A security administrator is reviewing the following code snippet from a website component:

A review of the inc.tmp file shows the following:
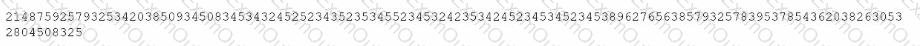
Which of the following is most likely the reason for inaccuracies?
A company’sSIEMis designed to associate the company’sasset inventorywith user events. Given the following report:
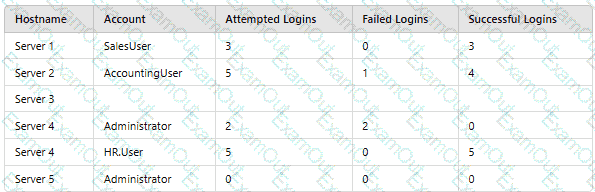
Which of thefollowing should asecurity engineer investigate firstas part of alog audit?
An organization wants to create a threat model to identity vulnerabilities in its infrastructure. Which of the following, should be prioritized first?
A security analyst notices a number of SIEM events that show the following activity:
10/30/2020 - 8:01 UTC - 192.168.1.1 - sc stop HinDctend
10/30/2020 - 8:05 UTC - 192.168.1.2 - c:\program files\games\comptidcasp.exe
10/30/2020 - 8:07 UTC - 192.168.1.1 - c:\windows\system32\cmd.exe /c powershell
10/30/2020 - 8:07 UTC - 192.168.1.1 - powershell —> 40.90.23.154:443
Which of the following response actions should the analyst take first?
A financial services organization is using Al lo fully automate the process of deciding client loan rates Which of the following should the organization be most concerned about from a privacy perspective?
A security analystreviews the following report:
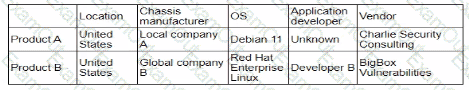
Which of the following assessments is the analyst performing?
While investigating a security event an analyst finds evidence that a user opened an email attachment from an unknown source. Shortly after the user opened the attachment, a group of servers experienced a large amount of network and resource activity. Upon investigating the servers, the analyst discovers the servers were encrypted by ransomware that is demanding payment within 48 hours or all data will be destroyed. The company has no response plans for ransomware. Which of the following is the next step the analyst should take after reporting the incident to the management team?
An analyst reviews a SIEM and generates the following report:
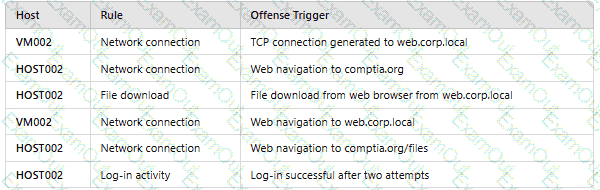
OnlyHOST002is authorized for internet traffic. Which of the following statements is accurate?
An organization recently experienced a security incident due to an exterior door in a busy area getting stuck open. The organization launches a security campaign focused on the motto, "See Something, Say Something." Which of the following best describes what the organization wants to educate employees about?
A security engineer needs 10 secure the OT environment based on me following requirements
• Isolate the OT network segment
• Restrict Internet access.
• Apply security updates two workstations
• Provide remote access to third-party vendors
Which of the following design strategies should the engineer implement to best meetthese requirements?

