigation, the following findings were identified:
Several new users were added in bulkby theIAM team
Additionalfirewalls and routerswere recently added
Vulnerability assessmentshave been disabled formore than 30 days
Theapplication allow listhas not been modified intwo weeks
Logs were unavailablefor various types of traffic
Endpoints have not been patchedinover ten days
Which of the following actions would most likely need to be taken toensure proper monitoring?(Select two)
A company updates itscloud-based services by saving infrastructure code in a remote repository. The code is automatically deployed into the development environment every time the code is saved lo the repository The developers express concern that the deployment often fails, citing minor code issues and occasional security control check failures in the development environment Which of the following should a security engineer recommend to reduce the deployment failures? (Select two).
A security engineer receives an alert from the SIEM platform indicating a possible malicious action on the internal network. The engineer generates a report that outputs the logs associated with the incident:

Which of the following actions best enables the engineer to investigate further?

