Which of the following best explains the business requirement a healthcare provider fulfills by encrypting patient data at rest?
An organization wants to manage specialized endpoints and needs a solution that provides the ability to
* Centrally manage configurations
* Push policies.
• Remotely wipe devices
• Maintain asset inventory
Which of the following should the organization do to best meet these requirements?
Emails that the marketing department is sending to customers are pomp to the customers' spam folders. The security team is investigating the issue and discovers that the certificates used by the email server were reissued, but DNS records had not been updated. Which of the following should the security team update in order to fix this issue? (Select three.)
A company has the following requirements for a cloud-based web application:
• Must authenticate customers
• Must prevent data exposure
• Must allow customer access to data throughout the cloud environment
• Must restrict access by specific regions
Which of the following solutions best addresses these security requirements?
A SOC analyst is investigating an event in which a penetration tester was able to successfully create and execute a payload. The analyst pulls the following command history from the affected server-
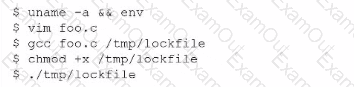
Which of the following should the analyst implement lo improve the security of the server?
Which of the following best describes the reason a network architect would enable forward secrecy on all VPN tunnels?
Which of the following AI concerns is most adequately addressed by input sanitation?
A security professional is investigating a trend in vulnerability findings for newly deployed cloud systems Given the following output:
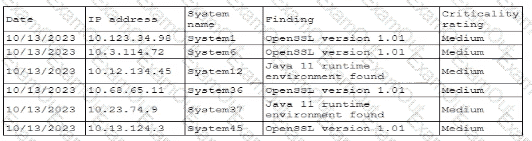
Which of the following actions would address the root cause of this issue?
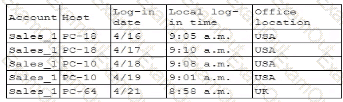
Which of the following is the security engineer most likely doing?
Third partiesnotified a company's security team about vulnerabilities in the company's application. The security team determined these vulnerabilities were previously disclosed in third-party libraries. Which of the following solutions best addresses the reported vulnerabilities?

