What is an advantage of placing the IS-IS flooding domain boundary at the core Layer in a three-layer hierarchical network?
In a network with dynamic mutual redistribution between multiple OSPFv2 and EIGRP boundaries, which two mechanisms avoid suboptimal routing? (Choose two)
Which two conditions are required for successful route aggregation? (Choose two)
Which option lists the cloud service models?
Which two functions are performed at the core layer of the three-layer hierarchical network design model? (Choose two).
A network has several routers running IS-IS L1L2 mode on the same Ethernet segment. Which action reduces to a minimum the number of IS-IS adjacencies in this segment?
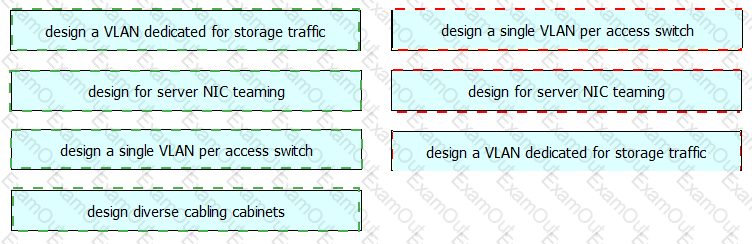
You are designing a new data center network. Drag and drop new data center requirements on the left into the appropriate design principle on the right.
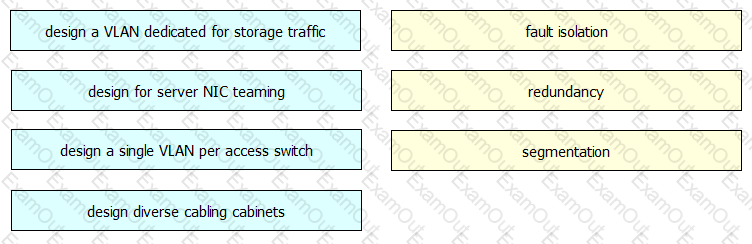
An enterprise campus is adopting a network virtualization design solution with these requirements
It must include the ability to virtualize the data plane and control plane by using VLANs and VRFs
It must maintain end-to-end logical path transport separation across the network
resources available grouped at the access edge
Which two primary models can this network virtualization design be categorized? (Choose two)
ACME Agricultural requires that access to all network devices is granted based on identify validation, and an authentication server was installed for this purpose. Currently the network team uses a list of passwords based on regions to access the internal corporate network devices. Which protocol do you recommend to ensure identify validation from the authentication server to the corporate directory?
Refer to the exhibit.

This enterprise customer wants to stream one-way video from their head office to eight branch offices using multicast. Their current service provider provides a Layer 3VPN solution and manages the CE routers, but they do not currently multicast. Which solution quickly allows this multicast traffic to go through while allowing for future scalability?