A senior security engineer flags the following log file snippet as having likely facilitated an attacker’s lateral movement in a recent breach:
qry_source: 19.27.214.22 TCP/53
qry_dest: 199.105.22.13 TCP/53
qry_type: AXFR
| in comptia.org
------------ directoryserver1 A 10.80.8.10
------------directoryserver2 A 10.80.8.11
------------ directoryserver3 A 10.80.8.12
------------ internal-dns A 10.80.9.1
----------- www-int A 10.80.9.3
------------ fshare A 10.80.9.4
------------ sip A 10.80.9.5
------------ msn-crit-apcs A 10.81.22.33
Which of the following solutions, if implemented, would mitigate the risk of this issue reoccurring?
Which of the following are risks associated with vendor lock-in? (Select two).
The identity and access management team is sending logs to the SIEM for continuous monitoring. The deployed log collector isforwarding logs to
the SIEM. However, only false positive alerts are being generated. Which of the following is the most likely reason for the inaccurate alerts?
Which of the following best explains the business requirement a healthcare provider fulfills by encrypting patient data at rest?
Company A acquired Company B. During an audit, a security engineer found Company B's environment was inadequately patched. In response, Company A placed a firewall between the two environments until Company B's infrastructure could be integrated into Company A's security program. Which of the following risk-handling techniques was used?
Emails that the marketing department is sending to customers are going to the customers' spam folders. The security team is investigating the issue and discovers that the certificates used by the email server were reissued, but DNS records had not been updated. Which of the following should the security team update in order to fix this issue? (Select three).
A company was recently infected by malware. During the root cause analysis, the company determined that several users were installing their own applications. To prevent further compromises, the company has decided it will onlyallow authorized applications to run on its systems. Which of the following should the company implement?
An analyst wants to conduct a risk assessment on a new application that is being deployed. Given the following information:
• Total budget allocation for the new application is unavailable.
• Recovery time objectives have not been set.
• Downtime loss calculations cannot be provided.
Which of the following statements describes the reason a qualitative assessment is the best option?
After an incident response exercise, a security administrator reviews the following table:
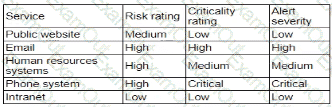
Which of the following should the administrator do to beat support rapid incident response in the future?
A company needs to quickly assess whether software deployed across the company's global corporate network contains specific software libraries. Which of the following best enables the company's SOC to respond quickly when such an assessment is required?

