A systems administrator works with engineers to process and address vulnerabilities as a result of continuous scanning activities. The primary challenge faced by the administrator is differentiating between valid and invalid findings. Which of the following would the systems administrator most likely verify is properly configured?
An enterprise is deploying APIs that utilize a private key and a public key to ensure the connection string is protected. To connect to the API, customers must use the private key. Which of the following would best secure the REST API connection to the database while preventing the use of a hard-coded string in the request string?
A security analyst isreviewing the following event timeline from an COR solution:
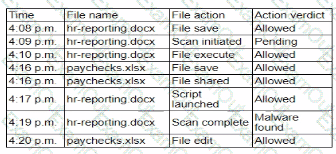
Which of the following most likely has occurred and needs to be fixed?
A security architect must make sure that the least number of services as possible is exposed in order to limit an adversary's ability to access the systems. Which of the following should the architect do first?
A security analyst is reviewing the following code in the public repository for potential risk concerns:
typescript
CopyEdit
include bouncycastle-1.4.jar;
include jquery-2.0.2.jar;
public static void main() {...}
public static void territory() { ... }
public static void state() { ... }
public static String code = "init";
public static String access_token = "spat-hfeiw-sogur-werdb-werib";
Which of the following should the security analyst recommend first to remediate the vulnerability?
A security engineer reviews an after action report from a previous security breach and notes a long lag time between detection and containment of a compromised account. The engineer suggests using SOAR to address this concern. Which of the following best explains the engineer's goal?
A global organization is reviewing potential vendors to outsource a critical payroll function. Each vendor's plan includes using local resources in multiple regions to ensure compliance with all regulations. The organization's Chief Information Security Officer is conducting a risk assessment on the potential outsourcing vendors' subprocessors. Which of the following best explains the need for this risk assessment?
A user from the sales department opened a suspicious file attachment. The sales department then contacted the SOC to investigate a number of unresponsive systems, and the team successfully identified the file and the origin of the attack. Which of the following is the next step of the incident response plan?
Consultants for a company learn that customs agents at foreign border crossings are demanding device inspections. The company wants to:
• Minimize the risk to its data by storing its most sensitive data inside of a security container.
• Obfuscate containerized data on command.
Which of the following technologies is the best way to accomplish this goal?
Within a SCADA a business needs access to the historian server in order together metric about the functionality of the environment. Which of the following actions should be taken to address this requirement?

