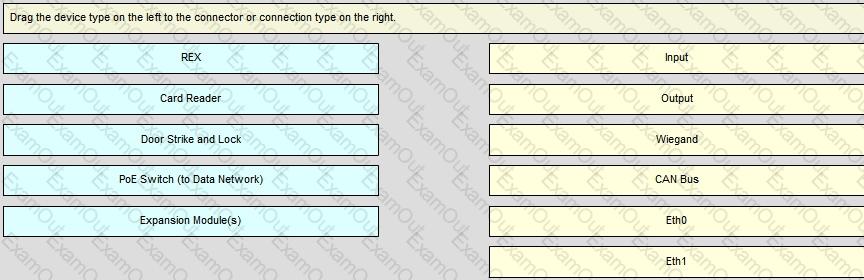
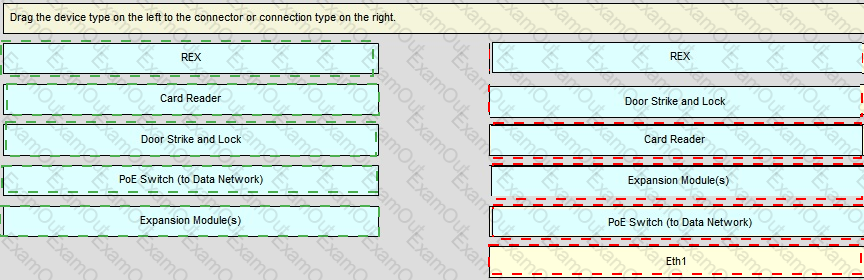
What are the four main components of a typical logical door?
What are the three common methods that are used for authentication with an access control system?
When a 24 VDC fail safe lock is being used to secure a door, how should power be supplied to the lock from the control source?
In Cisco PAM 1.3.2, what is the maximum size of a database backup file?
In Cisco PAM, how do you configure items such as DNS, system upgrades, and rebooting of the server?
Which one of the following image formats cannot be used as a background image in the graphical map editor in Cisco PAM?
Which of the following capabilities will cease to function if network connectivity is lost between the Cisco PAM Server and the Cisco Access Gateway?
You need to design a 31-door, networked Cisco Physical Access Control Gateway system. Each door will be controlled by a Cisco Access Gateway, and each Cisco Access Gateway will require its own IP address. Due to the limited number of available IP addresses, the network admin has decided to implement variable-length subnet mask (VLSM) in order to better allocate the available address space. What is the most efficient subnet mask that can be used to handle the 31 IP addresses that are needed for the Cisco Access Gateways?
On a converged network infrastructure, which Layer 2 technology can be easily enabled and configured to ensure separation of Cisco Physical Access Control Gateway traffic on the network from other "normal" data traffic (for example, IP voice, e-mails, and web browsing)?