Engineers at a cloud service provider can now access newly deployed customer environments from their personal laptops. The engineers are concerned that unmanaged systems may present unknown vulnerabilities to customer environments, which might become a significant liability to the service provider. Which of the following deployments provides the most secure solution to prevent access through non-authorized endpoints?
A company’s internal network is experiencing a security breach, and the threat actor is still active. Due to business requirements, users in this environment are allowed to utilize multiple machines at the same time. Given the following log snippet:
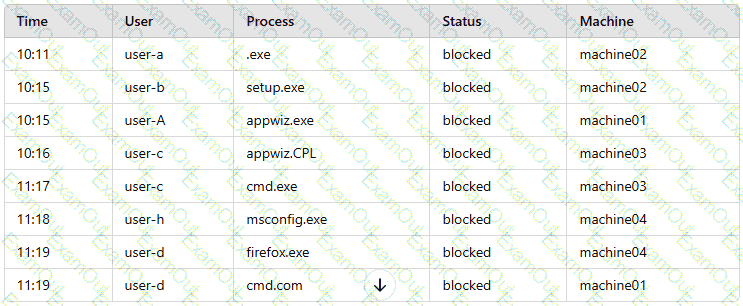
Which of the following accounts should a security analyst disable to best contain the incident without impacting valid users?
A security configure isbuilding a solution to disable weak CBC configuration for remote access connections lo Linux systems. Which of the following should the security engineer modify?
A security engineer is reviewing the following vulnerability scan report:
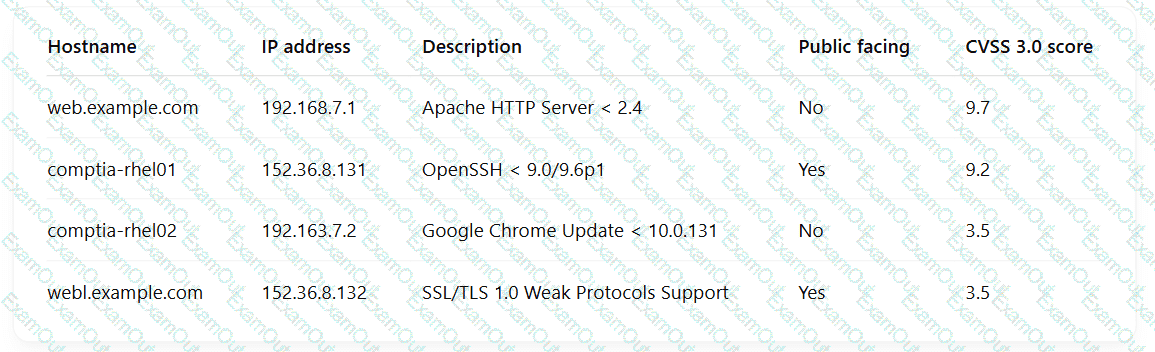
Which of the following should the engineer prioritize for remediation?
An organization recently hired a third party to audit the information security controls present in the environment. After reviewing the audit findings, the Chief Information Security Officer (CISO) approved the budget for an in-depth defense strategy for network security. Which of the following is the most likely reason the CISO approved the additional budget?
A company's Chief Information Security Officer learns that the senior leadership team is traveling to a country accused of attempting to steal intellectual property saved on laptops. Which of the following is the best method to protect against this attack?
During a gap assessment, an organization notes that OYOD usage is asignificant risk. The organization implemented administrative policies prohibiting BYOD usage However, the organization has not implemented technical controls to prevent the unauthorized use of BYOD assets when accessing the organization's resources. Which of the following solutions should the organization implement to b»« reduce the risk of OYOD devices? (Select two).
A security engineer wants to propose an MDM solution to mitigate certain risks. The MDM solution should meet the following requirements:
• Mobile devices should be disabled if they leave the trusted zone.
• If the mobile device is lost, data is not accessible.
Which of the following options should the security engineer enable on the MDM solution? (Select two).
The device event logs sourced from MDM software are as follows:
Device | Date/Time | Location | Event | Description
ANDROID_102 | 01JAN21 0255 | 38.9072N, 77.0369W | PUSH | APPLICATION 1220 INSTALL QUEUED
ANDROID_102 | 01JAN21 0301 | 38.9072N, 77.0369W | INVENTORY | APPLICATION 1220 ADDED
ANDROID_1022 | 01JAN21 0701 | 39.0067N, 77.4291W | CHECK-IN | NORMAL
ANDROID_1022 | 01JAN21 0701 | 25.2854N, 51.5310E | CHECK-IN | NORMAL
ANDROID_1022 | 01JAN21 0900 | 39.0067N, 77.4291W | CHECK-IN | NORMAL
ANDROID_1022 | 01JAN21 1030 | 39.0067N, 77.4291W | STATUS | LOCAL STORAGE REPORTING 85% FULL
Which of the following security concerns and response actions would best address the risks posed by the device in the logs?
Which of the following best describes the challenges associated with widespread adoption of homomorphic encryption techniques?

