An organization is developing a disaster recovery plan that requires data to be backed up and available at a moment's notice. Which of the following should the organization consider first to address this requirement?
Previously intercepted communications must remain secure even if a current encryption key is compromised in the future. Which of the following best supports this requirement?
A security architect is troubleshooting an issue with an OIDC implementation. The architect reviews the following configuration and errors:
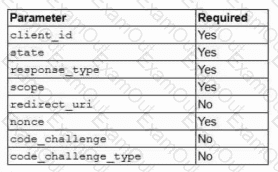
Error: Invalid authentication request code
Which of the following is the most likely cause of the error?
A security operations engineer needs to prevent inadvertent data disclosure when encrypted SSDs are reused within an enterprise. Which of the following is the most secure way to achieve this goal?
A malicious actor exploited firmware vulnerabilities and used rootkits in an attack on an organization. After the organization recovered from the incident, an engineer needs to recommend a solution that reduces the likelihood of the same type of attack in the future. Which of the following is the most relevant solution?
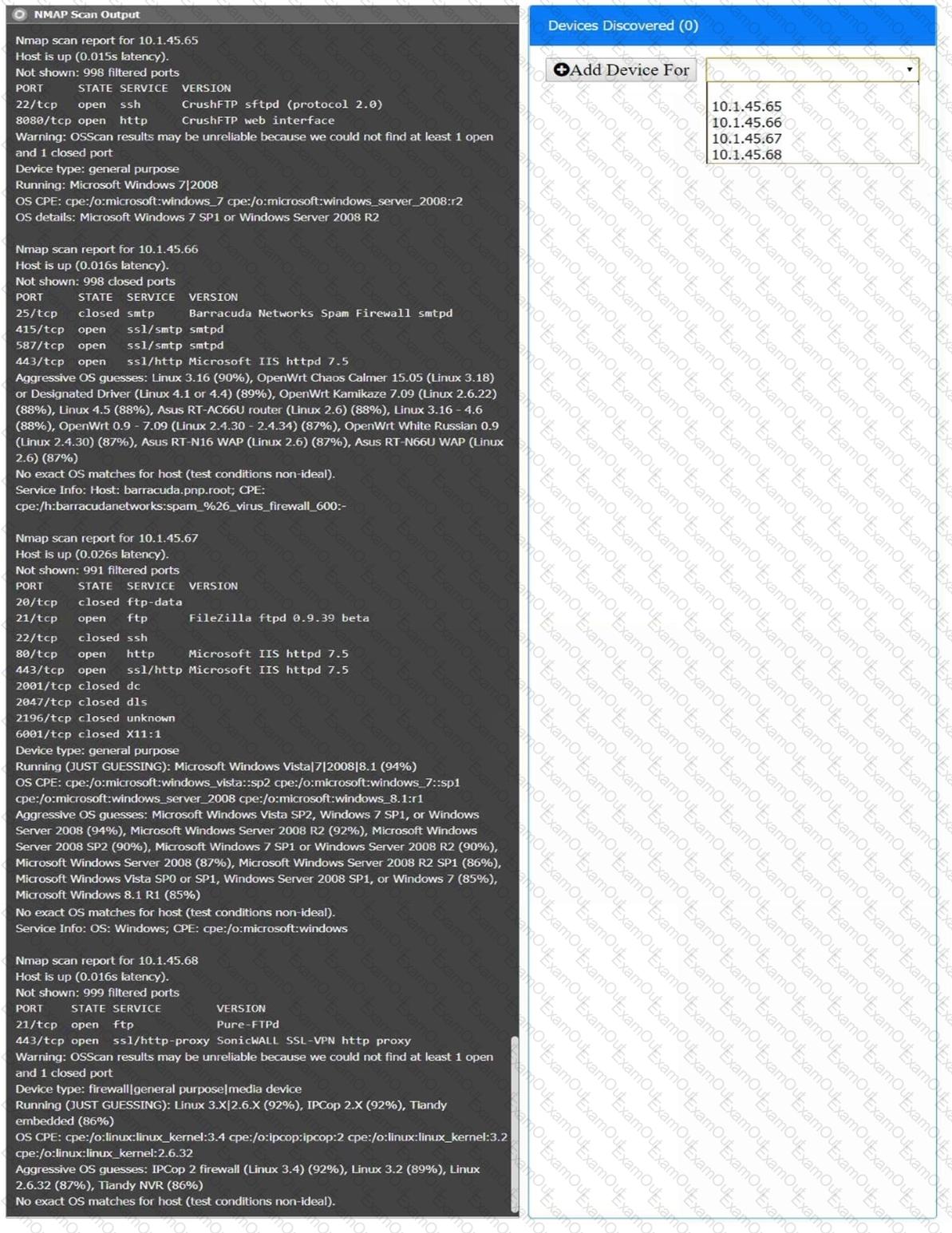
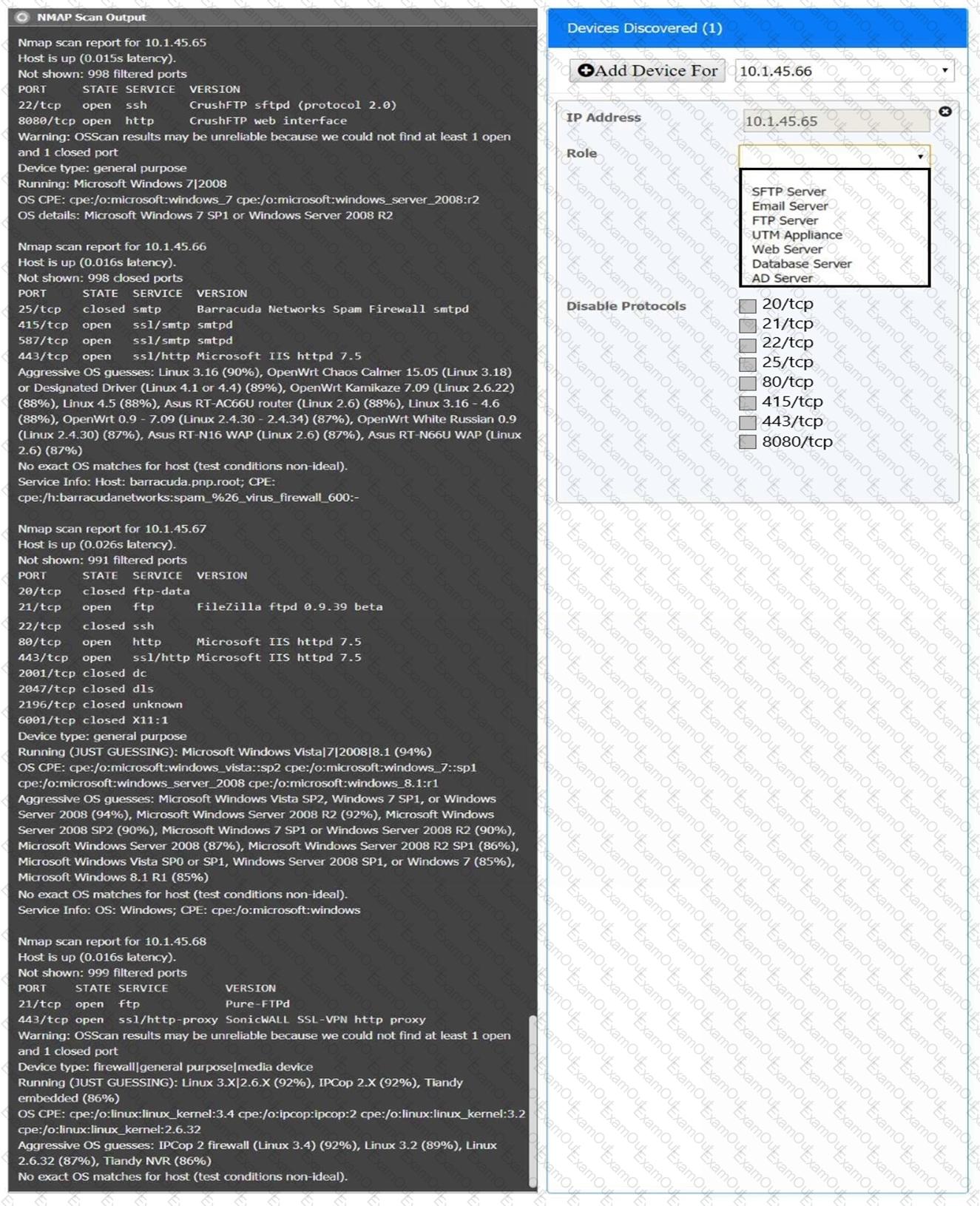
You are a security analyst tasked with interpreting an Nmap scan output from company’s privileged network.
The company’s hardening guidelines indicate the following:
There should be one primary server or service per device.
Only default ports should be used.
Non-secure protocols should be disabled.
INSTRUCTIONS
Using the Nmap output, identify the devices on the network and their roles, and any open ports that should be closed.
For each device found by Nmap, add a device entry to the Devices Discovered list, with the following information:
The IP address of the device
The primary server or service of the device (Note that each IP should by associated with one service/port only)
The protocol(s) that should be disabled based on the hardening guidelines (Note that multiple ports may need to be closed to comply with the hardening guidelines)
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
All organization is concerned about insider threats from employees who have individual access to encrypted material. Which of the following techniques best addresses this issue?
After discovering that an employee is using a personal laptop to access highly confidential data, a systems administrator must secure the company's data. Which of the following capabilities best addresses this situation?
Company A acquired Company B and needs to determine how the acquisition will impact the attack surface of the organization as a whole. Which of the following is the best way to achieve this goal? (Select two).
Implementing DLP controls preventing sensitive data from leaving Company B's network
After a penetration test on the internal network, the following report was generated:
Attack Target Result
Compromised host ADMIN01S.CORP.LOCAL Successful
Hash collected KRBTGT.CORP.LOCAL Successful
Hash collected SQLSV.CORP.LOCAL Successful
Pass the hash SQLSV.CORP.LOCAL Failed
Domain control CORP.LOCAL Successful
Which of the following should be recommended to remediate the attack?

