What is the role of the Meraki Dashboard as the service provider when using SAML for single sign-on to the Dashboard?
Which Meraki Dashboard menu section is accessed to enable Sentry enrollment on an SSID?
Refer to the exhibit.
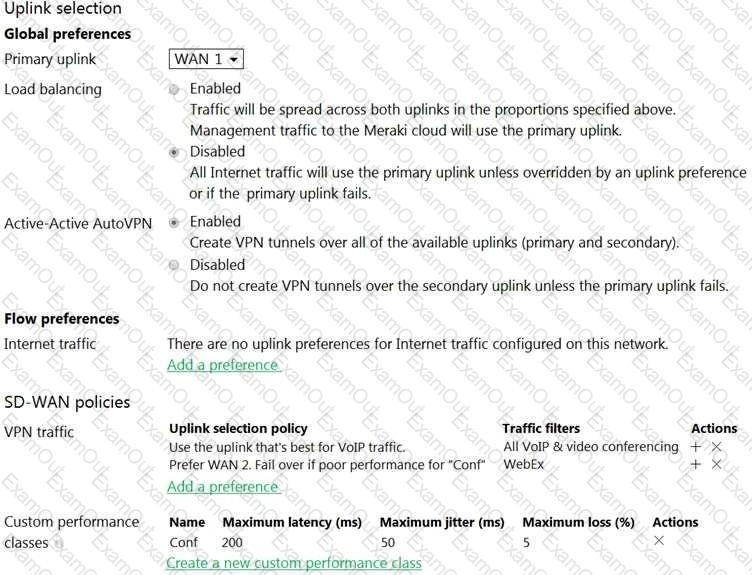
Assuming this MX has established a full tunnel with its VPN peer, how will the MX route the WebEx traffic?
Which Cisco Meraki product must be deployed in addition to Systems Manager so that Systems Manager Sentry enrollment can be used?
Refer to the exhibit.
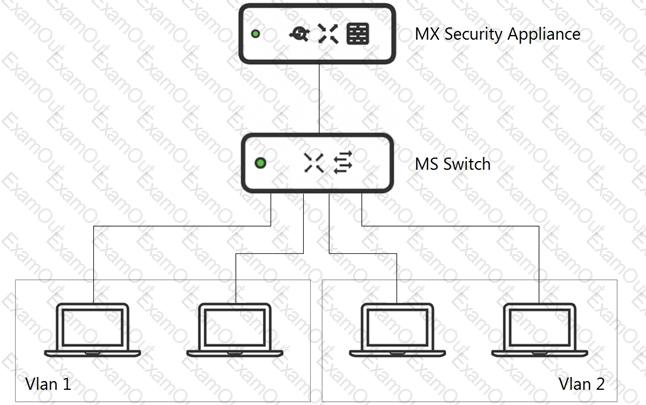
What is an advantage of implementing inter-VLAN routing on an MX Security Appliance rather than performing inter-VLAN routing on an MS Series Switch?
Which two features and functions are supported when using an MX appliance in Passthrough mode? (Choose two.)
What are two ways peers interact with ports that Auto VPN uses? (Choose two.)
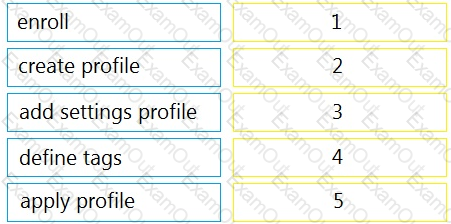
Drag and drop the steps from the left into the sequence on the right to manage device control, according to Cisco Meraki best practice.
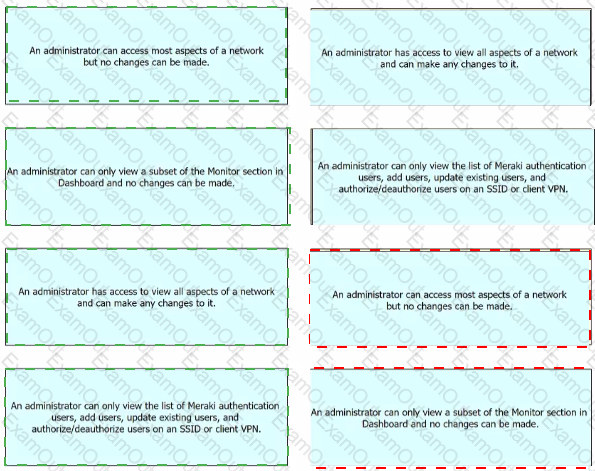
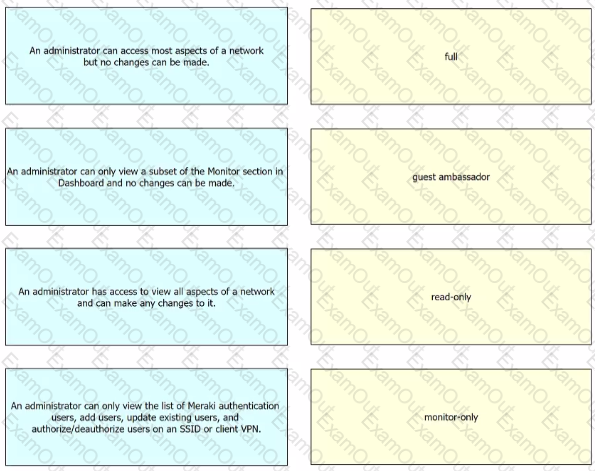
Drag and drop the descriptions from the left onto the permission types on the right.
Refer to the exhibit.
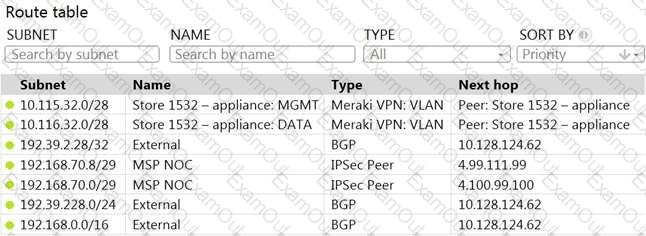
A packet arrives on the VPN concentrator with source IP 10.168.70.3 and destined for IP 10.116.32.4.
What is the next hop for the packet, based on this concentrator routing table?

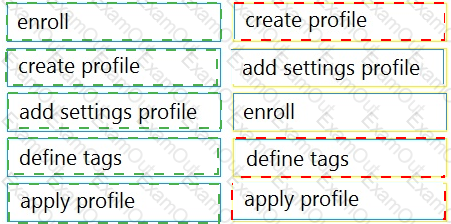
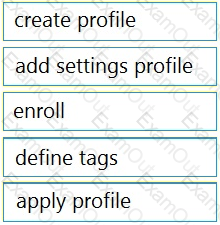 Table
Description automatically generated with medium confidence
Table
Description automatically generated with medium confidence