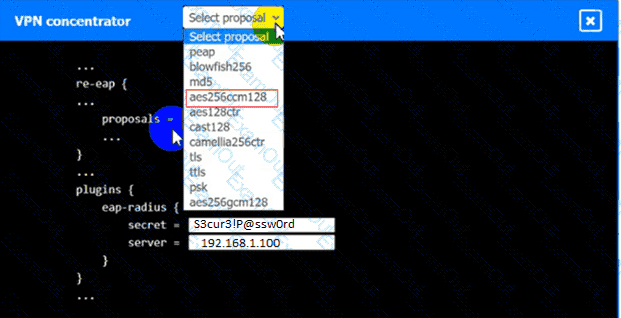
An IPSec solution is being deployed. The configuration files for both the VPN
concentrator and the AAA server are shown in the diagram.
Complete the configuration files to meet the following requirements:
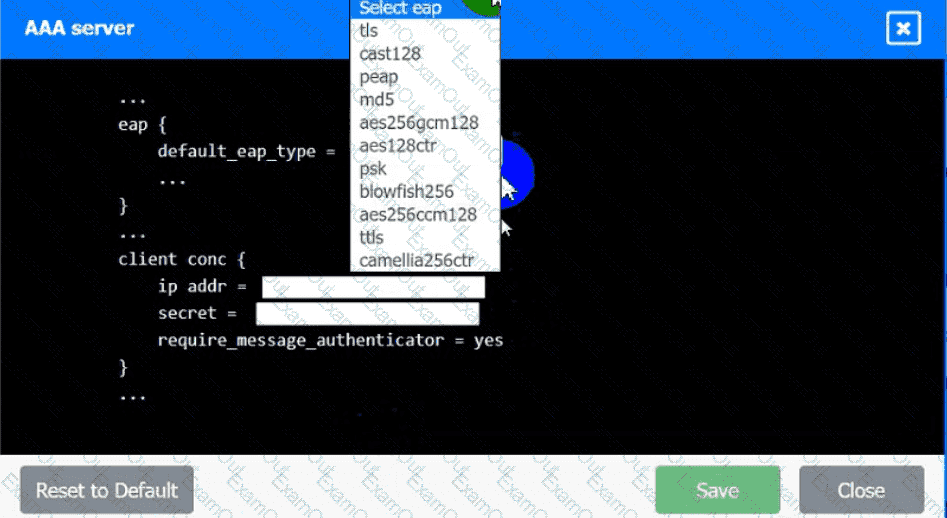
• The EAP method must use mutual certificate-based authentication (With
issued client certificates).
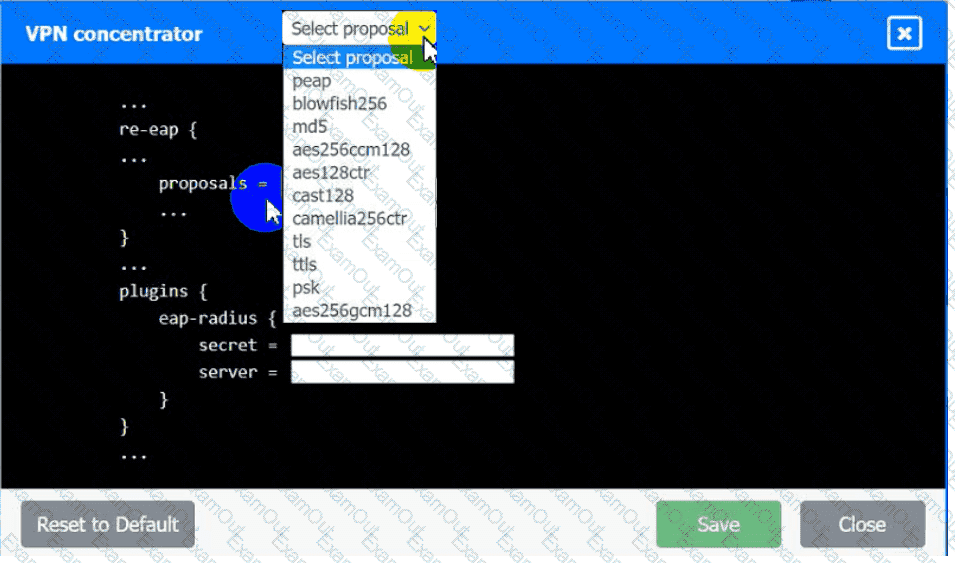
• The IKEv2 Cipher suite must be configured to the MOST secure
authenticated mode of operation,
• The secret must contain at least one uppercase character, one lowercase
character, one numeric character, and one special character, and it must
meet a minimumlength requirement of eight characters,
INSTRUCTIONS
Click on the AAA server and VPN concentrator to complete the configuration.
Fill in the appropriate fields and make selections from the drop-down menus.
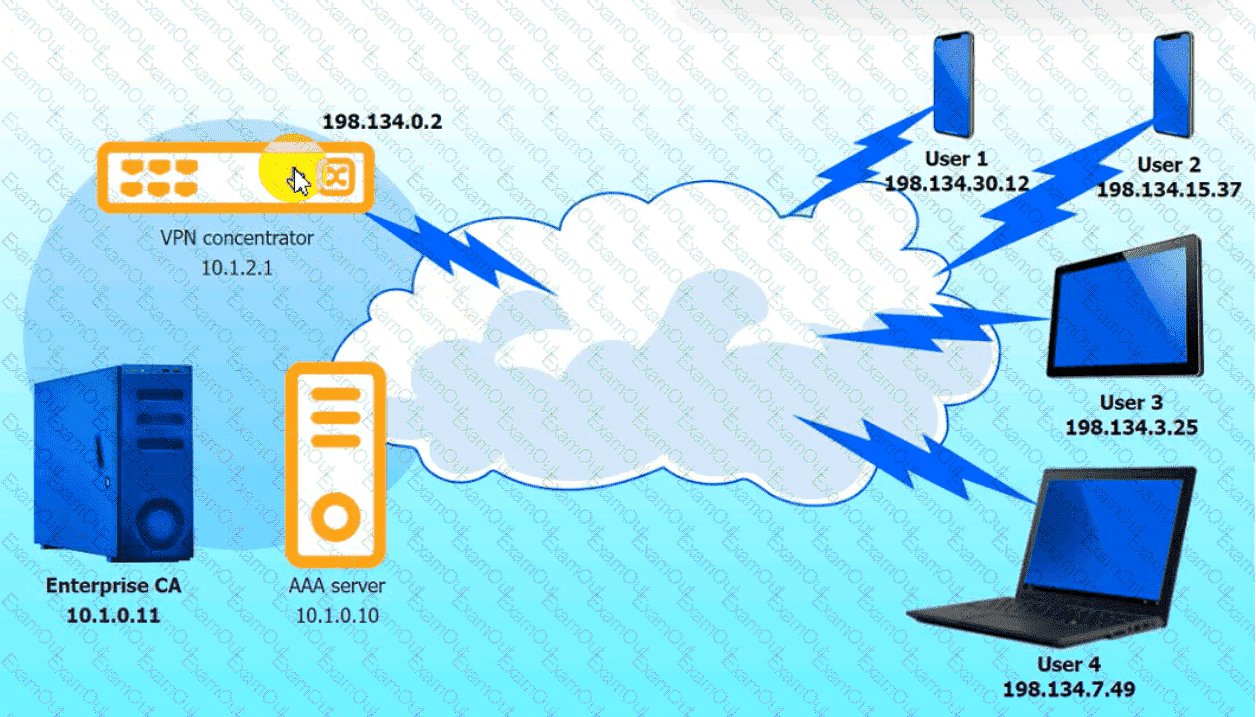
VPN Concentrator:
AAA Server:
A security engineer wants to reduce the attack surface of a public-facing containerized application Which of the following will best reduce the application's privilege escalation attack surface?
A company is having issues with its vulnerability management program New devices/lPs are added and dropped regularly, making the vulnerability report inconsistent Which of the following actions should the company lake to most likely improve the vulnerability management process'
A company discovers intellectual property data on commonly known collaboration web applications that allow the use of slide templates. The systems administrator is reviewing the configurations of each tool to determine how to prevent this issue. The following security solutions are deployed:
CASB
SASE
WAF
EDR
Firewall
IDS
SIEM
DLP endpoints
Which of the following should the administrator do to address the issue?
A vulnerability can on a web server identified the following:
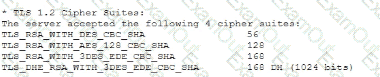
Which of the following actions would most likely eliminate on path decryption attacks? (Select two).
An organization must provide access to its internal system data. The organization requires that this access complies with the following:
Access must be automated.
Data confidentiality must be preserved.
Access must be authenticated.
Data must be preprocessed before it is retrieved.
Which of the following actions should the organization take to meet these requirements?
A company that uses containers to run its applications is required to identify vulnerabilities on every container image in a private repository The security team needs to be able to quickly evaluate whether to respond to a given vulnerability Which of the following, will allow the security team to achieve the objective with the last effort?
A user reports application access issues to the help desk. The help desk reviews the logs for the user:
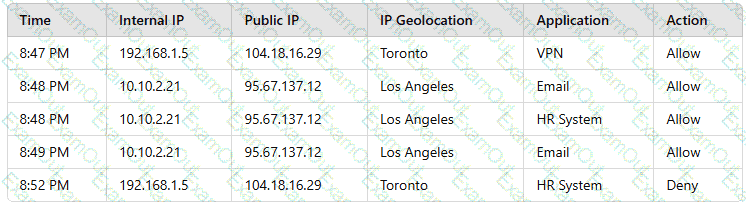
Which of the following is most likely the reason for the issue?
Developers have been creating and managing cryptographic material on their personal laptops fix use in production environment. A security engineer needs to initiate a more secure process. Which of thefollowing is the best strategy for the engineer to use?
A company plans to implement a research facility with Intellectual property data that should be protected The following is the security diagram proposed by the security architect
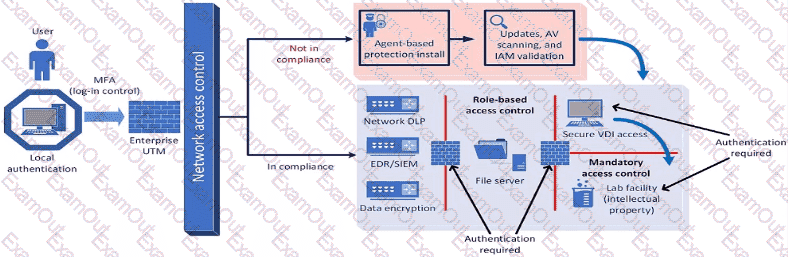
Which of the following security architect models is illustrated by the diagram?

 A screenshot of a computer Description automatically generated
A screenshot of a computer Description automatically generated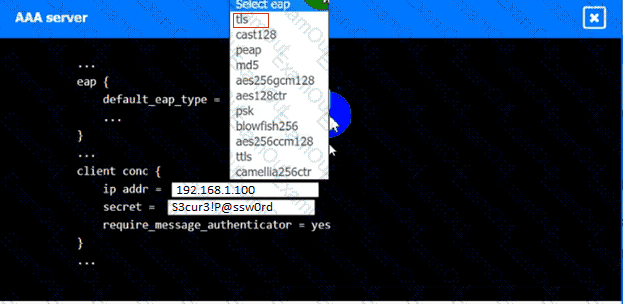 A screenshot of a computer Description automatically generated
A screenshot of a computer Description automatically generated