A web application is susceptible to cross-site scripting. Which two methods allow this issue to be mitigated? (Choose two.)
Refer to the exhibit.
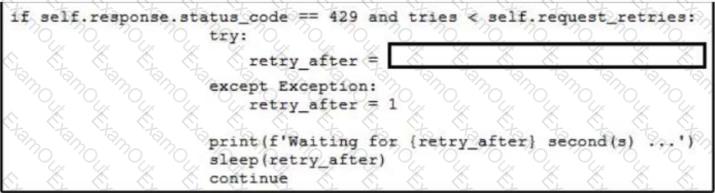
Which line of code needs to be placed on the snippet where the code is missing to provide APl rate-limiting to the requests?
A developer releases a new application for network automation of Cisco devices deployed m a local data center. The application utilizes complex design patterns such as microservices that host multiple third-party libraries and programming languages. The development must be simplified by implementing an observability-driven development lifecycle. Which two considerations must be taken to meet the requirements? (Choose two.)
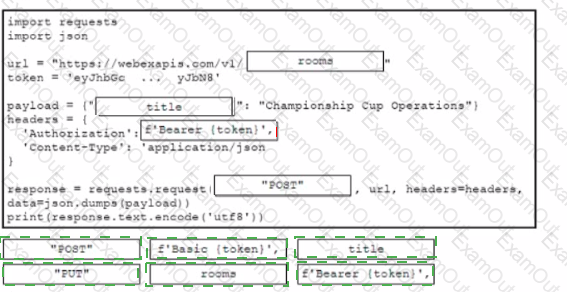
Drag and drop the code from the bottom onto the box where the code is missing to create a Webex space Not all options are used.
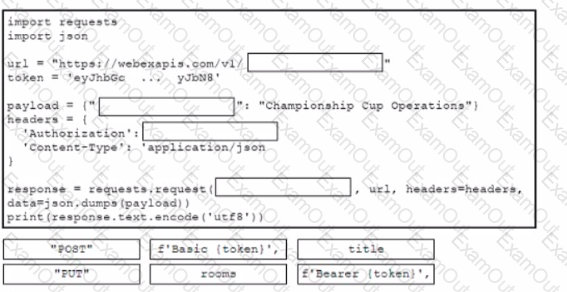
Refer to the exhibit.
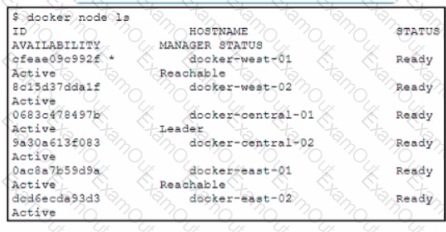
A Docker swarm cluster is configured to load balance services across data centers in three different geographical regions west central and east. The cluster has three manager nodes and three worker nodes Anew service named cisco.devnet is being deployed. The service has these design requirements
• All containers must be hosted only on nodes in the central region
• The service must run only on nodes that are ineligible for the manager role
Which approach fulfills the requirements?
An application is hosted on Google Kubernetes Engine. A new JavaScript module is created to work with the existing application. Which task is mandatory to make the code ready to deploy?
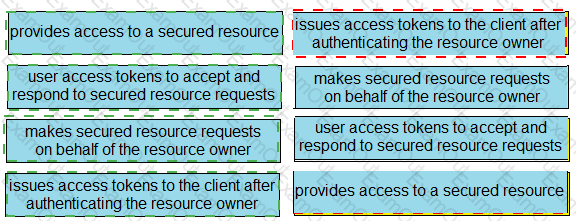
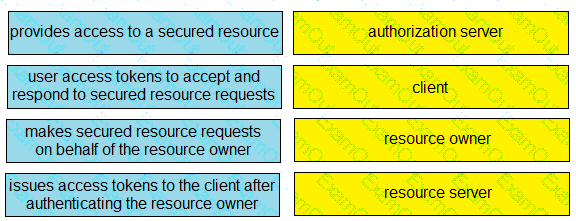
Drag and drop the descriptions from the left onto the related OAuth-defined roles on the right.
Refer to the exhibit.
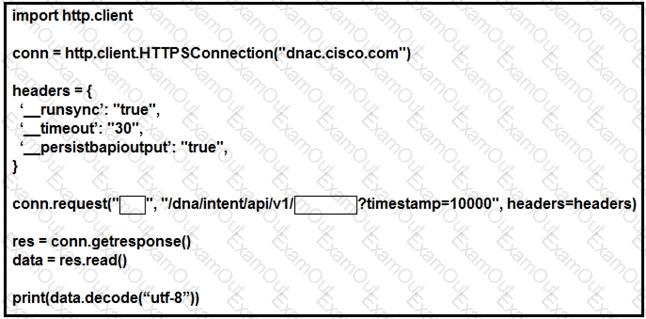
Which configuration of method and parameter retrieves the health of a laptop connected to the network from Cisco DNA Center?
What is a benefit of using model-driven telemetry?
What is a benefit of continuous testing?